EEPROM 1-Wire Protected with SHA-1 discovery & Low-Cost Side-Channel Attack
 DS28E01 with a size of 0.6x0.6 cm
DS28E01 with a size of 0.6x0.6 cm
In an early stage of analysis of our PCBs (Printed Circuit Board), during the reversing process we usually list the components that make them up, but in some cases these components are found in the peripherals of the products to be analyzed. In this post, we are going to talk about the basic principles of cryptography and we will propose a theoretical framework to carry out practices and techniques that attack these components at a considerably low cost compared to those of the current market.
This is the case of DS28E01, an EEPROM memory distributed by Maxim Integrated that according to its data sheet was created for configuration and monitoring print cartridges in professional environments (both 3d and conventional), Authentication and calibration of medical sensors and to implement intellectual property protection systems. Also, although to a lesser extent, they can be seen in industrial environments and in tokens for digital signatures.
But what makes it different from the rest of the best-known EEPROMS is not only its encapsulation, which at first glance shows only two connectors corresponding to the 1-wire protocol, but also its security based on cryptographic algorithms.
As a general description, the manufacturer assures us:
“The DS28E01-100 combines 1024 bits of EEPROM with challenge-and-response authentication security implemented with the ISO/IEC 10118-3 Secure Hash Algorithm (SHA-1). The 1024-bit EEPROM array is configured as four pages of 256 bits with a 64-bit scratchpad to perform write operations. All memory pages can be write-protected, and one page can be put in EPROM-emulation mode, where bits can only be changed from a 1 to a 0 state. Each DS28E01-100 has its own guaranteed unique 64-bit ROM registration number that is factory-lasered into the chip. The DS28E01- 100 communicates over the single-contact 1-Wire® bus. The communication follows the standard 1-Wire protocol with the registration number acting as the node address in the case of a multi device 1-Wire network”
 DS28E01 belongs to an accessory of https://www.3dsystems.com/3d-printers/plastic , Unfortunately, during the extraction process the encapsulation was damaged, but continues to function correctly.
1-wire connection
DS28E01 belongs to an accessory of https://www.3dsystems.com/3d-printers/plastic , Unfortunately, during the extraction process the encapsulation was damaged, but continues to function correctly.
1-wire connection
Present
Counterfeiting of electronic products has become a huge problem for manufacturers. According to a report by the United Nations Office on Drugs and Crime, the counterfeit goods market was worth $250 billion more than a decade ago. Approximately 8% of all counterfeit products are Electric equipment or IT (based on the number of seizures of counterfeits at European borders in 2008). Hence, protecting products against "cloning" is a necessity for a manufacturer today.
Devices consisting of various components of varying complexity appear to be a profitable target for counterfeiting in particular: For example, although printers are relatively different between makes and models, there is a huge variety of compatible ink cartridges for all of them, presumably because cartridges are easy to produce and are in constant demand. The same is true for similar low-cost items such as mobile phone accessories (e.g. chargers etc.) and also for more expensive equipment such as medical sensors or network expansion modules for network infrastructures.
(Chair for Embedded Security, Prof. Dr.-Ing. Christof Paar, Ruhr-University Bochum, Germany.)
To guarantee the authenticity of these components, an additional integrated circuit like the one we described at the beginning of the post is placed in the device to be authenticated. The host (for example, a printer, mobile phone, or medical device) then runs an authentication protocol with the IC (Integrated Circuit) to verify that the component (for example, an ink cartridge, sensor, or a battery) is authentic. Common cryptographic algorithms in this area range from AES and SHA-1 over SHA-2 to Elliptic Curve Cryptography (ECC). Typically, authentication is one-sided, that is, the device is authentic before the host, but not vice versa.
Often being relatively low cost products, devices protected with such integrated circuits are readily available for potential detailed analysis.
SHA-1
In cryptography, it is known as SHA-1 (Secure Hash Algorithm-1, translated as Secure Hash Algorithm) to the cryptographic hash function that takes an input and produces a fixed 160-bit value as a hash message. This hash is normally represented as a 40-digit long hexadecimal number. SHA-1 is based on principles similar to those used by MIT Professor Ronald L. Rivest in the design of the MD4 and MD5 message digest algorithms.
