It's not always clear 'What needs to be done', and 'What are the benefits' of well-implemented security. These benefits manifest as the absence of 'negative events' rather than the addition of positive events, making it sometimes hard to have a clear vision of 'What is needed' when approaching a new technology. This might be due to cognitive biases or user comfort related to 'not stepping out of their comfort zone'. This is a clear example of the fallacy that exists when thinking of a new solution that solves problems before they occur, and then teams fall into the questioning related to no one highlighting the virtues of a system that solves problems before they happen. Indeed, nobody is surprised. We are more accustomed to solving in a reactive rather than preventive way and of course celebrating these kinds of solutions
Since everything resolved without raising alarms does not receive due recognition, there's a tendency among users to neglect these types of solutions. DevSecOps is a practice that better aligns security, engineering, and operations, infusing security throughout the DevOps lifecycle. During this brief read, we will focus on which important and simple points you can concentrate on to perhaps unlock these mechanisms of change.
About Development
• Ensuring security is part of the entire development process:
Introducing security early in development and throughout the entire cycle allows the security analyst to give their requirements the same weight as functional requirements. This involves adding security controls and processes, and of course, automating these fundamental tasks in the workflow. This enables developers to address known vulnerabilities from the start, thereby providing secure and resilient software.
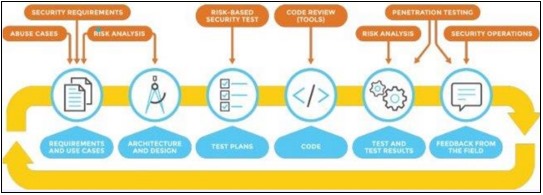
• Conducting Security Testing Throughout the Development Cycle:
We must ensure that security testing is a continuous process and an integral part of the entire application development cycle, targeting all types of applications, APIs, containers, data, processes, and microservices.
The sooner we can identify flaws, the easier it will be to correct them, but being able to identify flaws everywhere, from development to production, will ensure that you can maintain awareness of vulnerabilities, no matter where they arise.
• Monitoring Processes, Infrastructure, and Applications:
There are various data points of interest when it comes to monitoring; we collect logs not only to analyze the health of our assets but also to determine various focal points when considering what to observe and on which data point to scrutinize. Among the issues to review, we find:
• Collecting real-time intelligence allows you to make more informed decisions and apply precise compliance.
• Gathering and analyzing relevant metrics, event logs, and machine data to gain real-time insights throughout the application lifecycle.
• Monitoring applications in production to ensure we detect new vulnerabilities and security events.
All these issues serve to seize the opportunity to solve problems early, quickly, and at minimal cost.
• Generating Actionable Alerts When Issues Arise:
This involves implementing a tool that notifies the team when there's an issue in all key focus areas, including security. It must be capable of sending actionable alerts to relevant individuals. But first, these alerts must be correctly debugged to avoid potential blindness in the monitoring team. More alerts do not mean more monitoring.

About Environments
• Secure and Monitor Your Entire Physical and Virtual Environment:
First and foremost, to ensure security, we must enumerate our most critical environments. Security must be integrated across all of these environments. Steps must be taken to secure infrastructure, including on-premises and cloud environments, networks, CI/CD pipelines, code, data, operating systems, applications, and software.
• Collect Metrics to Measure Success:
Security is an endless journey, so we must focus on resolving and continually improving to enhance all our knowledge gaps. Collect and act upon security and compliance information from on-premises and cloud environments, gathering high-value metrics to gain insights and determine the effectiveness of your security processes, thus generating iteration whenever things improve.
• Secure and Reinforce Containers:
Follow the best security practices for containers. Ensure authentication and authorization are secure. Inspect, scan, and secure the files associated with images we pull from trusted places to apply due diligence in sanitation. Use private registries like Google container registry or Red Hat’s Quay thereby creating an architecture from trusted and verified containers.
