Within the cybersecurity environment, virtually everyone has knowledge about what Phishing is, as well as the techniques that are considered mostly well-known. This generally involves sending emails with subject lines that may be of interest to the victim, leading them to fall into the trap, such as downloading files that compromise their privacy. However, we are not aware of other methodologies that, being not as straightforward as the one mentioned earlier, pose a challenge when it comes to detection and can indeed impact users with a much higher technical level. In this post, we will explore some of them.
Attacking advanced users
It is quite clear that when seeking an 'easy money' style attack, attackers will first attempt to target users with lesser knowledge in computer-related matters. This can provide them with a significant advantage in taking their initial steps within the target network, and from this initial entry point, they may proceed to escalate privileges or begin moving laterally. During this progression, there are certain difficulties, and often, it takes time to carry out all these tasks, which could be shortened if, as an attacker, one were to gain permissions over an account with higher privileges within the victim's environment, such as developers, technical support personnel, or server administrators, for example. However, this, of course, presents a much greater challenge, as it becomes more complex to make one of these individuals our victim due to their higher technical knowledge.
Now that we have given some context to the situation and the reason for this article, we can go deep into the most significant ideas regarding this type of attack.
Types of Advanced Phishing Attacks
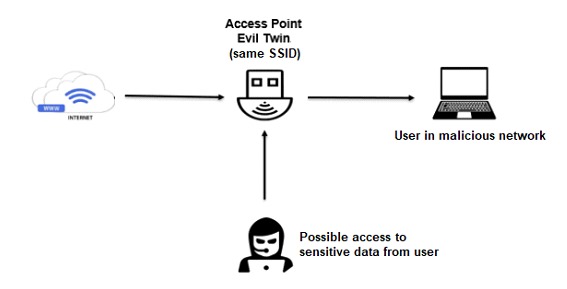
Evil Twin Phishing
This attack consists of a technique that can be used to target individuals with more knowledge, as it is more about deception techniques than technical issues per se. What does it involve? Creating a fake Wi-Fi network, to which a victim might easily connect and unwittingly share sensitive information within it. The danger of this technique lies in the fact that once a person has entered the fake network, all the information they share there, as well as any files they manipulate, will be sent to a server controlled by the attacker. The possibilities for the attack do not end there; the attackers could also gain access to the connected device, take control of the files on it, as well as important information related to log in credentials.
Even an advanced user could fall into this trap because it doesn't necessarily require direct technical knowledge to avoid it. This is because such attacks often occur in public places like cafés or restaurants, and considering that we are in an era where people are both 'Working from Anywhere' and working in physical offices, a momentary lapse of attention could make us victims of the mentioned attack.
Watering Hole Phishing
We can say that this attack is focused on initially understanding which websites a person or group of people, identified as targets by adversaries, access. Once the website focus with the highest traffic has been identified, it is then compromised. Subsequently, the victim(s) access the infected website and become compromised during their visit. To carry out the task of infecting the website, attackers typically identify vulnerabilities that could be exploited on the victim sites and use them to take control of the site.
The term 'Watering Hole' comes from the animal kingdom, where predators wait for their prey to gather at a watering hole before attacking them in a place of 'trust.' Similarly, victims are attacked and rendered defenseless on a site they regularly visit, where they would not feel unsafe entering at any time.
A real-world case related to this occurred in China in 2018, and what makes it noteworthy is that it happened at a national level. The attack was carried out by the LuckyMouse threat group (better known as APT27). In this attack, the mentioned group managed to inject malicious JavaScript code into government websites. This was achieved through the infection they performed in a data center using the Remote Access Trojan (RAT) HyperBro, which provided them with remote control and persistence over the affected systems.
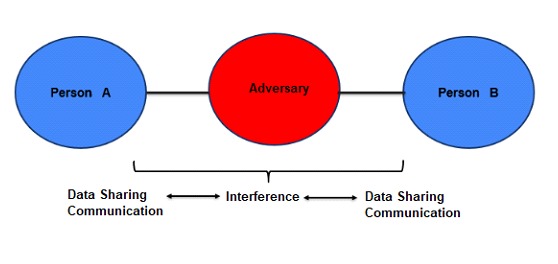
Man-in-the-Middle-Attack
This technique involves a type of attack in which an adversary interferes with communication or file exchange between person A and person B. The 'Man-in-the-Middle' attack is indeed challenging to detect, especially if it involves intercepting a conversation and the attacker has the ability to accurately impersonate each party, depending on their social engineering skills. This entire situation is more closely related to psychology than technical issues. However, if the target is a data transmission process, it may be somewhat easier to detect. Nonetheless, it's important to consider this attack because it can happen in our context, and waiting until it's too late to realize it's happening is not the best option.
Download Malicious Extensions
While there isn't a defined name for this procedure, this type of attack does exist and occurs occasionally. The process of the cyber-attacker involves creating an extension for a specific program with a particular functionality that the victim might find useful, and then inviting users to download it. This extension serves as the initial access point to the victim's computer.
As examples, we can think of a campaign designed to entice people to download an extension that allows them to automatically skip YouTube ads, or an extension that offers free PDF document conversion. An interesting aspect of these extensions is that they often receive positive ratings from users, and most users do not report any suspicious behavior.
This leads more people to continue downloading them, inadvertently putting their personal data and online privacy at risk.
Conclusions
We have reviewed some of the most dangerous phishing techniques that are prevalent today (of course, there are others). It's important to always keep in mind that attacks don't just happen through email; there are indeed other techniques that should be monitored and taken into consideration, whether we are cybersecurity analysts or users in sectors unrelated to IT. Being cautious when handling our work devices, personal information, or company data is key to avoiding falling victim to these attacks.