The evolution of threat actors results in a need for more comprehensive security testing. Systems need to be prepared for real attacks and for this reason, for several years we have been using techniques and methodologies for offensive security tests, such as penetration tests or network team exercises, and we have even been able to combine this approach with detection and defense to develop purple team exercises.
Offensive assessments, in their various approaches, seek to exploit system, network or technical asset vulnerabilities and the assessment of system resilience (People, Processes, Technology) against attacks that are likely to be carried out by real adversaries (Red Team/Purple Team).
We distinguish two approaches:
The first approach is manual testing, which is typically more detailed and well-customized to the environment. This is a time-consuming process and requires advanced knowledge from cybersecurity experts. Commonly, a group of experts is required to perform a thorough test of the system, especially in a limited time frame.
Another approach involves automated testing to a greater extent, a highly adopted approach to decrease the time spent, allowing tests to be easily repeated. The tools used for this automation are generally based on threat research and are combined in solutions that are easy to deploy and simple to use.
Automating testing
We can summarize the landscape of existing solutions for attack automation as follows:
- Atomic Red Team
Comprised of a test suite mapped to the MITRE ATT&CK framework for testing environments quickly, portably and consistently. This collection is especially useful for evaluating the effectiveness of security environments in detecting and responding to various types of cyber threats. Each "atomic test" is designed to emulate a specific technique or behavior associated with advanced threat groups (APTs), allowing security teams to identify and remediate potential gaps in their defenses before they are exploited by malicious actors.
- Stratus Red Team
Tool designed to automate the emulation of adversary tactics and techniques in cloud environments, especially focused on platforms such as AWS, Azure and GCP. Stratus Red Team helps teams better understand and prepare against cloud-specific attacks, enabling continuous assessment and improvement of security strategies in these environments.
- Leonidas
Leonidas is presented as a platform for running attack simulations. Its main goal is to enable security teams to test and develop their detection and response capabilities. Unlike other tools, Leonidas focuses on providing a framework for writing, running and testing attack simulations, allowing users to customize and adapt tests to their specific needs.
- MITRE CALDERA
Developed by MITRE, "Caldera" is a framework for automating adversary operations. It is based on MITRE's well-known ATT&CK framework and allows security teams to automate the execution of adversary tactics and techniques to assess the effectiveness of their defenses. CALDERA is distinguished by its ability to plan and execute sequences of actions that mimic complex adversarial behaviors, helping to identify vulnerabilities and blind spots in security strategies.
It is also true that there are several tools designed to automate Red Team operations. These tools. Among others, we can mention:
Metasploit Framework: It is one of the most recognized tools for penetration testing. It offers a framework for developing and executing exploits against remote targets.
Cobalt Strike: Provides a set of tools for post-exploitation adversary emulation. Offers robust command and control capabilities to simulate advanced threats and prolonged attack campaigns.
Infection Monkey:An automatic security testing tool for networks. It simulates an attacker moving laterally through the network to identify vulnerabilities and flaws in security configurations.
Red Team Automation (RTA): A set of scripts designed to simulate known adversary techniques and help validate the effectiveness of security tools.
Pupy: An open source RAT (Remote Administration Tool), it offers a wide range of features and can be used for remote control of compromised systems, with post-exploitation capabilities.
BloodHound: Using graphs to reveal structure and security vulnerabilities in Active Directory environments, BloodHound helps identify attack paths that could be exploited by an adversary.
Automate vs. Continuous
If our teams already have an automated approach to security testing, we have the groundwork in place to start moving forward with a continuous approach. To clearly differentiate these approaches, we can say that test automation focuses on efficiency and consistency of results. Its purpose is to quickly execute a series of known attacks and exploitation techniques to identify vulnerabilities and security flaws in the environment, but this is not the same as sustaining continuous network team exercises, where it seeks to create a sustained and evolving testing program that emulates real and evolving threats. It focuses on adapting to the emerging tactics, techniques and procedures (TTPs) of adversaries, it is clear that the former is a prerequisite for the latter.
In order to carry out continuous Red Team exercises, we can mention some key elements:
Specialized Team:
A Red Team composed of offensive security experts, threat intelligence analysts, software engineers, and social engineering specialists.
Tools and Advanced Technology:
This will be our toolbox, we have already mentioned Metasploit or automation platforms such as MITRE CALDERA.
Threat Intelligence:
Which TTPs should we start with? Different subscriptions to threat intelligence services such as "Recorded Future" or "Crowdstrike" will allow us to obtain information on emerging behaviors relevant to our sector.
Legal and Ethical Framework:
Here we can mention established policies and procedures that delineate the limits of the exercises, respecting professional standards and ethics.
Adequate Testing Infrastructure:
For appropriate environments, we can have isolated test environments or production mirror networks to perform simulated attacks without affecting daily operations.
Incident Response and Escalation Plans:
The "How to follow" where we can mention defined procedures for escalating critical findings to the incident response team and high-level management.
Training and Continuous Awareness:
Regular training programs for the Red Team and awareness sessions for the rest of the organization.
Documentation and Analysis Procedures:
Systems to meticulously document each exercise, including tactics used, vulnerabilities exploited, and lessons learned. (Documentation and follow-up are everything in an ongoing process).
Evaluation and Continuous Improvement:
Periodic reviews of exercises to assess effectiveness and make adjustments based on emerging trends and changes in the organization's environment.
Effective Communication and Coordination:
Clear communication channels between the Red Team, the Blue Team and executive management to ensure organizational alignment and support.
Integration with Existing Security Processes:
Ensure that Red Team findings and lessons learned are integrated into risk management, incident response, and information security strategies.
In conclusion
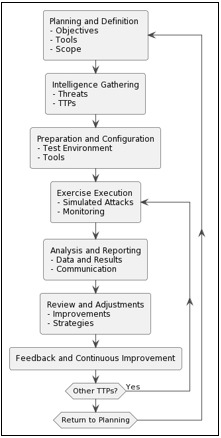
The lists are just some of the fundamental requirements for maintaining a healthy and harmonious ongoing network team exercise operation for the organization. On closer inspection, the differences between the two approaches are actually subtle, the main key is in the process. We can simply schematize it in the following diagram: