Custom Browser Analysis
Introduction
The main objective of this work was to evaluate the security of an exclusive browser for the banking sector, based on Firefox. This browser is used by a large number of banking customers and it is important to ensure that its use is safe and protected from possible risks.
To carry out the tests, the Windows 10 x64 operating system and the Visual Studio 2019 compiler were used. With these tools, DLL files were created and used to evaluate the browser in different scenarios and situations. Some of the tools used were: IDA Pro, Process Monitor, and CFF Explorer.
In this publication we will show some common vulnerabilities that can be found in custom developed browsers, which are mainly used by banks. These browsers offer users some browsing security, just because they are exclusive browsers.
Some of its advantages are the following:
• Single installation
• Automatic update
• Controlled access to accounts
• Improved browsing experience
Functionalities allowed by the browser:
• Home button to company site
• Reload website button
• Add favorite button
These types of browsers were analyzed to validate and test the possible risks that are counter to the security offered by the browser.

DLL Hijacking
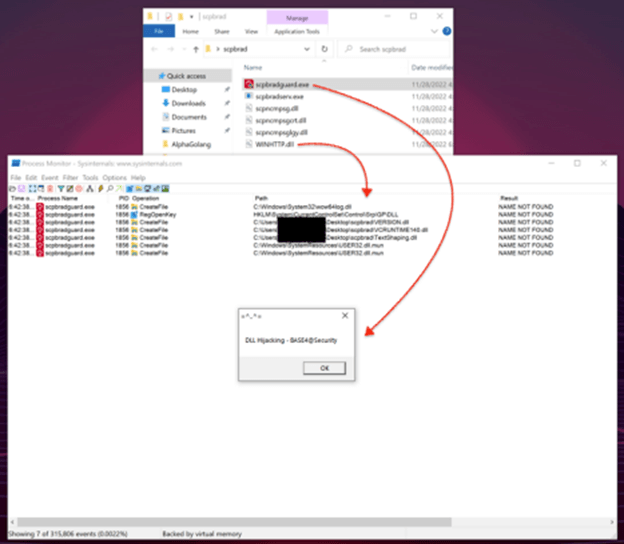
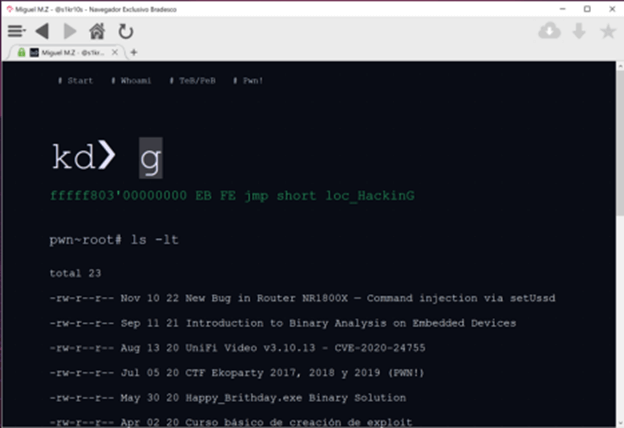
The first vulnerability found is DLL hijacking. This tricks the legitimate and trusted application into loading an arbitrary DLL. The binaries responsible for calling the DLL and its functions are scpbradguard.exe and scpbradserv.exe which runs as a Windows service.
This type of kidnapping would achieve three objectives:
• Execute malicious code
• Obtain Persistence
• Obtain Persistence
Let's get down to business!
First we identify the services that run after installing the browser. For it we use Process Monitor with some filters, this way we avoid to load unnecessary information. With the filter activated we can identify that there are two DLL not found VERSION.dll and WINHTTP.dll, we will focus on the second one.
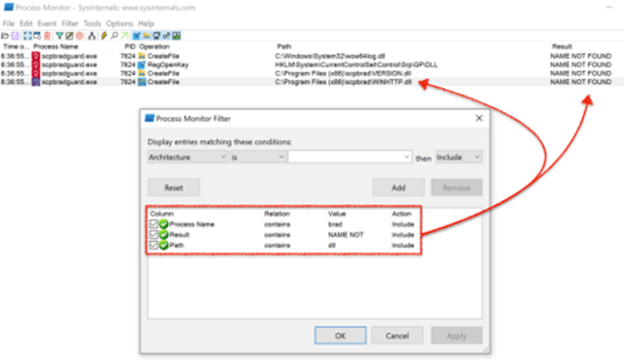
The next step is the identification of its functions, this information is necessary for the creation of the malicious DLL. In this case we use CFF Explorer, although IDA or Ghidra could be used, although if in-depth reverse engineering is not necessary, the first tool will suffice.
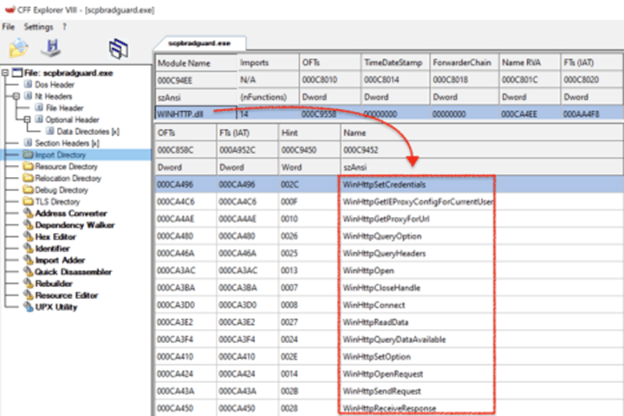
With the information obtained the DLL is programmed in C++ and compiled with Visual Studio 2019, then the DLL is copied to the root directory of the binaries or simply copy the binary to any Windows directory with the DLL.