Examples:
- SHA1("base") = 1405df66cbe219b0bf6355bc3d60361a8376b6b4
- SHA1("cuatro") = a37e3bea6f0b7562991701d9211834b3f315ab84
The SHA family is a system of cryptographic hash functions developed by the US National Security Agency and published by the National Institute of Standards and Technology (NIST). The first of these functions was published in 1993 under the title Secure Hash Standard, FIPS PUB 180, and is officially known as SHA. This function has been popularized as SHA-0, to avoid confusion with its successors. Two years after the development of the first function, the first successor to SHA was published, which received the name SHA-1. Four more variants have since been published under the name SHA-2; the differences between them are based on a somewhat modified design and increased output ranges: these are SHA-224, SHA-256, SHA-384, and SHA-512. SHA-3 is the latest member of the family, published by NIST in August 2015; its algorithm generates hashes of the same length as SHA-2 by using a different method based on the Keccak algorithm.
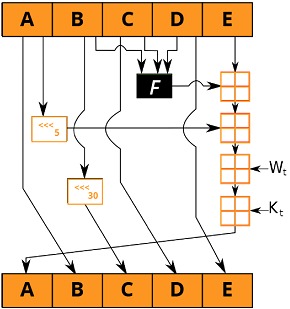
SHA-1 processing consists of these 5 steps:
- Padding bits are added to the input message. This operation consists of adding a "1" followed by the "0" that are necessary to complete the block 512 bit. This padding serves to hide the structure and length of the content, making it difficult to attack.
- A 64-bit block is added. That represents the length of the original message before being padded.
- Temporary memory is initialized, which consists of 160 bits and whose purpose is to store the intermediate and final results of the dispersion function. It consists of 5 registers (A, B, C, D, E) of 32 bits each.
- The message is processed in blocks of 512 bits. Each one goes through a module consisting of 4 rounds of 20 processing steps each. The rounds have a similar structure, with the exception that each occupies a primitive logic function differently.
- Once all the 512-bit blocks are processed, the message digest is the 160 bits of output of the last block.
SHA-1 differs from SHA-0 only by a single bitwise rotation in the message scheduling of its compression function. This was done to fix a flaw in the original algorithm that reduced its cryptographic security.
The resistance of the SHA-1 algorithm was compromised in 2005, after algorithms like MD5 were seriously compromised in 2004 by a team of Chinese researchers. The team, consisting of Xiaoyun Wang, Yiqun Lisa Yin, and Hongbo Yu, demonstrated its ability to break SHA-1 algorithms in at least 269 operations, nearly 2,000 times faster than a brute force attack, which would require 280 operations. The most recent attacks against SHA-1 have managed to weaken it to 263, which, while still a high number of operations, is well within the limits of current computational capabilities, so it should be phased out by December 31, 2030, in favor of the more secure SHA-2 and SHA-3 algorithm groups.
"We recommend that anyone who relies on SHA-1 for security migrate to SHA-2 or SHA-3 as soon as possible," said Chris Celi, NIST computer scientist.
Side-Channel Attack
Side-Channel Attacks (attacks by side channel or SCA) are non-invasive attacks that are based on attacking the implementation of a cryptographic algorithm instead of analyzing its statistical or mathematical weakness. These attacks take advantage of information leaks physically from various sources or indirect channels, such as the electrical consumption of the device to be analyzed, the time it takes to perform a calculation or electromagnetic radiation (EM), which is what we are going to focus on in this post.
These channels are called "secondary channels." The information contained in the parameters of the secondary channels depend on the intermediate values calculated during the execution of a crypto-algorithm, and are correlated with the inputs and the secret key of the encryption.
The secret key could be effectively extracted by observing and analyzing the parameters of the side/sub channels with corresponding laboratory equipment by subjecting the obtained reading results to various mathematical functions in a relatively short investigation time.
