Decanting cyber threats for 2023
On this occasion, let's take innovation in cybersecurity as a starting point to understand the possible focuses on which we will see greater attention in the coming years. It is clear that the improvements we are making in protection are (unwittingly and unavoidably) laying paths along which cybercriminals are finding their way.
New approaches, old tricks
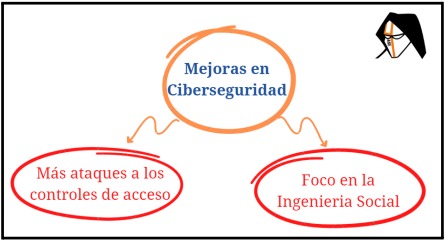
Our focus on protection based on more effective models such as Zero Trust focuses efforts and reduces the attacker's options for dealing with the identity and those behind it.

Why would an attacker make use of Zero Day exploits (acquired on the darkweb at a very high cost) if they can use social engineering techniques to capture a session cookie? Of course we will always find cases where the "attacker's business" allows or requires this kind of acquisition, but in the meantime efforts will be focused on access control systems, different types of MFA attacks, social engineering techniques adapted to new technologies. As a combination of these fields we can think, for example, of the application of Artificial Intelligence and Deep Fakes as a tool to facilitate deception, disinformation campaigns and even as a method to breach facial recognition controls.
Old environments, new approaches
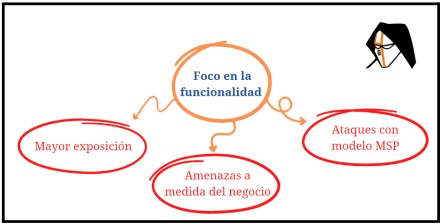
For decades now, technologies have met with industrial processes of all sizes, from assembly line automation in the automotive field, to control in hydroelectric power plants, to the implementation of technologies in the healthcare field. It is also recognized the integration with the real world that we have managed to embrace with the world of IOT, where we connect to the network from our home appliances.
to small space satellites. These technologies, often focused on their function (and not on their protection), have left us with an inherently insecure ecosystem. Addressing the protection of these devices (and new ones, of course) will be fundamental to reduce exposure (the attack surface of each environment). These devices are already a focus of interest for cybercriminals, not only at the organizational level, but also from a geopolitical point of view. During the last year, new waves of hacktivists have been recognized in the wake of the Russia-Ukraine conflict, giving specific attention to cyber operations and behind attacks with clearly destructive objectives as the main component.
Within this scenario we can also observe that the supply chain will have special value in the execution of attacks, a proverb says "To get rid of the seeds, pull up the roots", this is how the attackers have been able to improve the understanding of the functioning of the services of their targets, applying their techniques on the different suppliers that are fundamental for the "correctly protected" organization. A few years ago, we began to understand the need for a more secure ecosystem, from the "front door to the back door".
Looking at the attackers themselves, it is clear that they have increased their capabilities, not only using 0-day exploits, but offering themselves as service providers, Hacker as-a-service is a business model that has grown since 2021. A growth in the number of attacks based on this type of platform is expected, it is no longer necessary to be an expert to perform an expert attack.
New environments, we lose focus
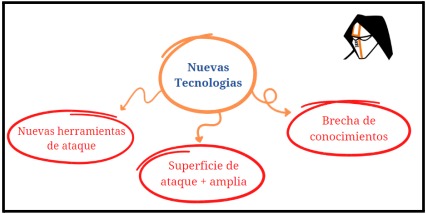
As it has been historically, new technologies bring new business, new business brings new threats, this is how WEB3, the entire Blockchain ecosystem and decentralized systems must also be observed from "security lenses".
In this regard, we can place, for example, the use of artificial intelligence algorithms, as a threat we can identify a manipulation of these algorithms based on "bad training", which would subsequently allow the algorithm to make decisions based on premises fabricated by a malicious actor. We can also take these technologies, from a cybercriminal's point of view, and use them as a tool for the creation and distribution of disinformation or false content, the collection of sensitive data, or the application on the exploitation stage in any attack.
These new technologies expand the attack surface significantly, giving rise to new threats about which we do not yet have full knowledge. Training and the definition of protection criteria for these technologies from their design is essential to face these times.
At this point we can also identify the growing lack of cybersecurity professionals in different areas, this current situation combined with the massive use of new technologies results in a gap between the knowledge that organizations have and the needs to be covered, this gap (wider of course in less mature organizations in terms of cybersecurity) will be a target for cybercriminals. We will see attack vectors specifically designed to exploit these gaps.
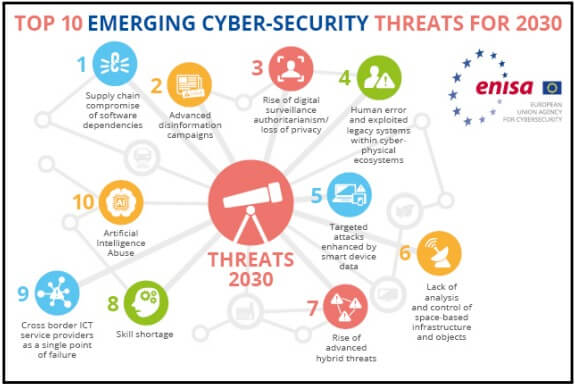
Finally, we dare to go a little further and do a little futurology, looking at the TOP 10 emerging threats for 2030 proposed by ENISA: