In the current scenario, where the world is increasingly connected and the exchange of information occurs at a fast pace, information security needs to be inserted into everyday life as a crucial concern for people and organizations. Within a context where there is a certain level of maturity in security on the part of an organization, it is expected that Vulnerability Management is a continuous task, which aims to reduce the possible impacts that can be caused by the exploitation of these vulnerabilities within their environments. One of the sub-tasks of vulnerability management is Vulnerability Assessment. In the next few minutes of reading, you will be shown what this is, how this activity can help decrease the attack surface, the importance of conducting periodic assessments, and the role of teams in this process. In addition, we will present suggestions for commercial and open source tools that can support the conduct of these assessments
Vulnerabilities and threats
Before really getting into the subject of vulnerability assessment, it is necessary to remember the concept of vulnerability. According to the Oxford Dictionary definition, vulnerability is "the quality or state of being exposed to the possibility of being attacked or harmed, either physically or emotionally”. Bringing it into the context of technology and information security, the ISO 27000 standard points to vulnerabilities as being "weaknesses of an asset that could potentially be exploited by one or more threats." These weaknesses can be inherent to any of the variables in a technology ecosystem, such as the construction of the asset in terms of code, the processes in which the asset is embedded, the data that flows through the asset, the people who handle it, or even the lack of knowledge, training, or commitment of the people themselves, who should also be considered as valuable assets of organizations. There is a type of simulation or assessment for each type of possible vulnerability mentioned above, so it is important to say that this article will focus exclusively on technological or software/firmware vulnerability assessment, the other types of vulnerabilities are subject for another (or several other) articles.
In the image below we can fit some of the concepts presented so far. For a threat to really be a threat (funny, but true) some requirements need to be met: an actor (threat agent) with a hostile intent is needed, this actor needs to have the ability to perform a hostile action, and he finally needs an opportunity - this is where the famous vulnerability fits in.
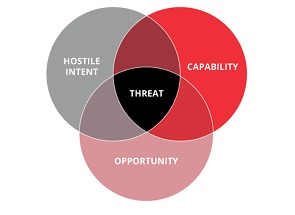
This understanding of threat is interesting to remember because one of the reasons for conducting vulnerability assessments is precisely to reduce the attack surface that exists in each technology ecosystem, i.e., the idea is to reduce the opportunities that an attacker would have to perform a hostile action by exploiting a known vulnerability.
Attack Surface
To be clear: An organization's attack surface can be quickly explained as the set of entry points or exposure points to a system that can be exploited by an attacker. These points can include servers, apps, various devices, user interfaces, and even people. The size of the attack surface is directly proportional to the probability of a malicious actor exploiting a vulnerability (of any type) and compromising the security of the ecosystem.
Defining a vulnerability assessment
In short, a vulnerability assessment is a systematic and proactive process for identifying and assessing potential vulnerabilities in systems. It is typically carried out through activities to actively examine networks, servers, applications, and devices for the aforementioned weaknesses that could be exploited by attackers. This assessment allows system administrators to identify potential threats and take corrective action to strengthen security. This can be done "manually'' using scripts in Python or Bash language, for example, but most commonly it is done by tools developed for this purpose, both commercial and open source.
Attention!
Due to the high cost of hiring commercial tools and the complexity of implementing open source tools that perform this type of activity, added to the nature of the scans that are performed by them, which can have an intrusive connotation, it is not uncommon for there to be confusion between the purpose of vulnerability assessments when compared to Red Team/Pentest activities.

Vulnerability assessment and Red Team pentests activities are complementary but distinct tasks. Both play very important roles in identifying security vulnerabilities in technologies, but they have different purposes.
The focus of vulnerability assessments is to find and document (for later remediation) vulnerabilities present in networks, systems and applications. These discoveries serve to make the organization aware of the level of exposure it is in so that it can prioritize and fix problems according to need/urgency. The tools that perform the tests and scans in general do this in an automated way and are based on a kind of database containing, usually, known vulnerabilities.
On the other hand, pentesting or Red Team activities seek to simulate real attacks to evaluate the effectiveness of an organization's security controls as a whole. In these activities known vulnerabilities can be discovered, however, the idea is that this goes beyond a common vulnerability assessment task, also finding unknown vulnerabilities, zero-days, process failures, among other discoveries.
Therefore, vulnerability assessment is usually performed by the organization's Blue Team, i.e. the team responsible for protecting the assets in the most defensive terms.
Importance of vulnerability assessment
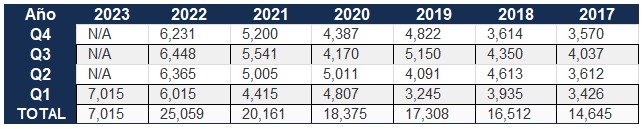
Below is a metrics table developed and updated by the CVE (Common Vulnerabilities and Exposures) project, and it shows us that in 2022 alone 25,059 new vulnerabilities were registered, and the first quarter of 2023 already shows an increase of 1000 vulnerabilities over the same period of the previous year. This data alone should be enough to convince the reader of the importance of performing this kind of testing.
Besides the absurd amount of vulnerabilities that are discovered every day, generally speaking, these assessments are important to maintain the security of the ecosystem and reduce the risks of cyber attacks caused by known vulnerabilities. An important point to be highlighted is that these assessments should be done periodically, according to the size of the organization and the complexity of each environment.