The Georgia Tech team concluded that it would take an attacker up to 3,579 times longer to figure out the encryption key for their circuit, compared with a standard model. PHOTO: GEORGIA INSTITUTE OF TECHNOLOGY
As we mentioned, the electromagnetic waves emitted by integrated circuits in operation are a parameter to be measured. These EM are defined as synchronized oscillations of electric and magnetic fields that propagate at the speed of light through a vacuum. In general, there are two types of EM signals:
Intentional emissions
Intentional electromagnetic emissions are the result of current flows that are applied to cause the device to emit an electromagnetic response. These current flows usually occur in the form of short bursts that cause a high power emanation that would be easily observable over a whole band of frequencies. Often the applied current flow is directed to a higher frequency band to quickly capture the response due to noise and other interfering emissions in a lower frequency band. The goal of an attacker in this type of emissions is to isolate the EM response from the critical data path that is targeted. This requires a tiny and sensitive EM probe. Device delay can also help improve the quality of the captured signal.
Unintentional emissions
When an attacker begins analysis, focusing on unintended emissions can help identify critical paths and acquire their data values. The greater complexity and smaller size of modern integrated circuits give rise to electrical and electromagnetic coupling between components, which is an uncontrolled phenomenon that can generate a compromising signal. These components can act as modulators; they generate a carrier signal that can be intercepted and post-processed to acquire the transported data.
The security of a device against SCAs must be evaluated using an appropriate metric. There are different methods to measure the level of protection of the attacked device. These methods assess the difficulty of successfully performing an SCA and the time required to successfully extract critical information from the device.
Test Vector Leak Assessment (TVLA) is a common testing method to measure how easy it is to detect any data leaks in a device, it is done by applying a predefined set of test inputs, detecting leaks and evaluating the capability to extract significant information from the traces (EM side-channel Traces (t)).
This is based on the Welch test, which is used to test the hypothesis that two Populations have equal means when two samples have unequal variance and unequal sample size. In the side channel evaluation process, n measurements are collected while the device under the test operates with a known secret key. The n measurements are submitted to analysis, and it is obtained if the two groups are distinguishable or not and if the application has a high probability of leaking information.
Another method used to measure the vulnerability of side channels is to apply the analysis of the success rate of successful attacks (i.e. the key is obtained through the attack) divided by the total number of attacks carried out, where the rate maximum of 100% means that the device is successfully attacked every time a side channel scan is applied, and the minimum of 0%, which means that the device is protected against all attacks. This evaluation can also reflect the time required for the attacker to extract critical information from the device.
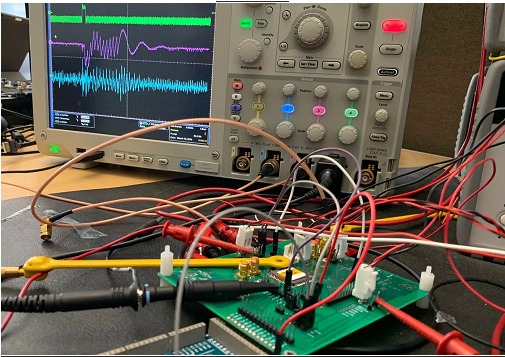
Next we will see a reference scheme with the necessary tools to carry out these practices:
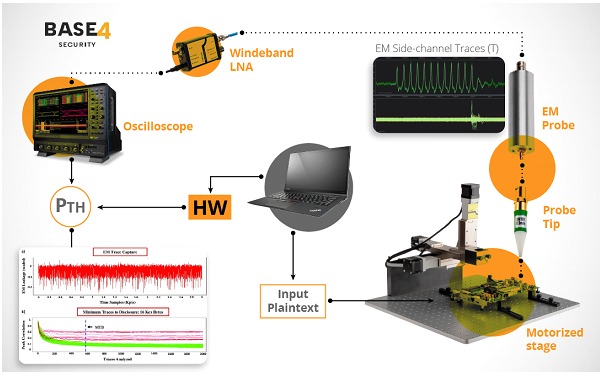 The representation of this graphic was recreated with products of https://getquote.riscure.com/en/quote/2109316/side-channel-analysis-premium.htm
The representation of this graphic was recreated with products of https://getquote.riscure.com/en/quote/2109316/side-channel-analysis-premium.htm
EM signals usually propagate by conduction and radiation; As we can see in the graph, these signals can be intercepted by sensors, such as a near-field probe or an antenna. This is mounted on an XYZ table, which is nothing more than a platform with software-controlled Cartesian movements that allow us to position our EM-sensors. Prove to the millimeter on the IC (Integrated Circuit) to be analyzed, since these (in their encapsulations) present more and less vulnerable areas against EM readings. The use of these sensors allows the amplified EM signal to be transferred to a current signal, which is post-processed to eliminate noise and limit the frequency band to apply the EM analysis. The quality of the received signal is usually improved if the sensor used is shielded from unwanted frequency bands or other electromagnetic interference.
