We have often mentioned that it is essential to keep up to date with the latest software versions to stay protected, this time we focus on securing your browsing.
Recently, Google has taken steps to strengthen the security of Chrome users by implementing an enhanced version of its Safe Browsing feature, which offers real-time protection against potentially malicious sites, without compromising user privacy.
Upgraded protection
As announced, this update represents an effort to improve the efficiency of real-time protection for Chrome users on desktop and iOS. Safe Browsing, in its enhanced form, compares visited websites against a dynamic list of URLs recognized as dangerous or malicious. This list is hosted on Google's servers and is continuously updated to reflect new threats as soon as they are identified. This process differs from the previous version, which used a local list that required periodic updates every 30 to 60 minutes, a method that, while effective, may not be sufficiently agile in the face of the speed at which new threats emerge online.
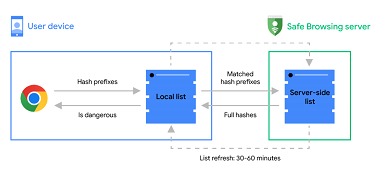
The transition to server-side checks is intended to address two main problems: first, the list of malicious sites is constantly growing, making it increasingly difficult for individual devices to manage, especially those with limited processing or storage capabilities. Second, the need to frequently update these lists to maintain effective protection can overwhelm the ability of some devices to receive and apply these updates in a timely manner. This change not only improves the effectiveness of the Browser, but also optimizes performance by relieving individual devices of the burden of maintaining and updating large lists of malicious sites.
New Architecture
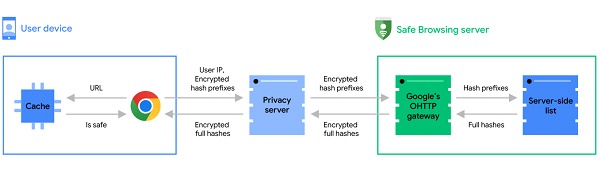
Under the new architecture, when a user attempts to access a website, the URL is instantly compared with global and local caches in the browser. These caches contain both known safe URLs and the results of previous checks performed by the Safe Browsing feature, allowing a quick and efficient determination of a site's safety.
If a URL that the user attempts to visit is not found in the browser's global or local caches, Chrome's Safe Browsing system initiates a real-time check that begins with URL obfuscation. This process involves converting the entire URL into a 32-byte hash, which is then reduced to a hash prefix of only 4 bytes. This prefix, after being encrypted, is sent to a private server dedicated to preserving the user's privacy.
Google ensures that this private server is specifically designed to remove any identifiers that could link the security query to a specific user. After this debugging, the encrypted hash prefixes are transmitted to the Secure Browsing server over a secure TLS connection. This connection not only protects the integrity and confidentiality of the transmitted data, but also pools requests from many Chrome users. This method of "mixing" requests ensures that individual URL checks are indistinguishable within the overall data traffic, providing an additional layer of anonymity.
Once the hash prefixes arrive at the Safe Browsing server, they are decrypted and compared against an extensive database of URLs known to be dangerous or malicious. If there is a match between the hash prefixes sent by the browser and those contained in the database, the server returns the full hashes of all matching insecure URLs. This approach allows Chrome to determine whether the URL the user wants to visit is safe or not, without Google having direct access to the full URL visited, thus maintaining a balance between security and privacy.
At the end of the client-side loop, the full hashes are compared with the full hashes of the visited URL and a warning message is delivered if a match is found.
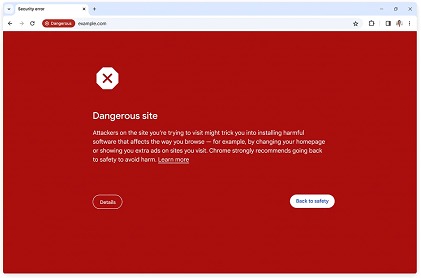
Jonathan Li and Jasika Bawa, Product Managers at Google explained that under this new approach, if Chrome identifies that a website may pose a risk to the user or their device, an informative warning will be displayed. This approach is intended not only to alert the user to potential dangers, but also to provide an additional layer of security when browsing the web. With this update, Google estimates an increase in the browser's ability to block phishing attempts, significantly improving protection against this type of threat.
This hybrid approach (between local and remote) reduces latency and preserves user privacy by minimizing the amount of shared data.
Conclusions
Google's decision to move towards a real-time verification of websites against a list of malicious URLs hosted on its servers is a step forward in the commitment to user security. Above all, it is remarkable the incorporation of complex controls to usual functions to offer "safer" versions, among other examples we can mention the Dark Web Report or the Password Verificationwhere in an almost organic way the user is guided to elevate his protection making him part of the solution
It is in our hands to adopt these tools.