Incident response simulation exercises, also known as Tabletop Exercises (TTX), allow us to simulate critical situations in a controlled and safe environment. This gives the different teams the opportunity to evaluate response capabilities, the level of preparedness for a possible crisis, identify areas for improvement and take preventive measures to minimize risks. Special focus is placed on improving communication and coordination between teams, as well as strengthening the ability to make effective decisions in high-pressure situations. They also help organizations comply with regulatory requirements for incident management.
We have reviewed some details about this type of exercises inprevious publications and in this opportunity we will explore our own methodological framework, developed and tested on several occasions to carry out this type of exercises.
Methodology
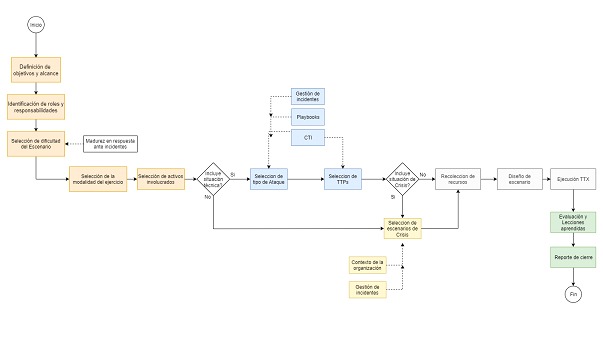
For the development of an incident response simulation exercise, like most processes involving continuous improvement, an iterative process based on four phases is defined. This type of exercise can be applied to any process, area or technology within the organization (e.g. Crisis for C-Level or full scenario with multiple teams).
These phases will provide a structured and systematic framework for the design, implementation and evaluation of these exercises, through which organizations can ensure that they are appropriate, relevant and challenging, enabling them to improve their ability to respond to potential cybersecurity threats.
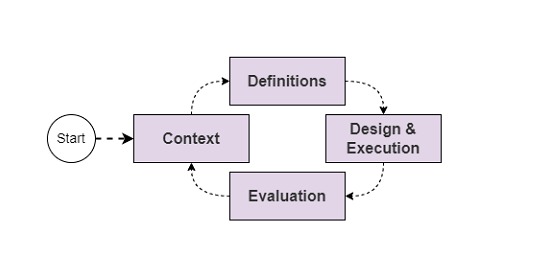
Context phase
The first phase of a TTX involves the collection of all the elements that will form the basis of each subsequent design decision. This phase is critical to ensure the success of the entire exercise execution. We can divide this phase into five stages:
1. Definition of objectives and scope of the exercise: It is determined what is to be achieved with the exercise and what are its limitations and scope. Although this type of exercise has a series of specific objectives, each design must consider or modify them as needed.
Identification of roles and responsibilities: Here the roles and responsibilities of each of the team members involved in the exercise are identified. Each participant will have a specific and defined role from the beginning of the planning. Among the possible roles we can find the active participants, who will participate and have an active role during the execution of the exercise, a team in charge of the scenario design, in charge of the previous stages of definition and design, a coordinationteam, who will guide the previous definitions and the execution of the exercise and finally the role of observers, the latter in charge of observing the execution of the exercise to later provide proposals for improvements and other types of comments that may add value to the results of the exercise.
Selection of the difficulty of the exercise: This stage allows defining the level of complexity and challenge that the team will face. A realistic exercise will always be intended, although the maturity of the teams participating in this type of exercise, their real experiences, process status, available tools should be considered.
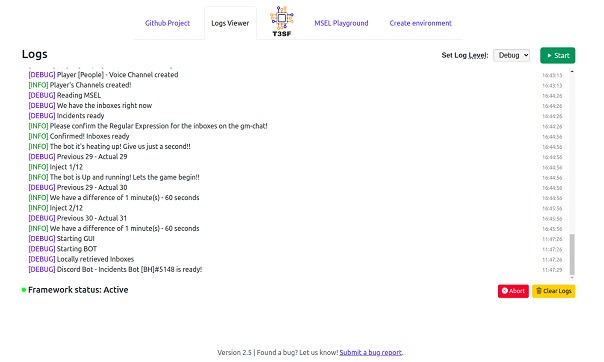
4. Selection of the exercise modality: The exercise modality will vary according to the type of interaction and the tools used. Typically, we can find two options, a scenario of a single flow of events, guided by a presentation, and a scenario made up of multiple flows of events assisted by some kind of automation platform. In particular for our designs and execution we use T3SF (Open-source tool developed in-house to facilitate the design and execution of this type of exercises).
5. Selection of the assets involved in the exercise: The assets selected can range from critical business lines, suppliers, key operations to specific elements such as computer systems, databases, network devices. Any asset that falls within the objectives of the exercise can be selected.
Definition phase
At this stage we are faced with the choice of the type of threat or major crisis situation to be considered for the design. This definition may include one or more threat types in relation to the objectives of the exercise. This may be defined by risk management, or cyber threat intelligence reports (internal, external, or aligned with the sector to which the organization belongs).
