Healthcare systems and the various devices associated with healthcare present a unique set of challenges for cybersecurity. Cyberattacks on healthcare centers and related spaces can result in (and have) serious consequences, such as patient data breaches, loss of life or the spread of diseases. Here we share an example.
As we move toward greater interoperability between medical devices and networks in healthcare environments, it's more important than ever that cybersecurity best practices are followed by all parties involved, especially device manufacturers, they are responsible for ensuring that adequate controls exist before products are used by customers, patients, or anyone else...
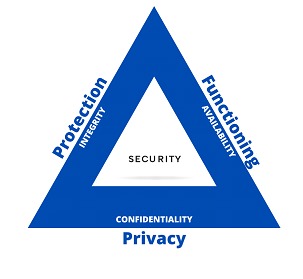
En este punto, aunque el objetivo final siempre será proteger a las personas en alguno de sus aspectos, podemos hacer algunas divisiones:
At this point, although the final objective will always be to protect people in some of its aspects, we can make some divisions:
⦁ Protecting the patient's health and physical safety.
These aspects are mostly in the hands of the developers and manufacturers of devices, sensors and all kinds of medical elements that interface between people and machines. Some questions we can ask ourselves:
Can an AED (Automated External Defibrillator) administer a huge load that causes us irreversible damage? Can a simple x-ray become a harmful dose of radiation? At this point we can say that we are interested in the integrity, in short, that the systems do what they have to do.
⦁ Ensure the operation of the service
In medical systems, the availability is one of the most determining factors, in a system that stops working within the metallurgical industry, for example, the operation of a series of melting furnaces, which would immobilize a production line (you can read here more about Industry 4.0). In healthcare environments, on the other hand, availability may be directly linked to a life.
Could an artificial respirator be affected by a code injection?What happens if the emergency room admission system is infected with ransomware?
The RTO (Recovery Time Objective) here should be practically 0.
⦁ Protect data privacy
It is clear that medical environments are spaces where personal information is one of the main assets, from the point of view of confidentiality, here we find records that contain details about people's health, about their treatments, health conditions, images and medical studies, a whole set of highly sensitive elements.
Where do we store records of prescription drugs?
Who has access to a patient's medical history and from where?
A person's medical history can be bottled up in a virtual machine on an out-of-date ESXi
MedTech
Medical devices play an important role in the operations of health centers and, although we do not want to, they provide a back door to directly access patients (to their data, or to themselves, which is much worse). We can begin to draw some similarities to an OT environment.
We find a universe of technology in constant development, such as:
⦁ Vital signs monitors
⦁ Electrocardiography systems (ECG)
⦁ Imaging systems (CT scans / MRIs / Ultrasounds)
⦁ Infusion systems
⦁ Anesthesia systems
⦁ Ventilation systems (e.g. respirators)
⦁ Patient monitoring systems
⦁ Radiation measurement systems
These devices can (and usually are) connected to a network, this is where the attack surface increases, they share information with other devices and information systems, such as "Electronic Health Information Systems" or "Electronic Health Record" (EHR). The standardized connectivity (ethernet for example) allows better interoperability between the devices, this adds value to health professionals and the management of the different functions of the devices.
A compromised medical device can have serious consequences for patients, physicians and managers. A cyber attacker could access a medical device and modify monitored patient data or change treatment settings, resulting in serious consequences for the patient's health. Patient data could also be stolen and used for malicious purposes, this could cause financial (even long-term emotional) damage to the patient.
Only as a reference we can take a respiratory monitor (oximeter) from the Medtronic firm and analyze the different types of interconnection ports, we find:
⦁Serial port type DB-15 (RS-232)
⦁USB type serial port
⦁RJ-45 (Ethernet) port
⦁RF Antennas (WLAN)

Let's focus on the inherent vulnerabilities of serial-type protocols for the first two connectors:
⦁The transmitted data can be easily read if there is no encryption
⦁The data can to be manipulated which can lead to falsified records
⦁This type of connection can be vulnerable to malicious inyección de código malicioso
⦁Exposure, if the connection is open anyone could connect to a device
On the other hand, regarding LAN and WLAN connections, for now we only share the following warning from the manufacturer:“When connecting the device to any other equipment, make sure it is virus-free””
We put most of our trust on all the other components of the network, the physical security and the security of the operating systems involved.
