One of the most efficient ways to create innovation is to do it together with the users. Since they are the fundamental piece of any improvement within an organization, regarding any modification or development that we want to implement. Changes happen all the time and generally people tend to have a marked resistance to it, not because we do not want to adapt easily, but because this shows that it is difficult for us to think as a team, to exchange ideas, or to accept a new idea from a peer.
It is true that there are people with greater tolerance to different types of changes, but apart from judging this issue, we always tend to point the finger at the other person when we identify resistance.
Why do these issues occur in social life? Why is resistance to change so strong?
If we were to define "Resistance to change", we would normally understand it as a negative attitude towards change, assuming the consequences of such change and the refusal to support its implementation in the scheme we use on a daily basis. Most people tend not to want to consider that the current state should or can be changed, having as an anchor the current satisfaction resulting from the responses that potentially report positive attitudes towards their own work, so they consider it correct. As a result, they do not want to take the risk of changing, and that is where the feeling of risk becomes a real risk that, depending on the discipline, may or may not have major consequences. If we refer to cybersecurity, we are talking about the consequences of users' resistance to change in the face of a security policy or a new procedure for handling information, which can have catastrophic consequences.
But not all the blame is on the end user and his resistance, we are focused on the "tree" and this "tree" covers a forest of possibilities for us to make ourselves better understood. Usually, in our day-to-day management as cybersecurity professionals, the user puts us on the opposite side of the street. Because we may have the profile of constantly observing what they do and evaluating the way in which users treat the information of the organization to which they belong.
Among the reasons that occur when understanding these issues, we find that these important points to observe may appear, according to the Prosci site there are several causes regarding the resistance to change, but among them, we can highlight the following:
• Lack of awareness of why the change was being made
• Impact on current job role
• Fear rooted in uncertainty due to past failed changes
• Lack of visible support from and trust in management or leadership
• Lack of inclusion in the change
If we think about these main factors and stop blaming the user for mismanagement or misunderstanding of the concepts, and focus on resolving some of the points mentioned above, we could stop this resistance in time and get the change accepted.
One of the things we do in information security is to raise awareness of the reasons, but along the way, beyond taking pains with infographics, videos, mandatory training, forced rules and a long etcetera, we forget the constant support to the user, to remove their fears and thus be able to include them in the decisions that become critical, depending on the environment in which they are treated, as we have explained in the previous paragraph.
Design Thinking
This is where Design Thinking comes to give us a hand, or rather, what we need for the user to cross over. This method will allow us to sit down with the user to implement the new changes, obtaining new clues on how to incorporate the concepts and how to improve communication day by day so that those concepts that we need to incorporate occur organically and become established in their minds, eliminating as much resistance as possible.
In order to understand this method let's do an exercise, which came first, the user or the new idea? This idea could be just as long as the question of which came first, the chicken or the egg?

If we immerse ourselves in this loop, we end up falling into the lack of ideas when it comes to generating awareness, because we blame each other and meanwhile, the backlog of problems is overloaded, leaving us completely saturated in our day to day and with the bar of patience on the floor. So all this translates into the following sentence: I have an innovative idea (or a need to implement a new process), do I impose it or do I first analyze the user, identify how they feel more comfortable and elaborate an implementation strategy so that everything happens with the least possible friction? In short, it is creating for the user or creating together with the user. Impose something or achieve an organic acceptance of that change
As part of any innovation process, it is essential to include the stakeholders from the very beginning, in order to understand which mechanisms to use. Design thinking in particular is a user-centered agile innovation methodology. It consists of the following stages: EMPATHY, IDEA DEFINITION, PROTOTYPE and TESTING;
If we think of this in terms of our language, we are applying an attack methodology, against the resistance to change, finding what are the potential vulnerabilities of the same. In all anatomy of the attack we find that it follows a similar structure to the one we need to apply, in the case of computer security language we find the stages of Discovery and Scanning, Enumeration, Gaining Access and Persistence, if we allow ourselves to make an analogy to these issues we find the following parallelism:
• EMPATHY (Discovery and Scanning): Understand the user, identify the pain points, combine it with what we want to apply, in short, make a discovery of the attack vectors we have with respect to the user's interests.