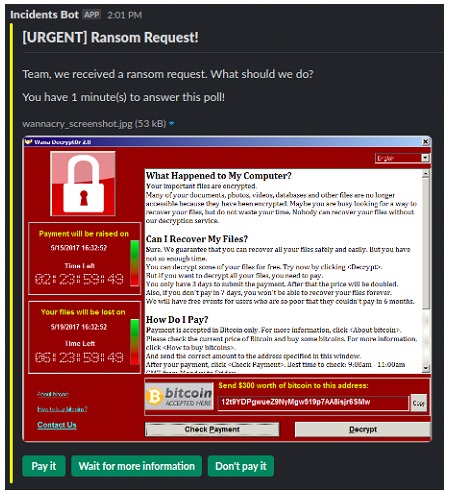
Examples of common threats include Ransomware, Denial of Service, Insider Threat, Data Leakage, Social Engineering, Supply Chain Attack, and Physical Disruption.
To give context to these threats, tactics, techniques and procedures (TTPs) to be simulated will be selected as a reference. In our case we made the selection based on the MITRE ATT&CK framework, the main industry reference.
If the exercise is designed for teams directly related to decision making (C-Level, Board of Directors, Crisis Committee), in this phase the crisis situation to be included in the scenario will be defined (always in relation to the objectives and scope).
Simulated impact scenarios will also be defined, e.g. in the form of some kind of repercussion to customers, suppliers, employees, stakeholders, social networks, press media. These definitions will guide the specific events that will be shown during the execution of the exercise. Scenarios with specific impact can also be developed, such as a drop in shares, decrease in operations, loss of operating licenses, loss of contracts with third parties, fines or legal actions.
Design and execution phase
In this phase, work begins on setting up the scenario itself, through the design process, and ends with the execution, on the DAY OF THE EXERCISE. This phase can be divided into three stages:
1. Resource collection: Elements linked to the assets defined in the scope and related to the technical and/or crisis definitions are collected. Among these we can find: regulations, related incident reports, references to third party crisis situations, supplier documentation, or other assets involved.
2. Design of the scenario: In this stage, the design of the scenario itself is carried out. A storyline will be elaborated to give structure and consistency to the scenario, and then the "participant's view" will be worked on, which will be made up of the events observed during the exercise.
• History design: A timeline is defined that will include the complete scenario of the simulated attack, from the initial access vector, techniques used. This timeline is not reduced to the attack chain from the technological point of view, but includes the route to impact and the different types of repercussions. This design of the history subsequently allows the fluidity in the execution of the exercise, an exercise containing non-aligned components can be interpreted as fictitious and hinder the dynamics of participation.
• Participant View Design: This design will be formed by the events that will be shown to the participants during the scenario execution, it will be based on the history and detection capabilities of the organization. The different events are grouped in an event structure known as MSEL (Master Scenario Event List). Each event may contain information about a situation (received from a third party or any other source), explicit decision options or additional information about the progress of the incident, e.g. the result of a forensic evaluation or a definition of a participant not present in the exercise.
3. Execution of the exercise: This stage comprises the implementation of the designed scenario, allowing participants to interact with the scenario and respond to events as they occur. This will be "The day of the exercise", a time scheduled with the different teams, where the meeting will be held in the modalities established in the design (face-to-face, virtual or on the platform). During a period of 2 to 3 hours the different events will be sent and the actions reported by the participants will be recorded.
Here the follow-up by the coordinators will be crucial to ensure that the planned objectives are met. Yes, this is the most fun part of the whole exercise. A well-planned scenario can lead to lots of valuable conversations, and discussions with a level of intensity that can only be found during a real incident, but in this case with the peace of mind of being in a simulation.
Evaluation and improvement phase
The last phase of the incident response simulation exercise can be divided into three stages:
1. Lessons learned analysis:A lessons learned analysis is conducted during the exercise. This may include the identification of the team's
performance, identifying strengths and weaknesses the effectiveness of established plans and protocols, and any other relevant aspects that may help improve the team's response capability.
2. Exercise evaluation: This stage involves the evaluation of the exercise, analyzing the team's performance, identifting areas for improvement and assessing the achievement of the exercise objectives.
3. Implementation of improvements: The last stage involves the implementation or projection of the improvements identified throughout the exercise. This may include updating plans, training teams, acquiring new tools, enabling configurations in software solutions, among others.
Conclusion
TTXs are a key tool for improving capabilities to deal with threats and crisis situations. A well-designed and executed exercise helps to identify gaps in processes related to incident response, improve the ability to manage critical situations and adjust action plans in response to them. With increasingly sophisticated cyber-attacks, the need for an efficient response increases, and these exercises must be properly planned to ensure that teams get the maximum benefit.
People find in Tabletop Exercises a space to test their skills in a critical situation, but a poorly designed scenario can result in a mere "simulated situation" that does not add value because it is not challenging. It is crucial that TTXs are realistic and aligned with scenarios that make sense for the context and objectives of each organization. All this makes it important to have a solid methodologyto ensure that valuable and useful information is being obtained.