Cybersecurity has undoubtedly become an essential component for the survival of Organizations. On the other hand, cybercriminals are always looking to improve their techniques and the continuous advance of technology leaves us with a scenario where the threats faced are constantly evolving, making them increasingly complex to prevent and manage.
This is where threat modeling comes into play. But what exactly is cyber threat modeling? In simple terms, it is the process of identifying, understanding and prioritizing the potential threats facing an organization. In other words, it is a way to anticipate potential attacks, understand their implications and design effective defense strategies.
Through threat modeling, organizations can map potential attack vectors, understand their vulnerabilities and determine how adversaries might exploit them. This not only enables organizations to defend more effectively against cyberattacks, but also allows them to be proactive rather than reactive in their approach to protection.
This may seem like a daunting task, but with the right approach and implementation of the right methodologies, it can become a powerful tool in the battle against threats. We will explore in more detail how organizations can perform cyber threat modeling and what methodologies they can use.
Step by step
Modeling cyber threats for an organization involves understanding the weaknesses that the organization has, thereby identifying potential threats and then taking steps to mitigate or eliminate those threats.
We share here a simplified step-by-step for conducting cyber threat modeling:
Step 1: Identify assets
First, identify all the organization's assets that could be the target of a cyberattack. These could include servers, databases, networks, hardware, software, personally identifiable information, trade secrets, and any other "stuff" that has value to the organization.
Step 2: Assess weaknesses
The weaknesses of those assets are then assessed. This could involve conducting network team exercises, security audits, or other forms of analysis. You should consider both technical and human vulnerabilities, as cybercriminals often exploit both types.
Step 3: Identify threats
Once you have identified the threats based on these weaknesses, you must assess the associated risks. This involves considering the probability of one of these threats becoming a reality, estimating the impact it would have on the organization and determining the current capacity of the different teams to mitigate that impact. Risks should be prioritized here, for example, by considering those with the highest probability of occurrence and the greatest impact.
Step 4: Assess risks
Una vez identificadas las amenazas a partir de esas debilidades, debes evaluar los riesgos asociados. Esto implica considerar la probabilidad de que se haga real una de esas amenazas, estimar el impacto que tendría en la organización y determinar cuál es la capacidad actual de los distintos equipos para mitigar ese impacto. Se deben priorizar aquí los riesgos por ejemplo considerando los que tienen mayor probabilidad de ocurrencia y mayor impacto.
In some cases we could say that this is as far as threat modeling goes, but let's go a few steps further.
Step 5: Develop mitigation strategies
Strategies can be developed to mitigate the risks that have been identified. This could involve implementing new technologies, training teams, revising policies or processes, and hiring new staff. Both technical and human risks should be addressed here and each should be brought to a level that is acceptable.
Step 6: Implement and control
After developing mitigation strategies, they must of course be implemented and monitored for effectiveness. This involves performing some form of monitoring of security measures, regularly auditing security and making adjustments as necessary.
Step 7: Update and review
This is generally the most complex step, cybersecurity is a rapidly changing field, so it is essential to keep these threat models regularly updated. A periodic assessment to ensure that the organization is protected against the threats most relevant to each one.
Remember that this is a cyclic process.
Methodologies
There are several methodologies and frameworks for cyber threat modeling, some of the most popular are:
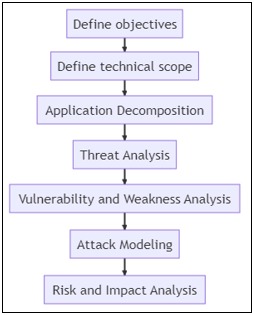
PASTA method (Process for Attack Simulation and Threat Analysis): This is a risk-based methodology for threat modeling. It involves threat identification, attack modeling, vulnerability assessment and risk analysis.
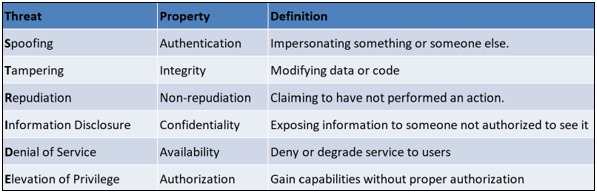
STRIDE Method (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of privilege): Developed by Microsoft, STRIDE is a threat modeling methodology for identifying security problems in software applications. It focuses on six threat categories:
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation): Developed by the Software Engineering Institute (SEI) at Carnegie Mellon University, OCTAVE is a framework for identifying and evaluating security threats in organizations.
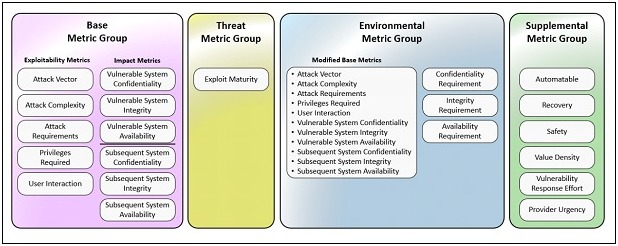
CVSS (Common Vulnerability Scoring System): CVSS is a framework for assessing the severity of security vulnerabilities in software applications. It provides a score from 0 to 10 to indicate the severity of a vulnerability. You can read in our previous post about versión 4
MITRE ATT&CK (Adversarial Tactics, Techniques & Common Knowledge): A framework used to understand the tactics, techniques and procedures (TTPs) that cybercriminals use to carry out their attacks. It can help organizations understand and prepare for advanced threats.
Choosing a methodology
It is important to remember that every organization is unique, so not all methodologies will be equally effective in all situations. Choosing the right cyber threat modeling methodology for your organization will depend on several factors, including your specific business needs, the maturity of your security program, available resources and your technology environment.
Here are some tips that may help you make the decision:
Understand your organization's needs and objectives: Are you trying to protect a particular application? Are you more concerned about data protection or business continuity? What types of threats are most relevant to your industry or business?
Consider the maturity of your security policy: Some cyber threat modeling methodologies require a high level of security maturity and can be difficult to implement if your security policy is still under development. On the other hand, others are more accessible and offer a good starting point for those just beginning to focus on cybersecurity.
Assess your resources: Implementing any cyber threat modeling methodology will require resources, time, personnel and budget. Be sure to consider these factors when choosing a methodology and its implementation.
Understand your technology environment: Each methodology has its strengths and weaknesses and may be more suitable for certain technology environments than others. For example, if your organization primarily uses Microsoft software, it may be useful to use the STRIDE methodology.
Research and learn from others in your industry: Often, it is helpful to see what methodologies other organizations in your industry are using. Not only can it provide you with ideas, but it can also give you insight into what has worked (and what hasn't worked) for similar organizations.
Finally, it is important to remember that there is no "one size fits all" when it comes to cyber threat modeling. You may find that it is more effective to use a combination of methodologies, or that you need to adapt an existing methodology to meet your specific needs.
Some useful links
https://learn.microsoft.com/en-us/azure/security/develop/threat-modeling-tool-threats
https://versprite.com/blog/what-is-pasta-threat-modeling/
https://handbook.gitlab.com/handbook/security/threat-modeling/