- Unit42 - Medusa Ransomware Turning
Your Files into Stone
- https://unit42.paloaltonetworks.com/
The threat of ransomware has become a growing concern in the contemporary digital world, among the latest variants to emerge Medusa Ransomware stands out as one of the most insidious. This form of malware not only encrypts its victims' vital files, but also imposes multiple extortion, further complicating data recovery and generating serious repercussions for individuals and organizations alike. In this context, it is crucial to understand how Medusa Ransomware operates and the preventative measures needed to protect against this cyber threat.
Medusa and its multiple extortion
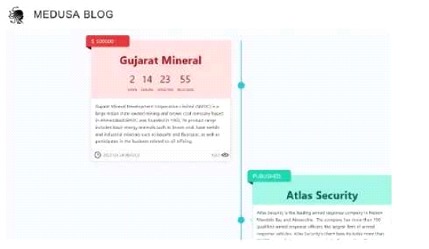
This is malicious software that spreads through the network carrying out ransomware attacks. This threat has undergone an evolution in its functions, since it initially used infected machines to carry out distributed denial of service (DDoS) attacks, but now it encrypts files and leaves a ransom note to demand payment in exchange for the information that has been encrypted. Through their website (hxxp://medusaxko7jxtrojdkxo66j7ck4q5tgktf7uqsqyfxxxxxxxxxxxxxxxxxxx[.]onion/), they publish their new victims and use a timer to give a specific deadline for payment; otherwise, all the information will be published or sold on dark web forums. One of its most known victims has been Gujarat Mineral, an Indian mining company.
The ransomware attack on Gujarat Mineral began with the infiltration of the Medusa malware through the company's network. Once inside the system, the ransomware proceeded to encrypt the company's critical files, preventing access to them unless a ransom was paid. This ransom was demanded by means of a note left by the attackers, which indicated the instructions for making the payment and the time limit for doing so.
The file encryption process and subsequent ransom demand left Gujarat Mineral in a delicate situation, as the company was unable to access its data essential to its daily operations. Although the specific details of the payment and the amount demanded have not been publicly disclosed, it is likely that the company had to take urgent steps to assess the situation and determine how best to respond to the ransomware attack.
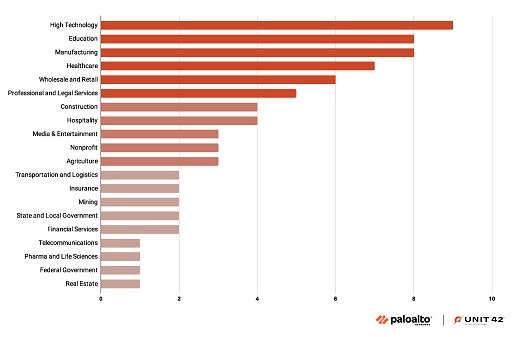
Medusa, not to be confused with Medusa Locker, is a ransomware strain that emerged in late 2022 and gained notoriety in 2023. This threat is characterized by opportunistically targeting a wide variety of sectors, including technology, education, manufacturing, healthcare and retail.
It is estimated that up to 74 organizations, mainly in the United States, United Kingdom, France, Italy, Spain and India, were affected by this ransomware over the course of 2023.
As ransomware continues to pose a significant threat, especially to technology, healthcare and critical infrastructure companies, the cybercriminals behind it are adopting bolder tactics. In addition to the practice of publicly exposing affected organizations, they are now resorting to threats of physical violence and even using dedicated public relations channels.
According to Unit42, Medusa not only has a PR team to manage its branding efforts, but also makes use of a public channel on Telegram called "information support," where files from compromised organizations are shared and can be accessed via clearnet. This channel was created in July 2021.
Main attack vectors
According to the U.S. Department of Cybersecurity and Digital Framework, the perpetrators of this malware exploit weaknesses in the Remote Desktop Protocol (RDP) to gain access to victims' networks. Once inside, they encrypt the victim's data and leave a ransom note in each of the affected folders, with clear instructions on how to contact those responsible for the attack. This note instructs victims to make their payments to a specific Bitcoin wallet address.
Another study by Cyble indicates that attackers exploit telnet services that are active on internet-connected devices. They use the ScanWorld function to carry out brute-force attacks. Once they have breached this stage, they inject an additional payload, following a specific set of steps.
Within the steps performed by the attackers, the following issues related to their behavior could be found:
• Resets the LanmanWorkstation service, allowing attackers to edit the registry freely.
• Eliminates forensic software processes
• Restart the machine in safe mode to avoid detection by security software.
• Encrypts victims' files with the AES encryption algorithm AES-256; the resulting key is then encrypted with an RSA-2048 public key.
To execute these tasks, in some more advanced cases, it uses LoLBins (Living Off the Land) techniques using legitimate software functionalities for malicious purposes, often mixed with regular traffic and behavior, making it more difficult to identify these activities.
Ransomware-related extortion
Multiple extortion in the context of ransomware refers to a tactic employed by cybercriminals to increase pressure on victims and increase the likelihood of obtaining the ransom payment. This form of extortion involves not only encrypting the victim's files, but also threatening to leak or sell the sensitive data in case the payment is not made within the set timeframe.
In the case of Medusa Ransomware, multiple extortion manifests itself through the publication of new victims on its website and the use of a timer to set a deadline for ransom payment. If the victim does not make the payment within this time limit, the attackers threaten to make all encrypted information public or sell it on dark web forums, which could have serious repercussions for the victim's reputation and security.
This multiple extortion tactic increases the pressure on victims and further complicates the situation, as they must deal not only with the loss of access to their data, but also with the threat of potentially damaging disclosure or sale of confidential information. As a result, victims are faced with difficult decisions and must carefully evaluate their options for responding to the ransomware attack and protecting their interests.
