REFERENCES
Innovación Pública de la Jefatura de Gabinete de Ministros de la Nación Argentina
(s.f.). “Firma Digital”.
Argentina.gob.ar:https://www.argentina.gob...
https://www. argentina.gob.ar/...
https://www. argentina.gob.ar/...
Digital Signature What is it and how to get it for free?
When talking about Digital Signature, there are several confusions: Is it
the same as a digitized signature? Does it have the same legal validity as a handwritten
signature? How much does it cost to implement it? What are the benefits of using it and what
security measures should I take into account? How does it differ from the electronic
signature? If you have ever asked yourself any of these questions, we invite you to continue
reading this post. In a simple and summarized way we will tell you everything you need to
know about it.
Legal regulations in Argentina
Law 25.506 of 2001 is the regulation in force that recognizes and establishes the conditions
for the use of the Digital and Electronic Signature in Argentina and determines its legal
effectiveness. In its article 2 the regulation conceptualizes the "Digital Signature" in a
very specific way, so we have to be very attentive to each of the requirements foreseen,
because in the absence of one of them, the signature will be considered "electronic" and its
evidentiary value will be different.
"A Digital Signature is understood as the result of applying to a digital document a
mathematical procedure that requires information of exclusive knowledge of the signatory,
which is under his absolute control. The digital signature must be susceptible of
verification by third parties, so that such verification simultaneously allows the
identification of the signer and the detection of any alteration of the digital document
subsequent to its signature".
The following is a brief but detailed explanation of each part of this definition:
• The application of this technology only makes sense in a digital
document, which is a digital representation of acts or facts regardless of the support used
for its fixation or storage (art. 6). That is, they can be "Word" files, in PDF format,
e-mails, web pages, spreadsheets and all other information included in an electronic
support. At this point it should be noted that if we digitally sign a document and then
print it, it loses the characteristics enshrined in the law.
• It is very important not to lose sight of the fact that the Digital
Signature is the result of applying a mathematical procedure: it is an algorithm that is
attached to the digital document. Therefore, the logo indicating "digitally signed" alone
has no value. A specific technological process must be carried out to sign and then another
one to authenticate that signature.
To technically understand what happens in the "background" when applying this technology, we
must first recognize a couple of concepts:
A. The security of the technique discussed in this post is guaranteed by
"Asymmetric Cryptography", which is a cryptographic method characterized by having two keys.
They are different, but they are mathematically related, so that what is encrypted with one
can only be decrypted with the other (they always work together). This pair is known as
"Public Key" and "Private Key". The latter is of exclusive domain and only known by the
signer.
B. On the other hand, we will refer to the hash function, which
transforms bit strings of arbitrary but finite length into fixed-length strings of n-bits.
In other words, it returns as a result the same fixed length of characters, regardless of
the size of the document. It is a kind of digest and, therefore, two documents may appear to
be identical at first glance, but because they have different hashes they cannot be
considered to be the same.
Taking into account the concepts developed above, we can proceed to explain how an
application digitally signs a document and then verifies its authenticity.
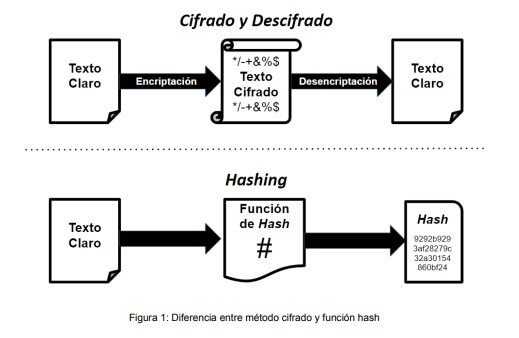
When performing the Digital Signature, the following steps are carried
out:
1. The software calculates the cryptographic hash of the document to
be signed.
2. The newly calculated hash is encrypted with the issuer's private
key (the password with which the user protected it will be requested at this point).
3. Finally, the encrypted hash is attached along with other data to
the document (date and time of signature, signer data, etc.).
To carry out the authentication procedure of the Digital Signature, the receiver must
possess the public key of the issuer (contained in its digital certificate). Subsequently:
1. The software calculates the cryptographic hash of the document.
2. It then decrypts the hash embedded in the digital signature with
the issuer's public key.
3. The results obtained in the previous steps are compared.
If the hashes obtained in section 1 and 2 are identical, the receiver can ensure the
following:
A. Integrity: the document has not been modified since the time of
signature.
B. Authentication and non-repudiation: the private key with which it was
signed agrees with the public key (remember that both are mathematically related and that
the private key is only known by the issuer, because it is information of his exclusive
knowledge). Therefore, the signer is thus authenticated.
