During the progress of an attack, adversaries will look for the shortest paths, the cheapest alternatives and the highest return on investment, generally translated into impact for their victims, this has led cybercriminal groups to focus on specific environments such as virtualization environments like VMware ESXi, Hyper-V among others. Data encryption in these environments directly represents the loss of large volumes of data and the disruption of large-scale operations in the environment.
Recently, there have been cases of Panera Bread and Omni Hotels, two U.S. chains, which although from different sectors (Bakery and Hospitality) were affected by a variant of ransomware that encrypted the virtual machines of the organization, in both cases although the data was restored, it took days or weeks to restore all services leaving disabled internal services that supported operations (such as access to rooms) as exposed services such as websites or applications, the impact to the operation and image of the organization is not solved with the backup of the data.
SEXi Case
IxMetro Powerhost, a Chilean hosting and data center service provider, was the victim of an attack by a new ransomware group called "SEXi". (Sexi as a pun on ESXi). PowerHost is a company that offers hosting, interconnectivity and data center services, with a presence in the U.S., South America and Europe.
Customers were notified that they had been the target of an attack during the early hours of Saturday morning (the preferred time for this type of attack). This incident resulted in the encryption of some of the VMware ESXi servers used to host customers' virtual private servers. Hours after the incident, it was reported that it might be impossible to restore the servers, backups were also encrypted.
During negotiations to obtain a decryption key, the ransomware gang demanded a payment of two bitcoins for each victim, a sum that PowerHost's CEO estimated at $140 million.
"Since the beginning of the problem, we have been in contact and collaborated with several security agencies in various countries to determine if they were aware of this ransomware. All the information we have gathered indicates that these are new variants with a very high level of damage. Personally, I negotiated with the hijacker, who demanded an exorbitant amount of bitcoins per customer: 2 BTC per customer, which added up to about 140 million. However, even if we could raise the required amount, would it really help us? The unanimous recommendation of all law enforcement agencies is not to negotiate, as in more than 90% of cases criminals simply disappear after payment."
Ricardo Rubem, CEO of PowerHost.
A quick analysis of the message could tell us about good practices in terms of collaboration, an analysis of the samples that is not conclusive in reference to other cases and negotiation as the last alternative, although without giving clarity on the next steps.
On the other hand, the company's response plan has provided new virtual private servers (VPS) for those customers who still own their website content, so that they can restore.
SEXi operation
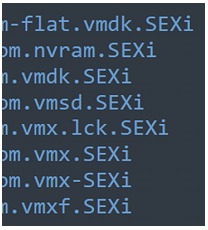
According to CronUp cybersecurity specialist German Fernandez, PowerHost the identified ransomware adds the .SEXi extension and generates ransom notes called SEXi.txt.
All the files of the virtual machines, including configurations and virtual disks, are included in the affectation.
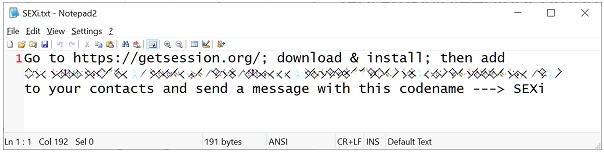
As for the infrastructure of the ransomware operation, no particular features are currently recorded. The ransom notes simply instruct victims to download the Session messaging application and make contact via the address provided.
SANS instructor Will Thomas found other variants that have been in use since February 2024, these variants use the names SOCOTRA, FORMOSA and LIMPOPO.
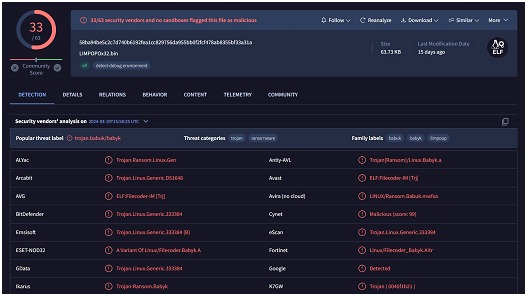
In the LIMPOPO sample shared by Thomas, it can be seen that they were created using the leaked source code of the Babuk ransomware, which has been used by numerous ransomware gangs to create ESXi encryptors. Windows encryptors related to this operation were also found to be created using the leaked source code of LockBit 3.0.
It is unknown whether the attackers are extracting data to extort companies with double extortion tactics via data breach sites. However, since this ransomware operation is very recent, this situation could change at any time.
Conclusions
In accordance with this incident, the Chilean government's CSIRT issued an advisory warning organizations to upgrade VMware software to the latest versions and offered advice on how to protect servers
While attacks targeting virtual machines are nothing new, the attacks over the past month continue to demonstrate that these are critical IT systems that must be adequately protected to avoid disastrous disruptions.