Signal post-processing may include filtering of frequency bands that are not related to the critical data band, which requires prior knowledge of the frequency band containing the information.
To gain that knowledge, a spectrum analyzer or oscilloscope (readability defines its cost) is often used to identify carrier signals and noise; a post-processing filter can then be set Alone to allow the passage of critical information.

Analysis Types
⦁ Simple Electromagnetic Analysis (SEMA)
In SEMA, a single time-domain trace is obtained to observe, and gain insight into, the device directly. The attack alone is valid when there is prior knowledge about the architecture of the device, or the security policy, applied. The main objective of SEMA is to obtain critical information by visual inspection of the EM signal trace, where a sequence of transitions at system startup can include information about the secret key used to encrypt/decrypt data. The use of SEMA is usually the first step of the EM SCA, where the information needed to carry out a more detailed analysis using DEMA can be observed.
⦁ Differential Electromagnetic Analysis (DEMA)
DEMA is applied to the device to exploit information that cannot be observed visually. DEMA generally uses a self-referencing approach, which compares the analyzed signal with an equivalent in a different area of the device (spatial referencing), or at a different time (temporal referencing). This analysis does not require extensive knowledge about the attacked device; most of the information can be exploited by obtaining different forms of EM signals at different places and times. DEMA analysis can help identify functional and structural details of the target device. You can also trace the flow of a process and determine how a signal propagates within the device. These DEMA details can help reverse engineer the device, or give the reverse engineer the ability to physically disable the system's security policy.
⦁ Correlational Electromagnetic Analysis (CEMA)
In CEMA, EM measurements are taken while a cryptographic algorithm is running on the target device (each measurement is known as a trace), and these traces are correlated with a leakage model, such as the Hamming or Hamming distance of the data. At a specific point in an algorithm, under the assumption of a subset of the secret key. In a successful attack, the hypothesis that gives rise to the highest correlation corresponds to the secret key. Due to the divide-and-conquer nature of side-channel analysis, the cost of performing an SCA attack is linear in key size, rather than exponential, as in brute force or other cryptanalysis methods.
Unfortunately, for projects or small teams, the costs of these implementations, as we see in the table, can be high, but there are several investigations that document alternatives at lower cost and with successful results.
