Industrial Revolution, one of the remarkable events that we learn about when we study history, not only focusing on the event itself, but also on how society was affected by these changes, causing changes in the way of working as well as in culture and in daily life. The arrival of the steam engine at that time installed the idea that sooner or later the human being was going to be replaced by machines, but it also gave us an acceleration in production, allowing the transport of goods over long distances.
The point is that over time several advances oriented towards the optimization of all these manual processes that the human being required to do predominated. In these industrial revolutions, there was not only one revolution, there were several changes that over time were considered important milestones that changed the operations.
How have operating technologies evolved?
It is estimated that throughout the ages there were four great industrial revolutions and that we are currently about to experience a fifth industrial revolution, for them to be classified as such, the change that must occur must be associated with 3 important factors: economic, social and technological.
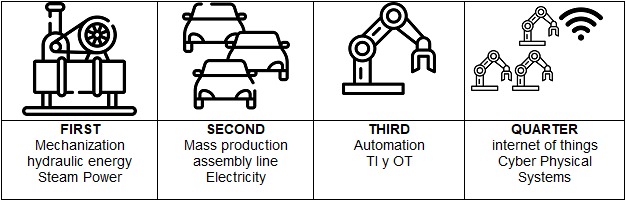
As we see in the small descriptive table, with the third industrial revolution we began to talk about Information Technologies and Operation Technologies, regarding the last one, it refers to processes that are automated with specific instructions to execute specific tasks. Eg: A robot arm that spreads jam on bread.

As you will see, these are simple and clear defined tasks. At that time, a certain robotic arm was dedicated to receiving instructions but with the difficulty of maintaining consistency throughout the process of creating something. In summary, the need to be created with the virtue of being available at all times, which is why in its design process this automatic system was not created with the security perspective in mind.
The problem of OT (OT vs IT)
Information technology is characterized by the application of telecommunication equipment aimed at processing data, we usually use it in various fields, on the other side, operations technologies are dedicated to detecting or changing physical processes through monitoring and control. So in this small difference we find that need for availability that we talked about above. We could also evaluate and divide them into categories in a small comparative table.
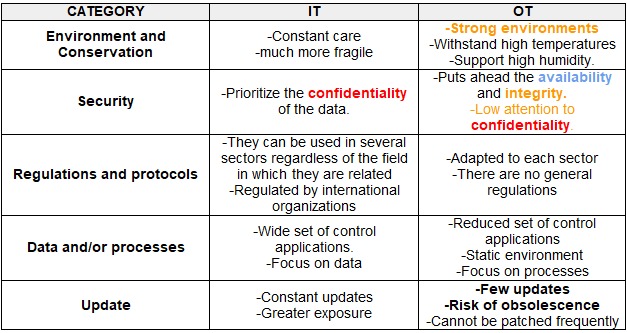
Until now, no one had thought that in the future there would be a combination of the two technologies to provide better performance in production. Until recently, OT (Operation Technology) environments were not connected to IT (Information Technology) environments, but current trends tend to connect these automatic systems together, which means there is constant communication between devices not intended for security and systems that are designed to provide security. If we extract some interesting visions from the painting, we can highlight the following famous phrases;
An OT system possesses:
⦁ low attention to confidentiality
⦁ Puts ahead the availability
⦁ Static environment
⦁ Few updates
That is where we find the perfect brew for an insecure system and the main problems that lead to resistance in evolving towards the new concept that Industry 4.0 brings with it, the Cyber Physical Ecosystems
What is a Cyber Physical Ecosystem?
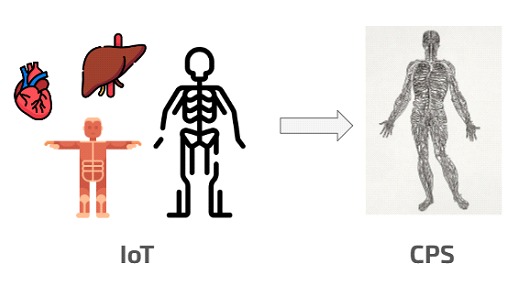
A Cyber Physical Ecosystem (CPS) is a group of devices that integrates computing capabilities, storage, communication and interaction with any physical process.
A CPS is connected to all these IoT components as a skeleton that supports the interactions. This system is permanently connected to the internet to correctly synchronize activities. The CPS would be the central nervous system that communicates through the internet with all the IoT devices that make it up.
But what happens when this interconnection occurs between legacy devices? What also happens when this system is managed by a human who doesn't have a correct vision of its limitations?
This interconnection associated with Industry 4.0 brings us vulnerabilities associated with their composition. Perhaps it brings us the same old vulnerabilities creeping in from interconnected devices and the carelessness that people have when handling them.
Possible CPS-oriented Attack Vectors
This connection, referenced in the operation technologies, has a significant gap between them, it is estimated that there is a 15-year gap between IT and OT devices, if we add to this the great diversity of communication protocols of the devices in the OT world, preserving their security becomes a major challenge for professionals in charge of these issues.
To reference these cases we have STUXNET in 2010 aimed at a nuclear power plant and INDUSTROYER2. One of the biggest threats detected to these matters. Most are born from human error to the common failures of these interconnected legacy devices (victims of the 15-year technology gap).
Therefore, within these issues, we find the following list of the top attack vectors that could be useful for attackers and their respective potential solutions;
⦁ Software not updated: We are facing technologies that are not updated frequently, due to the impossibility of doing so. Since doing this implies that you have to restart the entire infrastructure.
Impact:
⦁ An attacker could take advantage of the lack of an upgrade to have the necessary time to expand the surface of his attack.
⦁ It could also be based on some previous system to design a strategy that allows you to remotely control the devices (think what would happen if physical devices are attacked and then used for various purposes, e.g. Nuclear Power Plant).
Possible solution:
⦁ Implement an update flow and the corresponding procedures in the event of a critical failure that allows remote code execution actions to be carried out on the component platforms of a CPS.

⦁ Perimeter-based security: Originally we thought that if our security perimeter was secure, there was no need to secure the company's internal platforms, such as our local area network.
Impact:
⦁ An attacker could take advantage of the lack of attention of an internal network, being able to intercept traffic between the critical communication points of a CPS to get hold of the data and/or manipulate the information at will.
Possible solution:
⦁ Correctly segment the networks within a company, to avoid the existence of multiple communication points that affect the interoperability of the components of our CPS.

⦁ Insecure communications and custom protocols : The absence of encryption or the trend towards the availability of the components of our ecosystem means that communications can be easily intercepted. Additionally, most of these networks use proprietary protocols, when having protocols made especially for the issue, it often happens that they have design errors and security flaws that allow the attacker to dialogue without problem with all the components;
Impact:
⦁ An attacker could take advantage of the lack of encryption to be able to capture traffic in plain text or, failing that, the absence of strong encryption.
Possible solution:
⦁ Implement secure protocols and in the event that our critical CPS network cannot be isolated from any network that does not need to interact with it.
⦁ Absence of established reference frameworks: All kinds of strategies and standards must be developed with the objective of enhancing the cybersecurity of devices in the Industry to combine them with the factory security measures of the devices themselves. Since they currently lack these issues;
Impact:
⦁ In the absence of an established reference framework, the implementations may be subject to the usual oversights of a bad implementation, e.g. If the instruction manual does not ask me for segmentation, I do not implement it. So an attacker could witness a lot more sloppiness than usual.
Possible solution:
⦁ If the standard does not exist, adapt to the best practices that best serve us to implement networks and/or systems that interconnect components. For example, the well-known CIS Benchmark and/or NIST regulations.
⦁ Unsafe design of machinery and sensors: The protection of devices and machinery should not be a concern after the fact. In other words, by the time the machines themselves are designed, they must already include safety measures. Cybersecurity and physical security to reduce risks.
Impact:
⦁ An attacker can take advantage of a design flaw by making the system behave strangely or in a way associated with their benefit.
Possible solution:
⦁ Think of measures that complement security from an approach that allows us to provide the greatest possible containment in the face of these failures.

⦁ Physical security at facility level: Last but not least, we must ensure that special attention is also paid to the safety of the facilities. Since if we add vulnerable and outdated devices to facilities we are facing an inconvenience that enhances the current vulnerabilities of the CPS that cannot be corrected due to the lack of the corresponding upgrades.
Impact:
⦁ An attacker can take advantage of a flaw by physically accessing the CPS components to execute whatever attack they need.
Possible solution:
⦁ Carry out physical security tests that reveal the current failures from that point of view, in order to later be able to solve them before any type of accident related to this point occurs.