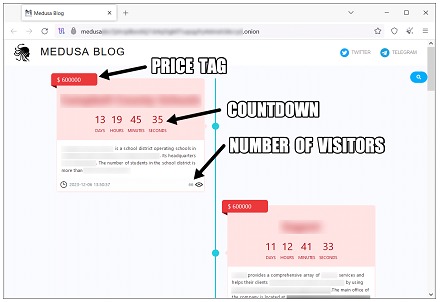
As a multiple extortion operation, the Medusa ransomware operator's advertisements include the following information points to pressure victims to pay the ransom (Source: Unit42):
Price: The amount shown is what affected organizations need to pay the group to have the data removed from the site. (Unit42 has observed that Medusa is willing to negotiate with victims, as are many ransomware groups. Payments made may not directly match the prices shown on the site.)
Countdown: The amount of time affected organizations have before the stolen data is publicly published and available for download..
Number of visitors: The number of visitors after the post, used in the negotiation strategy to pressure victims to pay.
Name and description of the victim: Identifiable information of the compromised organization.
News
Medusa ransomware, recently highlighted by analysts at Unit42, the research unit of Palo Alto Networks, is a growing threat in the cybersecurity landscape. This malicious group, known as the Medusa family, gained notoriety when it unveiled Medusa Blog in early 2023, marking a shift in its extortion tactics.
The Medusa family had a successful track record with Medusa Locker in previous years, but now, with Medusa ransomware, they have emerged as a prominent threat since early 2023, as we detailed in the introduction to this article.
A research conducted by analysts at Unit42 (Palo Alto Networks Research Unit) highlighted that it is a growing threat in the cybersecurity landscape. Another of the most prevalent cases today occurred during the month of September 2023, marking a change in extortion tactics, the massive attack affected 32 public sector entities in the country, seriously compromising the multinational that provides digital services to public and private organizations in the country.
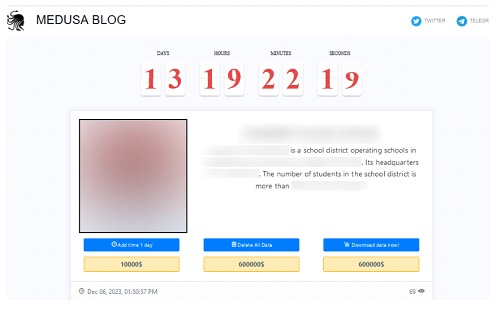
As evidenced in that case, the infection spread prevented the immediate restoration of the systems. The curious thing about this malware is that cybercriminals offer different recovery services, as a kind of billboard to obtain different "extortive spreading" services with greater and lesser impact in the case of a certain payment.
Companies that are breached can choose between different alternatives such as:
• Deadline extension
• Selective data deletion
• Complete download of sensitive information
• Among others.
Evidently, over time attackers are getting more creative to the point of offering this curious mercy disguised as less impact. Better known as Ransomware as a Service.
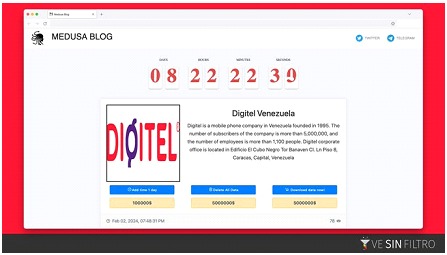
Recently, Digitel one of the most important telecommunications companies in Venezuela, suffered no more than a week ago a computer attack whose scope is unknown and although it rules out that its customers' data has been compromised, the information disclosed by the attackers suggests otherwise. Some organizations suggest that the company was recently attacked by the Medusa ransomware, currently asking for 5 million dollars to erase or download the data, otherwise it would be published shortly.
These data can be checked in the "Medusa Blog" by checking the modus operandi of this dangerous Ransomware:
Some protections and mitigations
Blocking the IOCs in the security devices of your infrastructure.
• Detect existing signs of the above-mentioned IOCs in their environment.
• Consider blocking or configuring detection for all URL and/or IP-based IOCs.
• Perform backups of the most critical information assets.
• Establish periodic backup policies that are stored outside the organizational network.
• Protect access to RDP-enabled systems.
• Ensure that applications, operating systems and antivirus software are updated with the latest patches available.
• Use caution with attachments and links in e-mails.
• Scan all attachments before opening them, using an antivirus that detects any suspicious behavior.
• Never follow instructions to disable security features if an e-mail or document requests it.
• Continuously educate users on computer security issues.
IOCs
Some related Hashes:
• FileHash-SHA256 - Win32:RansomX-gen\
736de79e0a2d08156bae608b2a3e63336829d59d38d61907642149a566ebd270
• FileHash-SHA256 - SUSP_XORed_URL_in_EXE
4d4df87cf8d8551d836f67fbde4337863bac
3ff6b5cb324675054ea023b12ab6657c0cce98d6e73e53b4001
eeea51ed91fdcf3d47a18712b6ba9c66d59677980
• FileHash-SHA256
7d68da8aa78929bb467682ddb080e750ed07cd21b1ee7a9f38cf2810eeb9cb959144a60ac86d4
c91f7553768d9bef848acd3bd9fe3e599b7ea2024a8a3115669
Infrastructure:
• Medusakxxtp3uo7vusntvubnytaph4d3amxivbxxxxxxxxxxxxxxx[.]onion
• Medusaxko7jxtrojdkxo66j7ck4q5tgktf7uqsqyfxxxxxxxxxxxxxxx[.]onion
Services and processes stopped by jellyfish:
Multiple services related to different data backup solutions, anti-malware software and multiple database engine services, among other services and processes, are stopped.