• IDEA DEFINITION (Enumeration): Based on the user interests surveyed, try to identify which are the main points to attack. After this, the most concrete information is obtained.
• PROTOTYPE (Trying to get access): Through materialization, we are elaborating a trusted channel approved by the user to implement the change. The game is opened for potential ideas and then the best option is chosen.
• TESTING (Persistence): Constantly testing the strategy so that this change is assimilated with the required organicism and the least amount of friction possible, until the corresponding adaptation occurs. The idea is concretized.
Throughout this process of implementing our Design Thinking method, we must be aware of which are the best paths according to the discipline we handle, each new idea to be implemented will bring with it its respective complexity. A good way to understand this method is through a double diamond model, like the one we see below:
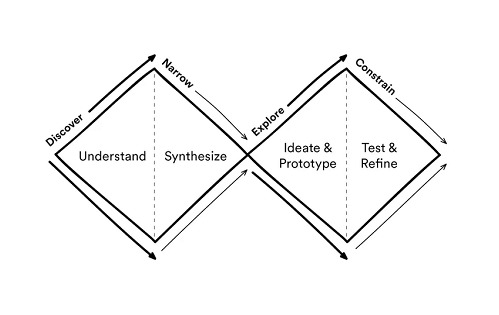
As can be seen in the graph, there is a process of understanding in which there is an expansion in that discovery, followed by a synthesis to keep the points of greatest interest, then the game is opened to explore again and finally the solution is designed and tested to finish refining it and narrow it down as much as possible.
Our Tools
There are several methodologies to approach users, each stage has its own according to the issues we need to implement:
• EMPATHIZE: Focus Groups, Active Listening of stakeholders.
• ⦁ Stakeholder Map: The stakeholder map is a tool used to identify the people, entities and administrations involved in a business or system, as well as the relationships established between each of them. It is a tool widely used in Design Thinking processes, which comes from the social sciences. A stakeholder map is divided into 4 circles, in which stakeholders belonging to the following categories are integrated:
• Users: Are placed in the central circle, the smallest one. The map starts from them, and from the relationships they establish with the actors placed in the other circles.
• Internal actors: They are placed in the circle closest to the central one. In it, you will have to place those actors that interact as directly as possible with the users.
• External actors: Those whose relationship with the internal actors makes possible the production or delivery of the product or service to the users. They are placed within the second circle.
• Public administrations: Public entities that relate directly or indirectly (through other actors) with the users.
• Discussion Groups: The Focus Group or discussion group is a qualitative research method in which a group of informants of a certain profile are brought together. The objective of the Focus Group is that these informants participate by giving their opinions and answering questions about a topic, product or service. The information obtained from a Focus allows the company that carries it out to have a more approximate idea of what the set of users that the Focus participants represent think.
• Cognitive Immersion: Cognitive immersion is a Design Thinking dynamic designed to experience what a user experiences in a specific situation.
• World Café: Serves to inspire meaningful conversations in a particular group of people. Among the main objectives of a World Café are the following:
• Facilitate a space for conversation
• Encourage the participation of all
• Generate inspiring conditions
• Collect the highlights
• To give continuity to this process with new meetings
• Covert Observation: It basically consists of observing a group of people without them realizing it, avoiding the intervention of their behavior.
• BenchMarking: Qualitative research technique, the concept focuses on quality, also focusing on observation.
• The 5 whys: The purpose of this tool is to learn how to pull the thread within an interview, it takes place when sharing findings and/or reflections within a team. In order to apply it, simply ask Why? After each answer, a total of 5 times.
• DEFINE: We may use the following techniques and tools that will allow us to cross-reference our interests with those of users.
