⦁ POLICY AS CODE (PAC) (Crowdstrike) (2023)
https://www.crowdstrike.com/cybersecurity-101
⦁ Emerging Tech Impact Radar: Security (Gartner)
In the current context, marked by rapidly evolving technology and increasing cyber threats, considering strategies such as "Policy as Code" is of value to keep up with the compliance. This approach facilitates the management of complex and changing IT environments, integrating seamlessly with DevOps and DevSecOps practices to ensure fast and secure policy implementation. This strategy also aids in regulatory compliance and human error reduction through automation. Its ability to quickly adapt security policies in response to emerging threats is vital to protecting critical information assets in an ever-evolving cybersecurity landscape, making Policy as Code an extremely valuable tool in any modern organization's security strategy.
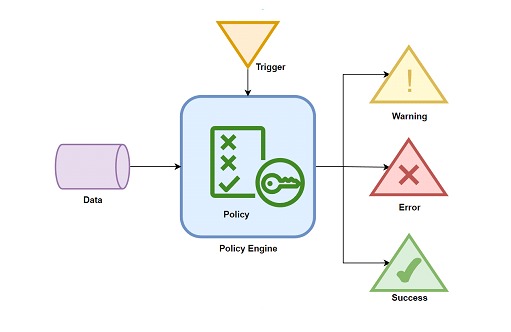
The basic components of PaC include the policy itself, consisting of a set of rules and requirements defined in a high-level language, the input data to check against the policy, and some form of query to determine the difference between the two.
Key features
We can list some particular characteristics of this strategy:
Effective Security Management: Implementing security policies "as code" ensures rigorous and consistent enforcement of security policies across the infrastructure. This is crucial to maintaining a secure environment, it also allows you to respond quickly to emerging threats.
Regulatory Compliance: "Policy as Code" facilitates compliance with data security and privacy regulations. By having policies defined as code, automatic and continuous audits can be performed, ensuring that configurations and practices are always aligned with legal and regulatory requirements.
Reduced Human Error: By automating policy enforcement, the risk of human error, which is a common cause of security breaches, is significantly reduced. This ensures that policies are applied consistently without relying on manual intervention.
Agility and Response to Change: The strategy enables security teams to quickly update and deploy policy changes. This ensures that the organization can respond in an agile manner to new vulnerabilities and threats.
Integration with IT Infrastructures: "Policy as Code" can be aligned with DevSecOps practices, integrating security into the development and operations lifecycle. However, it is also adaptable and can be brought into most of today's IT environments.
Transparency and Traceability: By having security policies stored as code in version control systems, a clear record is maintained of when and how policies have been changed. This is vital for auditing, forensic review and overall transparency in security management.
Scalability and Consistency: In large organizations or in cloud environments, where the scale and diversity of resources can be overwhelming, Policy as Code allows you to manage security in a consistent and scalable manner.
In conclusion, for a CISO or cybersecurity professional, "Policy as Code" is not just an operational efficiency practice, but an essential component of ensuring robust, agile and compliant security in the digital age.
Starting model
We can start from a YAML file, where we structure our policy as a series of rules. This will then be consumed by some system that will query the necessary requirements to confirm compliance with each point of the policy. Finally, this system processes the policy and its compliance, allowing to deliver detailed results.
These results can then be used for strategic decision-making.
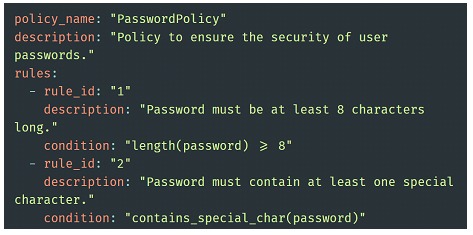
To ensure a smooth validation of these rules, without interfering in the processes, there will be an intense task to integrate them in each scenario, perhaps the simplest to see is directly linked to the software development lifecycle, but it is possible to take it to other areas.
Non-Technological Approach
Addressing policies that are not exclusively technology-related, such as an information security policy, through "Policy as Code" (PaC), requires a different approach that goes beyond automating some IT tasks.
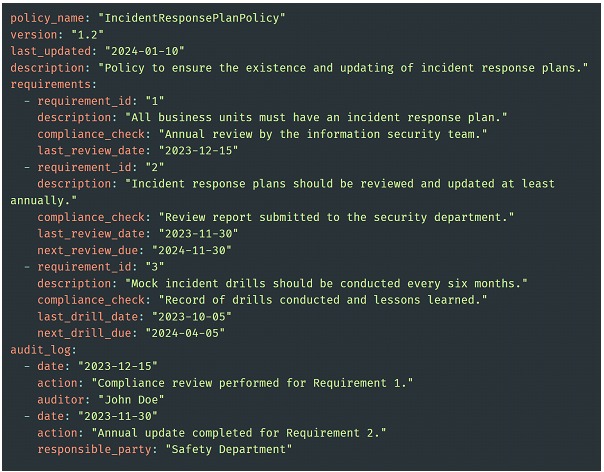
For example, for an incident response policy, they would translate non-technical requirements, such as simulation frequency or plan reviews, into codable parameters. Details such as review dates, responsible parties for actions and compliance schedules can be included in these requirements. Tracking and reporting tools are then integrated to automatically monitor compliance with these requirements. This could include automated alerts for upcoming reviews, or the generation of audit reports.
We separate some points that can be crucial to carry out this strategy:
Translation of Non-Technical Policies into Technical Rules: Interpret the non-technical aspects of the information security policy into rules that can be codified.
Integration with Governance, Risk and Compliance (GRC) Tools:Use GRC tools to automate the tracking and reporting of policy compliance. These tools can help map non-technical policy requirements to technical controls and automated processes.
Codification of Training and Awareness Policies: For aspects such as security training, an automated system can be developed to track and ensure that all employees complete the necessary training and awareness testing.
Integration with Organizational Culture: Incorporating PaC into the organization's safety culture requires special attention to integration. Each team must understand how their actions align with the codified policies and what the metrics are for defining compliance.
Ongoing Monitoring and Improvement: Establish an ongoing monitoring process to evaluate the effectiveness of implemented policies and make adjustments as necessary. This includes regularly reviewing policies to ensure they remain relevant and effective.
Conclusion
IImplementing PaC for information security policies requires an approach that starts from the automation of technical aspects with a deep integration into organizational processes and security culture. In doing so, it achieves not only greater efficiency and compliance, but also greater awareness and adherence to security policies throughout the organization. It is also true that its adoption requires a state of "agility" that in the long term is critical to sustaining the strategy.