• Isolate Docker and Kubernetes Infrastructure:
Secure and isolate your containers early, often, and continuously. One apt way to do this is to segment containers using tools like Apparmor,Seccomp and SELinux. These tools allow us to create isolation layers between different applications and between applications and hosts. This reduces the host surface, thus restricting access and safeguarding it, as well as the containers located on it.

• Conduct Threat Modeling Exercises:
A threat modeling exercise identifies design flaws and components at higher risk and should afford the security team an opportunity to prioritize and address defects based on their impact. Particularly, threat modeling helps teams understand the type of assets they are protecting, levels of sensitivity, potential threats, and their impact.
• Reinforce Cloud Deployments:
Cloud environments can provide secure infrastructure if properly implemented. Allowing the capability to deploy outside the production transition flow is nowadays one of the main dangers as it generates a false sense of systems area independence. Therefore, reviewing the teams and the individual roles and permissions we have assigned often presents a great opportunity for change.
We must grant access only to what each individual or team needs to perform their duties, imposing measures such as multifactor authentication for all critical roles.
Regarding Culture and Behaviors
• Develop a Strong Security Culture:
A robust security culture among developers, operations, and the security team is essential. Encouraging open communication channels to have strong feedback between areas is crucial. Achieving this alters the perception of our security area. In our post Design Thinking applied to cybersecurity we explore how our security area can become more empathetic when proposing changes by understanding user needs.
Besides, transferring the responsibility for security to all these teams, as opposed to the traditional approach where it was solely the security department's responsibility, adds more hands to the effort of creating a much safer ecosystem. If we manage to make security come from a place of 'yes, let's figure out how to do this securely' instead of 'no, you can't do it for security reasons,' security will shift from being an obstacle to being an enabler.
• Develop a Security as Code Culture:
Introduce a security-first mindset without impacting the agile practices developers rely on to build applications. Encourage your developers to add security into the code as they build applications, always making secure actions the easiest actions whenever possible.
• Provide Training and Tools to Developers:
Ensure that developers have the information, support, and tools they need to perform their tasks efficiently. Also, foster knowledge sharing and establish a decision-making process among different departments to promote team autonomy.
Regarding APIs
• Secure Your APIs
APIs enable interaction and data exchange between applications and are, therefore, more exposed and prone to security risks. Secure all APIs that the company consumes, as well as those it exposes to the public. Use encryption correctly to protect information from requests in transit while limiting the amount of information associated with API error messages.
• Authenticate and Authorize API Users:
Use API identifiers and keys to identify and authenticate users, devices, or applications. Employ an access control framework like OAuth or SAMLv2 to control which APIs authenticated users or specific API keys can access.
In one of our posts we detail with more specificity all potential recommendations concerning the world of APIs.
Regarding Coding
• Security in the Code in Your Applications:
Creating secure code from the onset of development through application deployment can be a challenging task without the help of those who know. Ensure that security is integrated into the code rather than added as an afterthought; this can be easily achieved by involving security analysts from moment zero. Also, keep code and deployments as simple as possible to avoid complexities that could compromise security. Implement processes and best practices that make it easy and straightforward for developers to make secure decisions.
• Continually Review Code at Every Stage
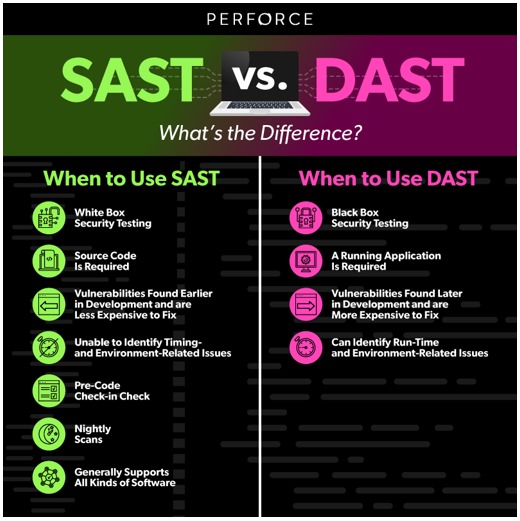
Review code and standards at each stage to ensure they adhere to security best practices. Use SAST and DAST to analyze the code and other automatic tools to track dependencies and scan all third-party and open-source code. Perform checks at various times associated with code construction—pre-commit time, commit time, build time, test time, and deployment time in our Continuous Integration and Continuous Deployment (CI/CD) channel."