Navigational Avoidance
Within the analysis of the browser, the first thing that was verified was whether it correctly complied with its security policies on navigation and blocking of third-party sites.
In the first instance, it was verified that the navigation bar is disabled, avoiding changing the domain already defined by the browser. For this type of restriction two evasions were made. The first one by HTML and the second one by means of parameters of the executable, which will be explained next.
So as not to be long and boring, let's get to the point!
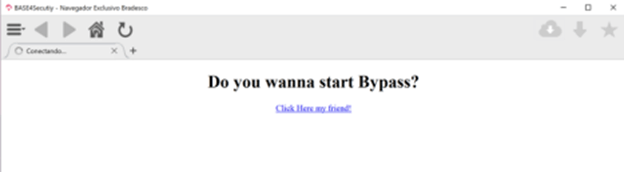
Open Redirect via HTML File
In the tests it was concluded that by creating an HTML file it is possible to execute the domain redirection. Now the only problem that was found was that the domain must be in an allowed list for the redirection to be executed, this means that the domain must contain the name of the company.
For this we used a simple bypass which consists of adding the domain name, followed by the HTTPS protocol. With this we exceeded the allowed list and the interpretation of the redirection would take the domain after the "@" character, since the rest would be in the format of username:password@domain.
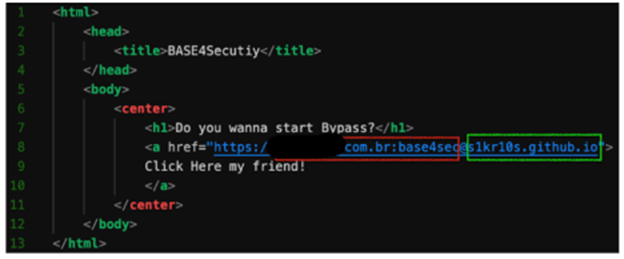
To execute the file it is enough to load the HTML in the browser using "DragDrop", but this would not be realistic. The browser itself, when installed, allows to keep it as default, which would facilitate its execution. Next, we can see how the file is loaded correctly by the browser, allowing to execute the redirection to a domain that is out of the allowed list.
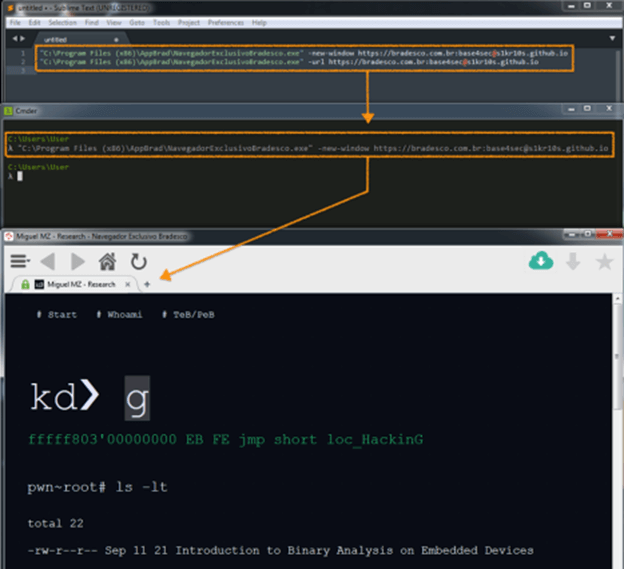
Open Redirect via Parameters
There is another less realistic way, but which still allows to evade the restriction, by means of parameters allowed by the browser. We can find the -url and -new-window parameters that allow to open an arbitrary domain, in the same way it is necessary to keep the url format to evade the allowed list. For more information on the CommandLineOptions used:
https://wiki.mozilla.org/Firefox/CommandLineOptions
To take this to a real exploitation it is necessary an intermediary binary (Malware) that activates the command each time the browser is called.
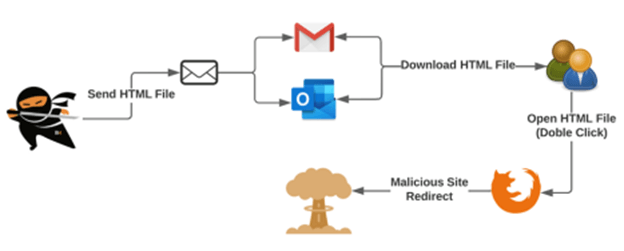
Phishing attack flow
The following flow represents how an attack is possible using the Open Redirect vulnerability that maintains the custom browser to users who use that browser. For this, the attacker sends the file by some means to the user. The most common would be via email, then the user downloads and executes the file being redirected to a malicious site.
Conclusion
In summary, the proof-of-concept tests of the Bradesco bank's proprietary browser showed that it contains vulnerabilities that may be dangerous for its customers. However, these aspects could be improved and it is recommended to implement additional security measures to further protect users. Therefore, it is important to continue working on improving the security of the browser and protecting its users.-



