Sun Tzu and The Art of Cyberdeceit
When it comes to protecting our systems, it is important to take into
account all the options and tactics available. One of the protection strategies within the
framework of active cyber defense is called "Cyberdeception" or "Cyberdeception", which is
based on the use of techniques that aim to create a distraction or confusion to divert the
attacker's attention, hinder their operations and thus protect our assets.
We share with you some references to previous posts on active
cyber defense and a webinar to introduce us to cyber
crime..
Exploring a little on the subject we can see that this type of strategy is often referenced
to Sun Tzu's famous "Art of War", an ancient book of military strategy that has been used
for centuries to guide leaders in decision making and victory in war.
"If you know your enemy and know yourself, you need not fear the
outcome of a hundred battles."
This famous phrase is one of the only ones mentioned when referring to cyber deception, in
this post we will explore some perspectives specific to the Art of War and its correlation
in cybersecurity in particular with cyber deception techniques.
Principles
The "Art of War" is an ancient book of military strategy written by Sun Tzu, a Chinese
general and strategist. The book has been used for centuries as a guide to decision-making
and victory in warfare. Although the book was originally written for the military context,
its teachings have also been applied to other areas, such as business and politics.
Some of the principles of the "Art of War" include the importance of knowing the enemy (as
is well known), the use of surprise and cunning, and the need to maintain the initiative in
combat. The whole art of war is based on simulation and deception. These same principles
also apply in cyberengaño, where the enemy is a cyberattacker and the battle takes place in
cyberspace.
Approaches and correlation
"The principle of invincibility lies in defense, the possibility
of victory, in attack."
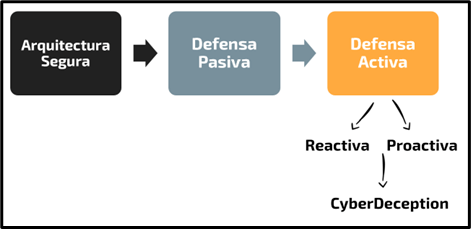
In this first approach we can also find cybersecurity strategies divided in two, on the one
hand the defense, where we refer to the architecture (where we protect from the design) and
passive defense techniques (firewalls, access controls, encryption, IDS, vulnerability
management, etc.) and, on the other hand, the attack strategies referenced in cyberspace in
the active cyber defense.
One of the main objectives of cyber deception techniques is to reduce the dwell time of an
attacker with access to protected environments (or within them). The "victory" will then be
the detection of this attacker and the subsequent tasks linked to securing the environment
in relation to this attacker.
"Experts in war observe the Tao and follow the laws, so they are
qualified to plan and execute victorious policies."
TAO refers to a concept fundamental to Eastern philosophy and is commonly translated as "the
way" or "the path". It refers to a kind of force or principle that guides the universe and
everything that happens in it. It is said that following the "Tao" means acting in
accordance with the nature of the universe, rather than trying to fight it or force it to
our will.
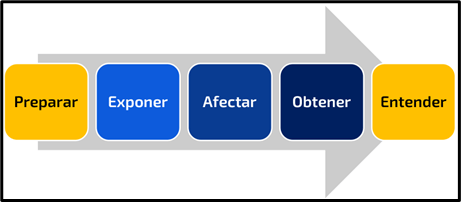
Mitre Engage proposes a series of actions, divided into strategic and engagement actions.
Engagement actions include in themselves the implementation of honeypots, accounts,
specifically designed information, complete systems. But all these elements are defined
based on the initial strategic actions of preparation (environment planning, threat
modeling, definition of operational objectives) and the last actions of understanding
(review, threat modeling, intelligence).
Just as cybersecurity must respond to the objectives of our business, cyber-danger
operations will only have good results if the planning is well done, this planning and
objectives will be going through the operation at all times, defining and limiting it.
"The capable general will offer an apparent triumph to the enemy,
he will organize him so that he can hit him where he wants to hit him."
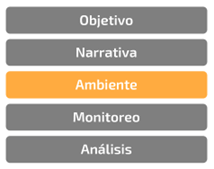
During the planning of a cyber deception operation, there will be information revealed that
will function as "supporting information", this non-essential information will give
guidelines to the attacker that will guide him along the defined path and serve as
validation to support other deception elements. These elements have a complexity that is
beyond the scope of technological understanding, they are defined by the cognitive response
of the adversary, which of course is at the end of the road human psychology.
"Keep your enemy in tension and wear him down. Create conflict
and division among his soldiers."
Other types of information planted in the environment during a cyber-breach operation will
be aimed at hindering, and wasting adversary resources. This information comprises a series
of elements that an attacker could potentially obtain, but do not provide any value during
the phases of an attack. In this type of items we could find for example files that look
tempting, encrypted with some weak algorithm using huge keys.