Continuing with the explanation of the definition previously presented:
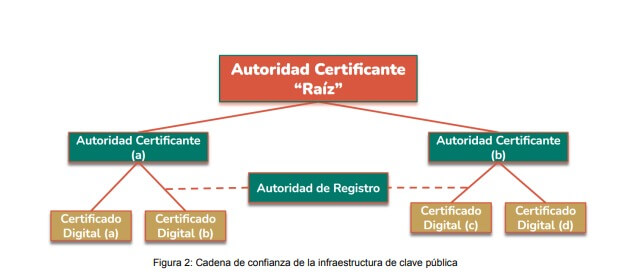
- This system must be susceptible to verification by third parties: to ensure the
reliability of the signature and authentication procedure, it is necessary to guarantee that
the public key belongs to the signatory. This is why the concept of "Public Key
Infrastructure" (PKI), which regulates the issuance and distribution of keys, is so
important.
Digital Certificates are documents digitally signed by a Certification Authority (CA) that
certify that a public key belongs to a specific individual or entity. They can be
authenticated in the same way as any other document with Digital Signature. For more
information on this point, we recommend consulting chapter II of the law 25.506 "of digital
certificates" and the X.509 standard that specifies the standard formats for digital
certificates and the validation algorithm of the certification path, among other aspects.
To conclude this section, let us return to a previously mentioned
concept. The norm indicates that, if the signature lacks any of the legal requirements to be
considered a digital signature, then it will be in the presence of an electronic signature.
If a person denies or does not know a Digital Signature, it is he who must prove that it is
false. On the contrary, if an electronic signature is denied or unknown, it is the other
party who must prove its veracity. In all cases in which a regulation requires a digital
signature, an electronic signature will not be sufficient.
Benefits of implementation
The main benefits of its implementation are:
• Digitally signed electronic documents have the same legal validity as
those signed in a handwritten form. When the law requires a handwritten signature, the
requirement is also satisfied by the Digital Signature (art. 3), with the exception of
article 4 of the aforementioned law.
• It is feasible to use it for various procedures in public and private
institutions and to sign any type of digital file.
• It is possible to identify the person who signed digitally and he
cannot deny or repudiate its existence or authorship. It is presumed, unless proven
otherwise, that the Digital Signature belongs to the holder of the digital certificate that
allows the verification of the signature (art.7).
• If the result of the verification of a Digital Signature is valid, it
is presumed, in the absence of proof to the contrary, that the document has not been
modified since the time it was signed (art. 8).
• Digitally signed electronic documents are considered originals and have
evidentiary value (art. 11).
• The legal requirement to keep documents, records or data is satisfied
if they are digitally signed, provided that they are accessible for later consultation (art.
12).
• It automates processes, provides flexibility and ubiquity, saves time
and money, contributes to the environment, and allows the traceability of electronic
instruments to be analyzed, among others.
Procedure to obtain the Digital Signature
The first thing to do is to request an appointment through the Internet and then go to the
selected "Registration Office", on the assigned date and time. It should be clarified that
the procedure is free of charge and is valid throughout the national territory. It can be
generated through two ways:
• Remote (with cell phone): in this case the "Google authenticator" must
be installed on the cell phone. This mechanism can only be carried out by human beings and
only serves to digitally sign files in PDF format through the "signer" accessed through the
web.
• Token: it is necessary to attend with the device that must be
previously acquired. Then, documents can be signed and authenticated through specific
applications such as "XolidoSign" or "Adobe Acrobat Reader".
Related services
Related services
•Detailed project planning.
•Risk matrix with the main situations related to the implementation,
their probability of occurrence and impact on the business. Detection of Strengths,
Opportunities, Weaknesses and Threats.
•Management of appointments to obtain the digital certificate.
•Preparation of a timetable specifying when employees should go to the
"Registration Office" nearest to their home address
•Evaluation of the number of token devices that will be needed, taking
into account the critical business processes and the referents involved.
•Preparation of a Training Plan on legal and technological aspects, use
of secure passwords and use of software to digitally sign and authenticate
signatures.
•Process reengineering for the implementation of this technology.
•Configuration of the chosen application for digital signature and
preparation of the associated documentation.
•Creation and approval of the procedure for the storage of digital
documents and their respective backup copies.
•Installation of "root" and "intermediate" certificates on all
workstations.
•Advice from qualified, experienced and qualified professionals.
From BASE4 Security SA we provide such services, in which we apply all our experience in the
industry, both in the technical and management aspects.-