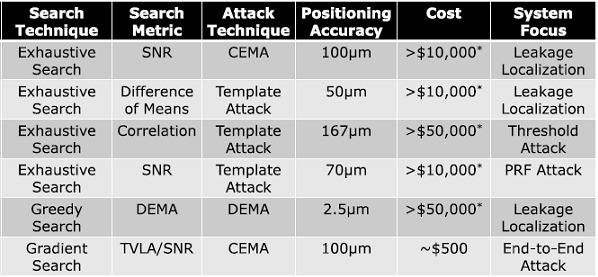
Low-Cost Tools for SCA
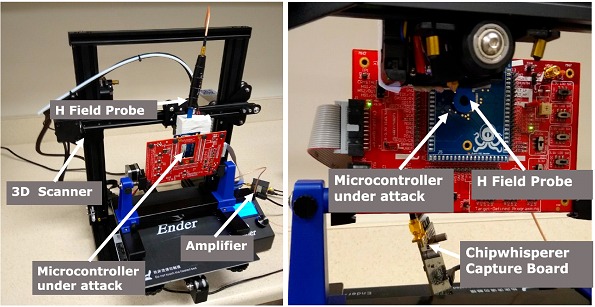
A fully automated system is proposed to efficiently scan a cryptographic IC capable of performing the analyzes seen above. The entire attack system is extremely low cost, because a 3D printer was adapted as a scanner Ender-3 for $200 compared to EM polling stations Risks Available on the market for > $50,000. The system achieves a spatial resolution of 100µm, and has a scan range of 220mm x 220mm, and is easily replicable. As a probe (EM-Probe), the tekbox TBPS0 kit is used, a Tekbox TWBA2 as an amplifier and finally a Chipwhisperer for connection to the target (the CW309T-XMEGA mounted on the 308 UFO Target board) next to a PC. Resulting in a complete setup for $630, just over 1% of a commercial set.
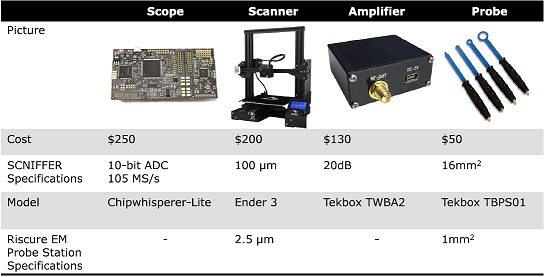
To manipulate the probe, the Ender-3 3D printer uses its stock firmware. This model has a minimum step size of 0.1mm and can be controlled via a connection series USB which makes interconnection much easier. It has a maximum speed of movement of 180 mm/s, with a printing area of 220mm x 220mm x 250mm. The firmware is open source and well documented, and the X axis carriage can be adapted to easily mount the probe and target plate.
The system is capable of performing a 30 x 30 matrix scan of the chip in 15 minutes, and a breadth scan in 75 minutes.
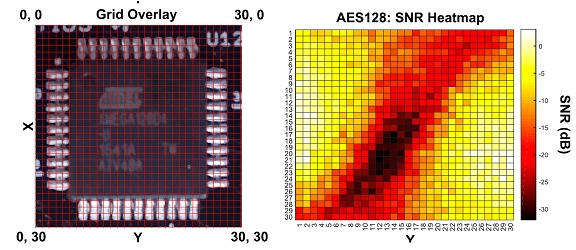
The resolution of the probe matches the resolution of the scanner, allowing for heatmaps as seen in the images, and the Chipwhisperer is capable of capturing enough leak information for the target devices, giving excellent results at low cost.
Conclusion
Now that we know the basic principles of some encryption algorithms and the SCA theory, we can return to the topic of the post. What about our DS28E01? According to David Oswald's research from The University of Birmingham, UK, where tests were performed on DS28E01 and DS2432, two successful key recovery attacks were achieved. The methods allow the complete extraction of the 64-bit secret key in approximately 40 minutes, for the acquisition of traces the SCA techniques used have relatively low requirements (sampling frequency of 125 MSPS) and the complexity of the traces (1,800 and 1,200 traces, respectively). ). Therefore, it is conceivable that attacks could also be carried out with low-cost tools such as those mentioned above.
3,000 traces each for a fixed and known secret were recorded, using evenly distributed random challenges. CEMA analysis was then performed for various intermediate values and leakage models.
Experimentally it was verified that the leakage of both devices follows the Hamming weight (HD) between the SHA-1 state registers. Therefore, SCAs can pose a serious problem for all manufacturing companies, even if the devices to be tested include a solution to provide some protection against counterfeiting.