• Introducing Chaos into the Comfort Zone
Utilize chaos engineering to test how prepared your systems are to respond to security threats in unfamiliar operational environments. Execute scripts to randomly shut down server instances, arbitrarily take down containers, disrupt some services, or create unexpected interruptions in applications and infrastructure. This aids teams in providing a moving defense that safeguards your systems across a broad array of conditions and ensures that something unexpected doesn’t cause everything to crumble.
A success model related to this methodology is the Chaos Monkey model that Netflix applies to its security architecture.

• Maintain an Inventory of Your Applications and Components
Create and maintain an up-to-date inventory of your application assets, gaining visibility into what's being deployed and what your organization is using. Keeping an updated inventory will help you uncover new security insights and prevent being caught off-guard when something insecure is deployed or security vulnerabilities are discovered in something old and forgotten.
• Scan and Secure Your Open Source and Third-Party Components
Stay abreast of your open source and third-party dependencies. Ensure they are always up-to-date and regularly check that they are not vulnerable.
• Initiate a Security Analysis Program for Your Code
Use threat modeling, penetration testing, and vulnerability testing to confirm that your code is secure. Determine the number of severe vulnerabilities and how long they persist before your team resolves them. Analyze the frequency and scope of automated testing, as well as the quantity and type of attacks on your applications.
Regarding Protection
• Use Best Security Practices and Tools
Adhere to standard best security practices. Minimize your attack surface (strengthen infrastructure and services), encrypt your data and communication channels, and filter and block malicious traffic. Conduct regular audits and celebrate when they pass, as they teach us new ways and primarily remind us of areas to focus on.
• Automate Data Policy Managements
Utilize automated policy applications to manage the lifecycle and flow of data, creating audit logs before and after any security issues.
• Use existing DevOps tools to automate some security functions. For example:
• Chef: To automate security tests
• Puppet: To assess compliance and apply security policies
• Ansible: To define and automate the best security practices, such as applying custom policies, configuring firewall rules, blocking certain users, etc.
• SaltStack: To automate security practices
Combine common tools with a continuous security monitoring platform and adjust this solution based on our availability with respect to different existing tools.
• Complement Automatic Testing with Creative Manual Testing
Automated test scripts may not be able to recognize or identify visual issues that the human eye could perceive. Additionally, a human tester will interact with the software and uncover usability or interface issues. Another challenge arises when automated test scripts contain errors or faults that produce false negative or positive results. Manual checking should intervene as soon as possible to avoid dragging a future error.
• Follow Best Post-Production Protection Practices:
Automate scanning and gather application-level metrics when deploying it. In this case, we can use a tool like Chef to automate configuration management, as well as runtime environment provisioning.
• Minimize the Attack Surface
Integrate protective and detection measures into the architecture to limit your attack surface and reduce exposure to internal and external threats. Focusing on high-risk areas, such as web forms, code exposed to the internet, access control, session management code, data from external sources, and other entry points interfacing with external networks. Essentially, our crown jewels.
• Keep Security Tools Up-to-Date:
The security solutions you implement must keep pace with changes in application and infrastructure environments, as well as with your own growth. They should have the capacity to protect your system in real-time and automatically send alerts when security issues arise. If they are not updated, the results will never be perfect.
Conclusion
Considering all the points discussed, we can highlight that the most crucial aspect is to befriend the process related to the DevSecOps methodology in order to see its viability. Often, we think we are far away when, in reality, we have never stopped to analyze how much more is needed to implement this type of methodology in our company. Please share in the comments if you found these tips helpful.