• Mental map: A mental map is a graphic tool, which is represented in the form of a scheme. It allows us to visually show different concepts and their different relationships with the elements that make them up. It has been widely used as a learning tool and can be very useful in a design process.
• Out and in: Its purpose, above all, is to help you organize the information in a visual way, and have it in an accessible way. A good number of Post-its, a wall, patience and synthesis capacity.
• Saturate and group: Su finalidad, sobre todo, es ayudarte a organizar la información de forma visual, y contar con ella de un modo accesible. Un buen número de Post-its, una pared, paciencia y capacidad de síntesis.
• Ishikawa Diagram: An Ishikawa diagram is a simple tool invented by the Japanese industrial chemist Kaoru Ishikawa. It arose as a result of a cause-effect diagram drawn by this expert in quality control. In it he collected, in a very simple visual form, all the causes that ended up giving rise to problems within a process. The causes are part of the skeleton of the process and the effect is at the head of it.
• Devise: Standards, Policies, Implementation Strategies, Planning
• Brainstorming: The main objective is to find as many ideas as possible with which to respond to a specific challenge. Whenever we have the opportunity, we must build on the ideas that others are saying, to avoid turning them off. Generating an enhancing effect on them.
• Brainwriting: Brainwriting is a mixture of two terms, brain and writing. Thus, the process involves participants taking out a sheet of paper and starting to write. Letting, as in a brainstorming process, the ideas flow forcefully.
• Drawstorming: Contrary to popular belief, we all have a greater capacity to draw than we think we do. And doing so activates different places in the brain than many of us are used to.
• REFINE/PROTOTYPING: Test what was devised in the previous step in the least disruptive way possible.
• Value Proposition Canvas: A Value Proposition Canvas is a template designed to align the needs of a set of users with the characteristics of the changes we are going to offer them. Seeing reflected the final idea of the change to be implemented.
Application to cybersecurity.
Having seen these techniques, could they be applied to cybersecurity, considering that we are an area that needs to constantly improve infrastructure and changes within a given environment? How could we transfer this same method?
In order to understand this, we must understand that thinking about security can imply innovating with respect to the habits with which users, developers and technicians handle the company's most important assets. Therefore, it always implies a cultural change in most cases where special attention must be paid to things that we did not know before.
While there are several use cases such as correcting a failure, implementing a new policy, penalizing the misuse of information, making users aware, developing in a secure way, and a long etcetera. We could start with one of them to evaluate the feasibility of this method applied directly.
Example: The implementation of a safe development culture within a DEVOPS team.
• On the above point there are usually many differences of concept, if we go down the normal route, the security analysts tell the development team to protect against the problems (or vulnerabilities) described in the OWASP top 10.
• This may be rejected or we may receive a response like the following: We have a continuous integration process and use an X platform.
• As a result of these types of responses as cybersecurity professionals we lose motivation and we get into the mindset of simply demanding something without first understanding how we could carry it out and what strategy we can use.
• So we turned to Design Thinking:
• Empathize: : Understand how the development team works, understand how long their tasks take, how we can incorporate the new concept into their day-to-day so that it gradually mutates into what we want as security.
• Define: We simplify where the main possibilities are.
• Ideate: We open the game to think about the alternatives we have to get into their process.
• Refine and Prototype:Monitor this change to see if there is any substantial difference.
Conclusions
As professionals we should propose to free ourselves from the statement "Why would we have to empathize if we already know what are the things to improve", this type of absolute statements cause us to lose that empathy that we want to generate in the user as a respectable and collaborative area. So removing the focus on absolute palliative measures and changing it for a real interest could be of great help for the person who is on the other side to want to cross over to collaborate with us, as well as to focus on the whole development of an idea and how it ended successfully, understanding the ways of handling the other points of view and how a successful implementation was devised when implementing a new standard or a new point of change. Working on empathy as the next task to be seen on the horizon.