"The capable general fixes the battlefield to his enemies and
never lets them take him."
In a cyber-ransomware operation, one of the fundamental elements is the environment in which
the operation will take place. This can include networks and sets of servers/services, as
long as the attacker is in this environment we can let the operation develop. In these
environments, specifically designed, we must consider how the adversary will move and what
type of adversary we want to attract, threat modeling will be fundamental for this.
"Against the wise in defense, the enemy will not know where to
attack."
A specially shaped piece of false information will not only provide afiction for the
attacker, but will also raise the level of ambiguity with respect to all the elements that
can be collected in the different phases of an attack. The adversary will not only obtain
false elements, but, even detecting their falsity, will have a greater difficulty in
determining which of the collected elements are false and which are the real ones from our
environment. His operation will be tinged with a tone of doubt.
"If the campaign is too long, the soldiers become fatigued, the
weapons lose their edge and the morale of the army drops."
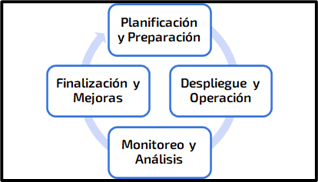
Each of the cyber deception operations will be conformed by phases, which have a beginning
for preparation and a closing for the definition of improvements, this allows each of the
elements involved during the compromise actions to be clearly defined and correspond to our
narrative. An indefinite extension would generate a series of traces and criteria in the
deception elements that would degrade their quality in front of an attacker.
"A sensible general will get his troops to stock up on the enemy,
because a hundred kilos of the enemy's supplies is equivalent to two thousand of his
own."
Cyber threat intelligence will deliver IoCs (Indicators of Compromise) that are aligned to
our environments, yet all IoCs collected in cyber-breach operations will be of a higher
quality and of course aligned to our environment, as we ourselves are effectively the target
of these attackers. Collection will then be one of the objectives of the operation
itself.
"Those who do not know how to have maps, do reconnaissance or use
local guides are unable to gain advantage of the terrain."
Building a narrative will be fundamental to generate a common thread for cyber deception
operations, the only way that deception elements can really camouflage themselves within the
IT/OT infrastructure is that they are aligned to the natural functioning of each component
found in the environment. Having a clear notion of how information flows between the various
services in the infrastructure will be the way to gain an advantage over our
terrain.
"To win a hundred victories in a hundred battles is not the
greatest skill. The greatest skill is to surrender the enemy without
fighting."
The active cyber defense strategy, as well as the battles, can give us a victory against the
attacker, that is why we make the preparation, design and deployment of the various elements
of operations. On the other hand, it is clear that these operations generate wear and tear
and require the acceptance of a greater risk, other objectives of cyber-deception actions
will be to provide information to the design strategies and passive cyber defense. It will
always be preferable to stop the adversary long before he is involved in cyber deception
elements. For our organization, this will be "winning without fighting".
"Just as important as having a prepared troop is knowing the
enemy's plans. Then you will know what strategy to use and what is not
appropriate."
Cyber threat intelligence will provide threat models aligned to our organization and its
objectives. Just as these models provide information for risk management, they will also be
of particular interest for all protection strategies. Within cyber-breach operations, these
will be critical in shaping the narrative and the various engagement actions. A honeypot
implemented without a real understanding of the rest of the elements of a cyber deception
operation will be like deploying an army towards the base of a mountain that an attacker
cannot get through, a waste of resources.
"There are roads not to be traveled, troops not to be attacked,
cities not to be stormed and territories not to be disputed."
Traditionally, cyber-attack operations were tinged with the "Hackback" concept, where the
target of a cyber-attack launches a direct offensive response against its aggressor. This is
natural when analyzing the origins of these operations from the military (of today and in
the past as we can see). In the context of an organization, this is not feasible and will
not be part of the engagement actions, the legal team (for example) may accompany the
definition of cyber-attack operations in order to have clarity on those roads that should
not be traveled.
"If the enemy's troops are stronger, avoid combat. "
Every cyber-rogue operation must include a series of "rules of the game", which contemplate
clear criteria for the closing of the operations. Each of these actions will have a series
of associated risks, this includes a responsibility which we will delimit by defining
critical conditions which will guide and limit the operations. An adversary, for example,
may obtain information that was not part of the planning.
Some conclusions
In summary, active cyber defense strategies especially cyber deception actions have many
points in common with Sun Tzu's "Art of War", we can see it in terms of strategy and the use
of the various elements of deception to protect against the enemy. This is no coincidence,
but the origins of cyber defense in general are completely aligned to the concepts, criteria
and of course strategies of traditional military defense.
By applying these principles to our technological environment, analogizing the different
factors, we are defining our cyber defense strategies. This understanding and applied
analysis will allow us to really maintain an advantage over attackers to protect our
networks and systems.




