⦁ Top Trends in Cybersecurity 2023 (Gartner)
⦁ Implement a Continuous
Threat Exposure Management
(CTEM) Program (Gartner)
Continuous Threat Exposure Management (CTEM) is a concept that addresses the limitations of most current risk management frameworks. This approach focuses on proactively identifying, assessing, monitoring and mitigating security vulnerabilities and flaws throughout the IT infrastructure before these issues become actual threats. Through CTEM, organizations can overcome traditional barriers to risk management, ensuring a more secure and resilient digital environment.
Defining CTEM
CTEM is an approach that involves the continuous identification and management of vulnerabilities within an IT environment. Unlike traditional approaches that focus on reacting to incidents, CTEM anticipates threats by constantly assessing the security infrastructure and adapting it to new vulnerabilities as they arise.
We will now analyze some key elements of this approach in order to give it concrete form.
Technologies in CTEM
Around technology, we can find scanning and continuous monitoring tools (vital for real-time identification of vulnerabilities through constant scanning of networks and systems). Risk management platforms, used to evaluate and prioritize those vulnerabilities detected, considering their potential impact and probability of exploitation. Finally, automation and orchestration is most important, focusing attention on incident response and routine security tasks.
People in CTEM
Among the professionals who play key roles in the CTEM). We find cybersecurity teams, responsible for monitoring security alerts, investigating incidents and implementing corrective actions (we could speak of a SOC and a CSIRT). Then, risk analysts, responsible for assessing and prioritizing vulnerabilities and risks, playing a key role in directing mitigation efforts. Finally, IT teams and developers, who have direct influence from patching to modifying software to address identified vulnerabilities, thus ensuring the integrity and security of the organization's systems and networks.
Processes in CTEM
An effective CTEM program can ultimately only be carried out through well-oiled processes. Initially, we already talked about the continuous identification and assessment of vulnerabilities, this is an ongoing process. Next we have to sort through risk prioritization and mitigation. We move on to the implementation of controls. Finally, training and awareness play a crucial role. These processes together form a strategy to proactively manage and reduce risks.
Key Benefits
Proactivity: By continuously monitoring the environment, vulnerabilities are identified and mitigated before they are exploited.
Risk Reduction: CTEM helps companies better understand their threat landscape, enabling better planning and risk reduction.
Enhanced Compliance: With increasingly stringent regulations, CTEM provides an approach that ensures ongoing compliance with data security regulations.
Bringing CTEM to the organization
Continuous Threat Exposure Management is not a tool, or a technology different from the ones we already have in place in our organizations, but a change of approach in the way risk management and the environment are integrated.
Some key points to get you started:
Continuous Risk Assessment: Implement tools and processes for the constant assessment of vulnerabilities.
Integration with Existing Tools: Ensure that CTEM integrates with existing security tools for complete coverage.
We can structure it as a cyclical process comprising five key steps, divided into two main phases: Diagnosis and Action. This cycle, when repeated, can ensure infrastructure coverage and continuous improvement. Each CTEM cycle encompasses all the steps, but its initiation can be driven by any element.
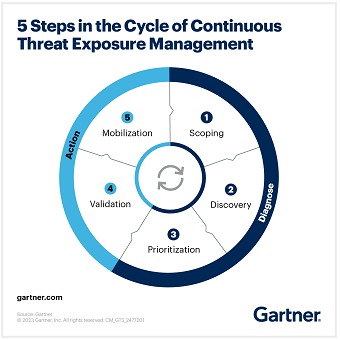
Diagnostic Phase - Identification and mapping of priorities and weaknesses:
• Scope: Mapping of the external attack surface, enumeration of digital assets and evaluation of their operational value, communicating this information to all those involved so that both technicians and executives understand which assets are critical.
• Detection: Focuses on discovering security gaps in environments, such as vulnerabilities and misconfigurations, assessing their risk and associating them with specific assets for more effective prioritization.
• Prioritization: This consists of identifying and addressing those security breaches most likely to be exploited, using an adversarial perspective and relating the findings to organizationally or business-critical assets.
Action Phase - The safety posture is evaluated and improved through corrective actions:
• Validation: This step has the objectives of determining the probability of success of an attack, assessing the potential impact of the attack, testing the effectiveness of existing detection and response systems.
• Mobilization: This refers to the creation and implementation of a remediation program that integrates automatic and manual solutions. This program is developed in collaboration with the technical and executive departments to ensure that operational and safety needs are truly aligned.
To achieve these objectives, methods such as Attack Surface Management (ASM), Continuous Network Teaming (CART) and Breach and Attack Simulation (BAS) are employed.
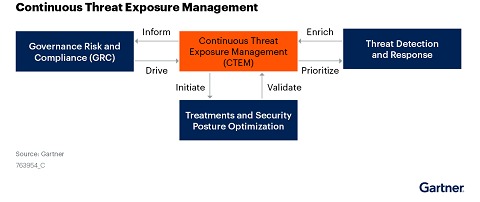
Gartner Perspective
Gartner's Emerging Technologies report shares that the impact of exposure management on existing technologies lies primarily in consolidating capabilities that support attack surface management, vulnerability assessment and cybersecurity validation. There is already a high degree of consolidation among exposure management technologies.
También se puede observar la convergencia de las herramientas del Blue Team y Red Team, lo que significa el surgimiento de plataformas de ciberseguridad que ya incorporan características integradas. Gartner predice que hasta 2026, más del 40% de las organizaciones, dependerán de plataformas consolidadas para realizar evaluaciones de validación de ciberseguridad.