⦁ NIST SP 800-115, “Technical Guide to Information
Security Testing and Assessment” (2021)
⦁ Siddharth Chowdhury, “Perceptions of purple teams
among cybersecurity professionals” (2019)
⦁ Scythe, “Purple Team Exercise Framework (PTEF)“
https://github.com/scythe-io/..
⦁ Namosha Veerasamy, “High-level Methodology for
Carrying out Combined Red and Blue Teams” (2009)
⦁ Justin Warner, “Common Ground Part 1:
Red Team History & Overview” (2016)
https://sixdub.medium.com/common-ground-part..
In the field of cybersecurity, we recognize the term Purple Team although we are not always clear about its scope or purpose within the cybersecurity objectives. In this post we will make an introduction to the different types of Purple Team exercises, their scope, how these are developed according to the needs of each organization. And how we can differentiate it from other types of protective functions.
Context
Offensive and defensive cybersecurity operations are known as Red Team and Blue Team. Concepts adopted from the military field (of course) introduced in the 1960s as concepts, although modalities used almost two thousand years ago (320 AD) always with the aim of simulating conflicts based on real war strategy rules to prepare for upcoming real battles.
The Red and Blue team approach was established as a form of interaction in which at least one party pretended to be an enemy. This idea has since been adopted in the cybersecurity domain to enable testing from an adversarial mindset through threat replication and the development of countermeasures based on the results of such testing.
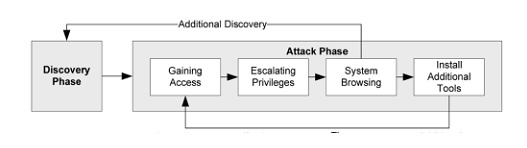
It is clear that the Red Team and Blue Team approach, which we can now consider traditional, provides good results, but presents some problems in its implementation when a medium or high level of maturity is reached in the operations of each of them.
One observation that emerges from the way each team operates and after analyzing deliverables, is that "The Red Team always wins", since it is practically always possible to detect some vulnerability to exploit, while the Blue Team is always "behind" and “tries to keep up". This disconnect between the approaches may be due in part to the lack of communication and the configuration of perspectives, but also due to the way operations are designed, they point to different, often contradictory, results, as the success of one looks like the failure of the other.
It is the opposite nature of the teams that generates this competitive perspective, which leads to secrecy between the teams and causes them to operate in isolation from each other. Among the undesirable results we find that the Blue Team progressively begins to build defenses to protect itself from the Red Team and neglects the real threat.
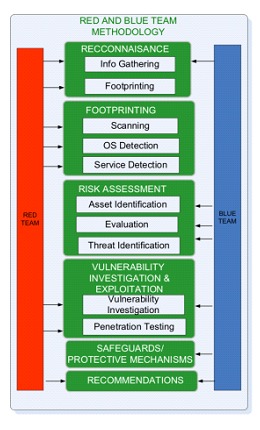
This is where the Purple approach has emerged, which is focused on using collaboration and information sharing to achieve the same objectives. An approach that, while not new, has been maturing and adapting according to the environments in which it is developed.
Not just a matter of colors
Typically, the concept of Purple that we recognize is nothing more or less than the combination of the Red Team and the Blue Team (as if they were pigments and not operations with high complexity and increasing challenges). It is here that we find limited definitions of the Purple Team such as "One team for small organizations that cannot hire people for defensive tasks and another for offensive tasks" or "A meeting between Red and Blue Team".
A Purple Team Exercise takes forward the principles of both Red Team and Blue Team to evaluate and improve the detection systems (and other aspects) of an organization. It focuses on both offensive and defensive tasks, which gives them a different perspective. Typically, penetration testing can be performed with the addition of in-depth knowledge of the assets provided by the defensive teams, allowing security to be evaluated from a different perspective.
This is useful to maximize the effectiveness and potential of the Red and Blue Team separately, but this approach also integrates cyber threat intelligence (CTI), vulnerability analysis and security architecture.