Digging a little deeper into the subject, we can list some advantages of periodic (and continuous) evaluation:
• Identification of new vulnerabilities in the environment: New vulnerabilities can be discovered at every cycle, whether in operating systems, applications, or network infrastructure.
• Compliance with security best practices: regular assessments, organizations ensure alignment with security best practices and compliance standards. The careful reader will associate this item with the major security frameworks used as international best practice guides, such as NIST CSF and special publications, CIS V8 etc. It is a practice that helps maintain an up-to-date security posture and avoid unnecessary risk exposure.
• Response to new threats: Threats are constantly evolving and new attack techniques are regularly developed. By performing periodic assessments, organizations can quickly identify new threats and adjust their defenses.
Periodization!
There is no magic recipe that presents the "correct" recurrence for vulnerability assessments and that applies to all types of organizations, because there are variables to be considered, such as: the size and purpose of the organization, the nature of the assets, the possible threats to the environment, the frequency of changes in the environment, and several others.
Best practice frameworks, in general, do not cite a specific periodicity for performing any type of security testing, so, again thinking in a general way, taking into consideration only the size of organizations, one can think of the following scheme:
• Small organizations: assessments every 6 months or annually, depending on the complexity of the environment and the amount of changes implemented.
• Medium-sized organizations: here the re-evaluation period can be a bit shorter, from 3 to 6 months to maintain a good security level and keep up with the changes and updates implemented in the systems.
• Large organizations: due to the maturity and security needs, complexity and scale of the systems involved, assessments here can be even smaller, e.g., conducting every 1-3 months may be appropriate.
Again, it is important to emphasize that these periods are only suggestions based on one of the multiple variables surrounding security testing, and should be tailored to the specific needs of each organization, considering factors such as the threat environment, asset criticality, and applicable compliance requirements.
Other important recommendations that are independent of the size of the organization:
• Testing after major changes: significant changes in the ecosystem should be followed by vulnerability assessments.
• Variety of tools:different scanning tools can bring different vulnerability identifications in their reports.
• Employee training: most vulnerabilities are the result of human error. Having an agenda of information security training at various levels, from the developer to the employee in the less technological area of the organization can help reduce risks.
• Constant updating: Keeping the ecosystem up-to-date is essential to avoid some problems.
The steps for a good security assessment
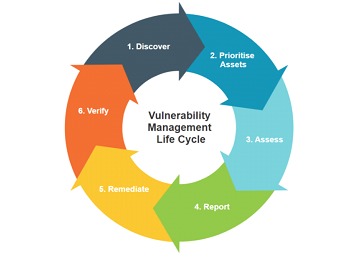
The NIST (National Institute of Standards and Technology) special publication 800-115 "Technical Guide to Information Security Testing and Assessment" presents detailed guidelines and recommended practices for performing comprehensive security testing and assessment of complete IT ecosystems, involving applications, networks and systems. It is always worth remembering that each organization has its own particularities regarding its environment and value of assets, etc., but based on some of the guidelines in the NIST special publication, and by comparing and adapting them to various other publications and articles, it is possible to summarize (and summarize a lot) a good vulnerability assessment in the following steps:
Planning: Define the scope of the assessment, identify the networks, systems, applications, devices, and any other assets to be assessed, establish the security objectives and requirements, prioritize the assets according to their criticality, and obtain the appropriate authorizations.
Threat Analysis: Identify potential threats that could affect the ecosystem assets and analyze the known techniques and vulnerabilities, a good reference source for this is the MITRE ATT&CK matrix.
Vulnerability Scanning: Use automated tools and manual techniques to actively identify known vulnerabilities in the environment.
Risk Analysis:Assess the potential impact and likelihood of exploitation of each identified vulnerability, taking into account the criticality of the assets.
Report and recommendations: Produce a report containing all identified vulnerabilities and recommendations for remediation and security improvements.
Mitigation and remediation: According to the priority and criticality of each asset and vulnerability respectively, perform the recommended remediation actions, such as applying patches, configuring systems, or updating security policies.
Retesting: This is a task that is often overlooked, but it should not be. After vulnerabilities have been identified and properly fixed, it is important to retest some vulnerabilities and perform additional tests to confirm that the vulnerabilities have been fixed and that the mitigation actions were effective.
Review and continuous improvement: Conduct a post-assessment review to identify opportunities for improvement in the assessment methodology itself and in the organization's security practices.
Scanning Tools
ChatGPT was asked to rank the five best vulnerability assessment tools available both commercially and free or open source and here’s the answer:
Commercial tools:
• Nessus (Tenable)
• Qualys
• Rapid7 Nexpose
• Acunetix
• BeyondTrust Retina
Open source Tools:
• OpenVAS
• OWASP ZAP
• Nikto
• Nmap
• Wapiti
Conclusions
After all of the above, it is possible to conclude that vulnerability assessment is a fundamental task for an organization to raise its cybersecurity maturity level and have a more robust security posture. It is important that this is a continuous and regular task for the Blue Team, or security teams in general, that should think about security proactively, besides all the reactive measures that are inherent to this role, i.e., it is essential to be one step ahead of cyber threats, and these periodic assessments help achieve this goal.
Another important point to note is the integration of these evaluations with the activities of the offensive teams, which should test the applied corrections and validate their effectiveness.
In short, for the process to be truly effective, it is essential that organizations follow best practices, perform security tests with a regularity to be defined within a policy, correct problems found, and stay up-to-date on constantly evolving threats.