Cunning and creativity have characterized some of the cyber-attacks of recent times, and when it comes to social engineering, the adversary will do whatever it takes to make our users believe they are in a safe place, even though they are actually in enemy territory.
Within this approach we find the homographic domains and the surprise comes when we see for the first time that gοogle[.]com is not google[.]com.
Homographic Domains
Homographic domains are those that visually resemble legitimate domains, but are not the same, but one controlled by a third party (apple[.]com looks like aple[.]com). This technique allows attackers to provide a "story" based on those domains they are trying to spoof.
This technique is specifically seen in phishing attacks, attackers register domain names similar to real services used by organizations and in these they typically store malware, scripts, redirects or simply forms to collect data.
Within the types of homographic domains, we find those that make use of characters from different alphabet encodings. To understand it clearly, here is a list of letters from different alphabets that visually resemble vowels (A, E, I, O, U), along with the alphabet to which they belong:
a (Roman / Latin)
• а (Cyrillic) - Used in Russian, Bulgarian, and other Slavic languages.
• α (Greek) - Alpha letter.
e (Roman / Latin)
• е (Cyrillic) - Used in Russian and other Slavic languages.
• ε (Greek) - Letter epsilon.
i (Roman / Latin)
• ι (Greek) - Letter iota.
• і (Cyrillic) - Used in Belarusian and Ukrainian.
• ı (Turkish) - i without dot, distinct from "i" with dot.
o (Roman / Latin)
• о (Cyrillic) - Used in Russian, Bulgarian and other Slavic languages.
• ο (Greek) - Letter omicron.
u (Roman / Latin)
• υ (Greek) - Epsilon letter.
• у (Cyrillic) - Used in Russian and other Slavic languages.
The visual similarity of these letters is one of the reasons why they are used in homographic domains; they would easily fool even the trained eye.
For example, an attacker could then register a domain that uses a Cyrillic character, such as "а" (Cyrillic letter) instead of "a" (Roman/Latin letter). At a glance, the domain might appear legitimate, but it is actually a different registration.
Case and Response
A phishing email could then include these specially formed domains registered to host a malicious payload.
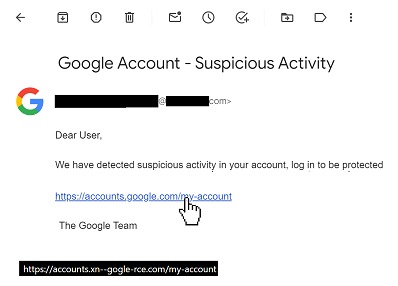
The text visible in the body of the email remains (as always) a series of characters that could have nothing to do with the link behind it. Browsers have long since opted to shed some light on these activities, through a special encoding called "punnycode". This allows characters to be converted to ASCII where we have a restricted character set.
This has turned out to be a big win because as users, we can once again rely on that little popup. Online mail services even when opening these sites.
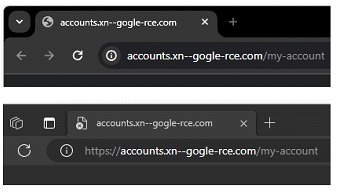
Our victory is not long-lasting (it almost never is), as we notice that only webmail clients perform this decoding for our users. Not so the clients installed on workstations.
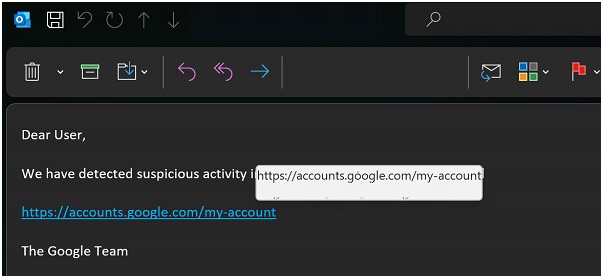
And this is where a journey begins to recognize what software in the organization might be "vulnerable" to this function: Office applications? Our management systems? Mobile phones?
We can then start from our asset inventory (the one we always have updated) to develop measures and strategies to protect the systems.
To conclude
As professionals in the field, we know that sometimes the best defense is a good offense: educating and raising awareness will be our first stop. Diving into the world of homographic domains not only adds another layer to our digital armor, but also gives us a clearer perspective on the tactics employed by adversaries around social engineering. At the end of the day, awareness can be as crucial as any sophisticated tool in our arsenal, but it is still just one more protection in our strategy.