Lockbit Ransomware (Bleeping Computer)
- https://www.bleepingcomputer.com
/news/security/lockbit-ransomware-
disrupted-by-global-police-operation/
- https://www.bleepingcomputer.com
/news/security/police-arrest-lockbit-ransomware
-members-release-decryptor-in-global-crackdown/
- https://www.bleepingcomputer.com
/news/security/lockbit-ransomware-
gang-has-over-110-million-in-unspent-bitcoin/
- https://www.bleepingcomputer.com
/news/security/lockbit-ransomware-
returns-restores-servers-after-police-disruption/
More than 4 years of operations, about 1700 organizations affected, at least $100 million and about 200 affiliates, this complex scenario to manage found LockBitSupp last week with Operation Cronos through a vulnerability in PHP.
After the seizure, LockBit's data leak website showed:
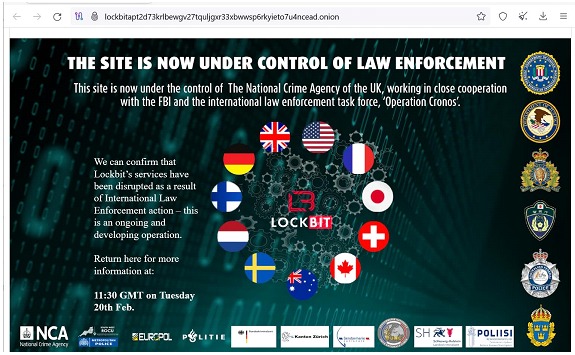
"The site is now under the control of the authorities. This site is now under the control of the UK National Crime Agency, working in close cooperation with the FBI and the international law enforcement task force, Operation Cronos."
The LockBit operation is run by the threat actor known as LockBitSupp which communicates using TOX messaging service. A message is now displayed on his account:
"FBI screwed up servers through PHP, backup servers without PHP can't be touched" message written in Russian.
LockBit and its supply chain
The LockBit operation as ransomware-as-a-service (RaaS) emerged in September 2019 and has since targeted a wide range of high-profile organizations around the world. The law enforcement involved also removed LockBit's affiliate dashboard and have added a message mentioning that LockBit's source code, chats and victim information, among other items of value to the investigation, were seized.
A special message was also left on the platform for affiliates:
"Law enforcement has taken control of the Lockbit platform and obtained all information contained therein. This information relates to the Lockbit group and you, its affiliate.
We have the source code, details of the victims you have attacked, the amount of money extorted, the data stolen, chats and much, much more. You can thank Lockbitsupp and their flawed infrastructure for this situation... we may be contacting you very soon.
Have a nice day.
Regards,
The UK National Crime Agency, FBI, Europol and the Operation Cronos Law Enforcement Task Force."
Thus, the material obtained in the digital break-in has begun to be used, not only to shape further investigations but also for the development of a tool to decrypt files previously encrypted by the LockBit Ransomware, which is now available on the No More Ransom.
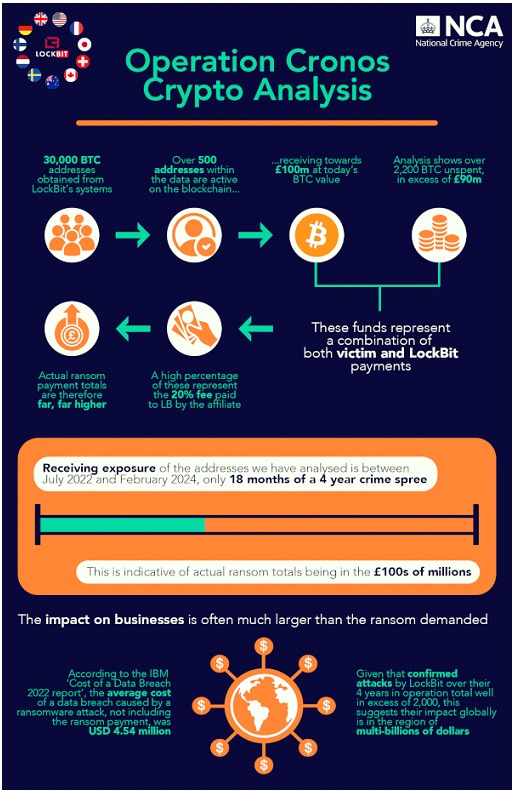
The researchers have also obtained information regarding "accounting" and crypto-assets valuable to better understand the scope of operations carried out by cybercriminals. Among these were found more than 2200 BTC (about $110 million as of today) unspent when the group's break-in occurred.
The team involved in the operation, after the seizure, was also able to use the same media used by LockbitSupp on its site as a channel to publish its findings, even making an offer to put a value on the question: Who is LockbitSupp?
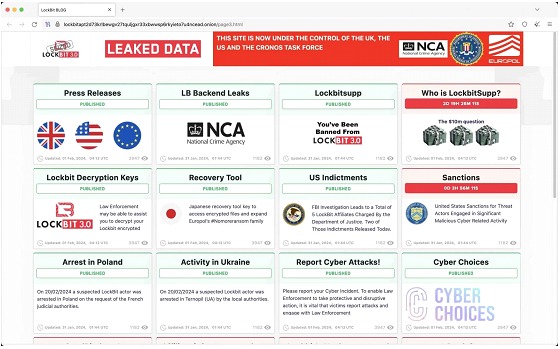
Operation Cronos
Operation Cronos is being conducted by a task force led by the UK's National Crime Agency (NCA) and coordinated in Europe by Europol and Eurojust. The investigation began in April 2022 at Eurojust, at the request of the French authorities.
During months of investigation, Lockbit's infrastructure has been compromised and is now under police control and consists of the main platform along with some 34 servers in the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States and the United Kingdom.
The U.S. Department of Justice has announced the disruption on its YouTube channel:
U.S. and U.K. Disrupt LockBit Ransomware Variant.
Conclusion
Operation Cronos is a sample of several collective operations in pursuit of the defense of digital ecosystems under attack by groups such as LockbitSupp. These actors are not exempt from making mistakes for which they are discovered, we could say that it has been as simple as a well-exploited vulnerability, but we would leave out months of work and dedication on the part of the teams involved in the investigation.
In this historical operation it is remarkable how it has sought to generate an impact on the various links of a threat actor. In the world of cybercrime trust is not something that is easily obtained and while the hit to LockbitSupp's assets may be significant, we can say that a more complex one to recover is related to their reputation and the risks of establishing operations with them in an "as a Service" model.
Will we see this threat group in action again? It is an answer that did not take long to be answered when about 5 days later they published an announcement about the "resumption of business" and a statement admitting "personal negligence and irresponsibility". 5 timers with new victims are published on its site.
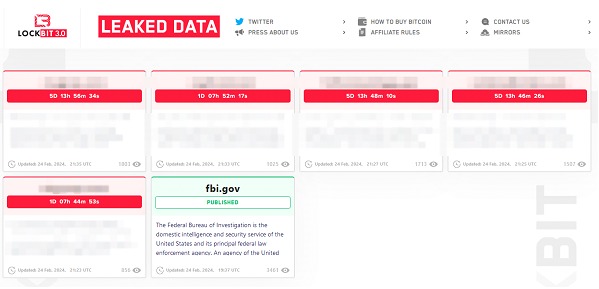
In this return, it also admitted the lack of updates on services using PHP (probably CVE-2023-3824). The group has applied an update and has made available a kind of reward in case of detection of a new vulnerability.
This long message thus seems to be damage control and an attempt to restore credibility, although only time will tell how this story worthy of a movie will unfold.