Fast Flux is a technique that involves the dynamic association of IP addresses with a single Domain Name. In this strategy, the rapid and constant change of IP addresses makes it easier for attackers to evade security systems. The key lies in the ability to change IP addresses quickly and efficiently, allowing the attacker's systems to continue to function without interruption. When an IP address is blocked, the system immediately moves to another address, ensuring the persistence of the attack. This tactic is commonly used in combination with Botnets, giving attackers more uptime to carry out their malicious actions.
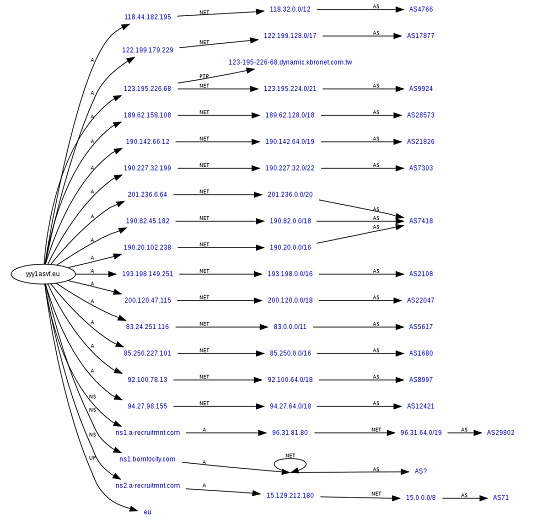
How it works
The Fast Flux technique works by dynamically and constantly associating IP addresses with a single Domain Name (ND). Its operation is described in detail below:
• IP-Domain Association: Fast Flux starts by associating multiple IP addresses with the same Domain Name. This domain is usually controlled by the attackers.
• Fast IP Changes: The distinguishing feature of Fast Flux is the fast and constant change of IP addresses associated with the Domain Name. This change is done quickly and automatically.
• Detection Evasion: When a security system detects and blocks an IP address used in the attack, the Fast Flux technique allows the system to adapt immediately, switching to another IP address. This process of continuous change makes it difficult for security systems to detect and block effectively.
• Persistence of Attack: By rapidly changing IP addresses, attackers' systems manage to maintain persistence in their malicious actions. Although an IP address may be blocked, the attack is not interrupted, as the system immediately moves to another available IP address.
• Use with Botnets: Fast Flux is often combined with Botnets, networks of compromised devices controlled by attackers. The combination of these two techniques allows attackers to have more uptime to carry out their malicious activities.
The Fast Flux strategy is executed by leveraging a load distribution technique called DNS round-robin, along with the configuration of a short time-to-live (TTL) for each associated IP address. This approach implies that some or all of the linked IP addresses are often web hosts compromised by attackers. These machines, located at the compromised IP addresses, will function as proxies for the attacker's original server. This process allows for a constant rotation of IP addresses, making it difficult to detect and block malicious activity, while ensuring the persistence of the attack.
Single Flux vs Double Flux
In a single-flux network, the authoritative name server of a fast-flux domain name continuously permutes DNS resource records with short time-to-live (TTL) values, typically between 180 and 600 seconds. The permuted records in the zone file include A, AAAA and CNAME records, and the disposition is often done by the round-robin method, using a record containing the IP addresses and DDNS names of compromised hosts.
It is already difficult to block a domain and trace the source of malicious activity, but Double Flux adds another layer of DNS flow, making it even more complex. During fast double flux, the IP address of the authoritative name server is also changed frequently. In technical terms, this means that both the domain's DNS A records and the zone's DNS NS records are updated regularly.

Malicious cases
Attackers use the Fast Flux technique for a variety of reasons, taking advantage of its dynamic and evasive characteristics to carry out various malicious activities. Some of the most common uses of Fast Flux by attackers include:
• Detection Evasion: Fast Flux allows attackers to evade detection and blocking systems by rapidly changing the IP addresses associated with a domain. This makes it difficult for security solutions to identify and block malicious activity.
• Persistence in Attacks: The ability to constantly change IP addresses guarantees persistence in attacks. Even if an IP address is blocked, the attacker can continue its operations without interruption, defying mitigation attempts.
• Malicious Content Distribution: Attackers can use Fast Flux to distribute malicious content, such as malware, phishing or fake landing pages. By rapidly changing IP addresses, they make it difficult for security services to block access to compromised sites.
• Botnet Hosting: Fast Flux is often combined with Botnet hosting. Constantly changing IP addresses make it difficult to identify and disable Botnet nodes, allowing attackers to maintain control over their networks of compromised devices.
• Ad Fraud: Attackers can use Fast Flux to drive traffic to fraudulent websites or to engage in ad fraud schemes, generating fraudulent revenue through fake clicks or ad impressions.
• Infrastructure Obfuscation: Fast Flux can be used to obfuscate the attack infrastructure, making it difficult for security researchers and analysts to trace and understand the server network used in an attack.
• Distributed Denial of Service (DDoS) attacks: By rapidly changing the IP addresses used in a DDoS attack, attackers can complicate mitigation efforts by making it difficult to identify and block sources of malicious traffic.
• Traffic Diversion: Attackers can use Fast Flux to divert legitimate traffic to malicious servers, compromising the privacy and security of end users.
Protection strategies
Avoiding Fast Flux can be challenging due to its dynamic nature and its ability to bypass conventional defenses. However, there are some strategies that can help mitigate the risk and protect against this type of technique:
DNS Traffic Monitoring:
Implement DNS traffic monitoring solutions to detect unusual patterns, rapid IP changes and behaviors associated with Fast Flux.
List of allowed domains and IPs:
Maintain an up-to-date whitelist of trusted domains and IPs, blocking access to those not on the list to reduce the attack surface.
TTL configuration:
Adjust the Time to Live (TTL) of DNS records appropriately to balance system efficiency and responsiveness to rapid changes.
Layered Security:
Implement layered security measures, such as firewalls, intrusion detection systems (IDS) and anti-virus, for a comprehensive defense.
Threat Signature Updates:
Maintain up-to-date threat signatures in security systems to recognize patterns and behaviors associated with Fast Flux.
Personnel Training:
Educate users about social engineering and phishing tactics, as Fast Flux often combines with these threats to infect systems.
Forensic Traffic Analysis:
Perform forensic analysis of affected traffic to identify patterns, IP addresses and domain names used in the attack.
Collaboration in Security Communities:
Participate in threat intelligence sharing communities to obtain up-to-date data and assist in identifying Fast Flux tactics.
Malicious Activity Monitoring:
Establish continuous monitoring systems to identify and track malicious activity, which may provide additional clues about the presence of Fast Flux.
Domain Name Analysis (DNS):
Analyze the domain name patterns used in the Fast Flux technique to identify possible connections and variants used by attackers.
Coordination with Service Providers:
Collaborate with ISPs and other relevant providers to share information and take action against malicious infrastructures.
Conclusions
Fast Flux types, either Single Flux or Double Flux, represent advanced strategies used by cybercriminals to make their malicious activities difficult to detect and mitigate. In a Single Flux environment, the continuous permutation of DNS records with short TTLs complicates domain blocking and tracking of malicious activity. Double Flux, meanwhile, adds an additional layer of complexity by frequently changing the IP address of the authoritative name server, making it even more difficult to identify the source of the attack. Effective protection against these tactics requires a comprehensive approach that includes active monitoring, regular security updates and collaboration in threat sharing communities.