Different stakeholders from a cybersecurity perspective
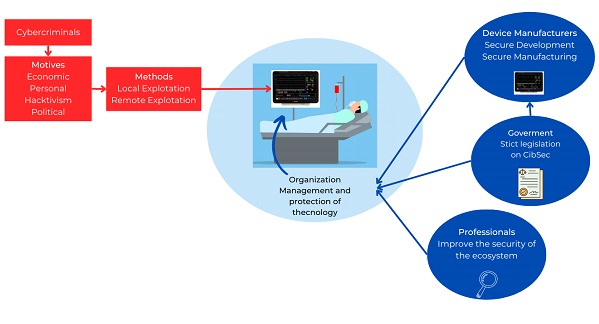
A simple matter of cybersecurity
These types of systems are still an environment that combines IT/OT, with particularities that we can consider critical. The different devices together with the patients only form one part, the other part is made up of a set of networks, configurations, servers, databases and data, an entire IT environment. Many of these environments still lack sufficient controls (such as encryption, which prevents something as trivial as unauthorized personnel from accessing sensitive data).
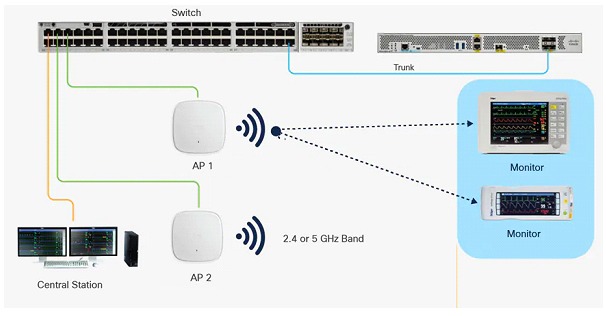
Many medical devices use old technology that was not built with security in mind, and these often lack sufficient security measures to prevent breaches, as we saw before, but on top of this, the entire environment falls short of expected standards for this type of infrastructure. Many hospitals or health centers have pending measures such as keeping their operating systems up to date, implementing multi-factor authentication, and using storage encryption to prevent cybercriminals from using the device's memory card or hard drive as a network entry point. Some for budget reasons, some for lack of knowledge.
In addition to the standards and regulatory frameworks in the technological field, we have different standards for this industry that to a greater or lesser extent offer some guarantees.
It is important to note that meeting these requirements is the responsibility of healthcare professionals and healthcare organizations, some of these frameworks are mandatory, and there are civil and criminal penalties for non-compliance. Among some of these, we can find:
HIPAA
It is a US federal law that establishes national standards to protect the privacy and security of individuals' personal health information. Applies to health information exchange organizations and most health care providers.
ISO27799
It is an international standard that establishes guidelines for the management of information security in medical care. It provides a framework for implementing information security measures to protect the privacy and confidentiality of patient data in addition to improving the quality of medical care.
ISO14971
It is a standard that establishes a process for the identification, evaluation and management of the risks associated with medical devices throughout their life cycle. Its aim is to ensure that the risks associated with medical devices are managed effectively, minimizing potential harm to patients and users.
Dentro de los requisitos técnicos de estos marcos, podemos listar algunos reconocidos en todos los entornos informáticos:
⦁ Authentication :
Verification of the user's identity before allowing access to medical information.
⦁ Authorization:
Explicit permissions for access to medical information based on a need to know.
⦁ Encryption :
Encryption of medical information during transmission and storage to protect it from loss or theft.
⦁ Backups :
Backup plan to ensure that medical information is not lost in the event of natural or technological disasters.
⦁ Intrusion detection :
Intrusion detection systems to identify and respond to potential threats to information security.
⦁ Risk assessment :
Periodic evaluation of the risks to the privacy and security of medical information.
⦁ Password management :
Policies and procedures for secure password management.
⦁ Security monitoring :
Continuous monitoring of the security of medical information to detect possible vulnerabilities.
⦁ Mobile device protection :
Measures to protect medical information on mobile devices, such as smartphones and tablets.
⦁ Activity log :
Record of activities related to medical information to facilitate auditing and monitoring.
Some conclusions
Organizations that use and develop medical technology implement robust security measures in their devices (or should do so), although maintaining that level of security is complex to sustain over time and depending on the use of each device.
In the field of architecture, security is increasingly taking center stage 'from design to implementation' (to prevent security breaches and protect patient information), but it is clear that it is still not enough to cover the risk and exposure that organizations face today.
It is also essential for healthcare centers to implement (but above all maintain) cybersecurity policies and procedures to minimize the risk of attacks and ensure the safety of their patients.
In future publications, we will explore these standards and protective measures.