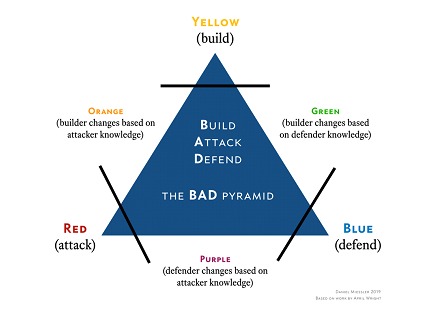
The idea of a team that combines perspectives aims to bridge the gap between offensive and defensive approaches by focusing on a more collaborative methodology. It can also help assess and mitigate unique threats, such as insiders, (which have one of the greatest potential for negative impact on a business).
We can say that in Purple Team operations, the testing is more targeted, as the offensive objective is to evaluate specific security controls while the defensive objective is to test specific preventive measures and skill sets simultaneously.
Scale and nuances
Considering "Purple" as "The continuous collaboration between cybersecurity teams with varied skills to test, measure and improve resilience to threats and attacks" we can find a variety of implementations for this type of operations.
We will now develop some methodological details for these operations as described by Scythe in their "Purple Team Exercise Framework (PTEF)".

Purple Team Exercises
A Purple Team exercise is a cybersecurity assessment with a complete understanding of the environment, attendees collaborate to design a threat, attack, detect and respond. The attack activity is exposed and shown to attendees as it unfolds in real time, the defense team in turn shares how each step is detected and how they respond accordingly. Purple Team exercises are hands-on, participants work together in open discussions on each attack technique and defense expectation to test, measure and improve people, processes and technology in real time.
These exercises are emulations of Tactics, Techniques and Procedures (TTP) driven by cyber threat intelligence that allow for the identification and remediation of gaps in the organization's security posture.
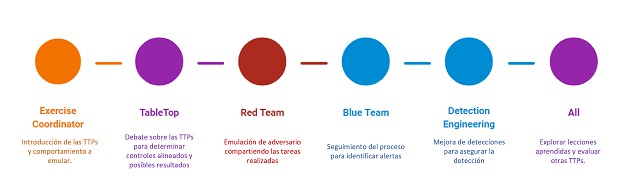
Operationalized Purple Team
The operationalized Purple Team is a virtual team, which is activated when new TTPs with impact to the environment are detected. These are analyzed, discussed and emulated to build and continuously improve detection and response.
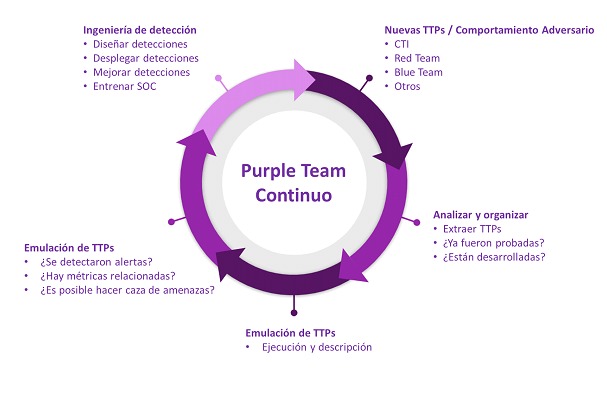
Dedicated Purple Team
More mature organizations are beginning to find particular value in these types of operations, forcing them to establish dedicated teams to perform these tasks. These specific roles vary from exercise coordinators to offensive or defensive profiles with collaboration-focused objectives.
Some conclusions
The development of Purple Teaming operations has its origin based on an operational and tactical disconnection between teams performing the same tasks that we can expect from a Purple Team. Their choice, as well as their effectiveness, will be fully related to the culture and maturity of the different offense and defense operations of the organization.
It is an interesting trigger (and not accidental) that the concept of "Purple Team" is a combination of functions typically performed by color-coded teams. Although as mentioned earlier the concept may be limited, this possibility of "mixing it up" gives us a kick-start to allow us to develop new skills from the tools we currently have. Finally, to improve cybersecurity.