One way to adequately protect against demonstrated attacks may be as follows:
It must be ensured that the same secrets do not exist throughout the implementation (the same ones stored in all distributed ICs) and that there is secure diversification of keys (e.g. based on the UID of the IC). Otherwise, an attack on a single device would make all the others insecure. Note that the counterparty on the host must also be protected, especially if you store a diversification key for the entire system. Checking the UID (and using it for key diversification) on the host also ensures that an adversary cannot use a real DS28E01/DS2432 IC for a cloned product simply by copying the recovered secret and memory contents. To breach this protection, a custom emulator would have to be created, for example using a custom microcontroller or ASIC, this would increase the complexity and cost of counterfeiting, possibly to the point that cloning is no longer profitable.
In the long term, the CIs discussed in this article should include side-channel countermeasures to at least avoid low-cost SCA techniques and raise the bar in terms of complexity towards tracer and measurement equipment. They should adopt the common countermeasures (eg timing randomization, masking, etc.) in each case of product authentication.
Maxim Integrated acknowledged the results and is currently studying ways to mitigate the security issues.
References
- David Oswald, “Side-Channel Attacks on SHA-1-based Product Authentication ICs”, The University of Birmingham, UK.
- NIST, “SECURE HASH STANDARD” , Federal Information Processing Standards Publication 180-2, 2002 August 1.
- HanSeop Lim , JongHyeok Lee and Dong-Guk Han, “Novel Fault Injection Attack without Artificial Trigger” Seoul 02707, Korea.
- Swarup Bhunia, Mark Tehranipoor. “Hardware Security a hands-on learning approach” Cambridge, MA 02139, United States.
- Debayan Das, Mayukh Nath, Baibhab Chatterjee, Santosh Ghosh, Shreyas Sen “STELLAR: A Generic EM Side-Channel Attack Protection through Ground-Up Root-cause Analysis” School of Electrical and Computer Engineering, Purdue University, USA and Intel Labs, Hillsboro, Oregon, USA.
- William Unger, Liljana Babinkostova, Mike Borowczak, Robert Erbes, Aparna Srinath “TVLA, Correlation Power Analysis and Side-Channel Leakage Assessment Metrics“.
- Josef Danial, Debian Das, Santosh Ghosh, Arijit Raychowdhury, Shreyas Sen, “SCNIFFER: Low-Cost, Automated, Efficient Electromagnetic Side-Channel Sniffing” School of Electrical and Computer Engineering, Purdue University, West Lafayette, IN 47906, USA.
- Pieter Robyns, Peter Quax and Wim Lamotte “Improving CEMA using Correlation Optimization” Hasselt University - tUL, Expertise center for Digital Media Martelarenlaan 42, 3500 Hasselt, Belgium.
- E. Tena-Sánchez, I. Durán, S. Canas and A. J. Acosta ”Vulnerability Evaluation and Secure Design Methodology of Cryptohardware for ASIC-embedded Secure Applications to Prevent Side-Channel Attacks” Instituto de Microelectrónica de Sevilla.
Otras lecturas de interés:
- Monjur Alam, Haider Adnan Khan, Moumita Dey, Nishith Sinha, Robert Callan,Alenka Zajic, and Milos Prvulovic, Georgia Tech, “One&Done: A Single-Decryption EM-Based Attack on OpenSSL’s Constant-Time Blinded RSA” August 15–17, 2018
- Baltimore, MD, USA.
- Gregor Haas, Aydin Aysu “Apple vs. EMA: Electromagnetic Side Channel Attacks on Apple CoreCrypto“ North Carolina State University Raleigh, NC, USA.
- Maxim Integrated, “DS28E01-100 1Kb Protected 1-Wire EEPROM with SHA-1 Engine DataSheet”
- Realize, “Espressif ESP32: Glitching The OTP Data Transfer” Friday, Mar 10, 2023.
- https://spectrum.ieee.org/a-very-noisy-signal-intel-circuit-squashes-sidechannel-sniffing
- https://www.techexplorist.com/threat-hardware-trojan-horses-bigger-we-thought/43160/
- https://www.ledger.com/introducing-rainbow-donjons-side-channel-analysis-simulation-tool
- https://statologos.com/prueba-t-de-welchs/










