The field of active cyber defense becomes relevant when we have a set of defensive measures in place for our environments that we can call "passive". This is where we find cyber deception strategies as a way to "change the game" for our organization's cyber defense. In this post we will develop some practical and limited examples on how to implement this strategy to the technological infrastructure without the need for an extensive budget and develop some more context on the variants to perform these operations.
From honeypot to the cyber deception
Fake targets
We have long recognized "honeypot" services as an element that we can implement in our environment to fake a real service and propose a kind of trap for a potential cyberattacker to use it and, in the best case, try to perform an exploit. Among these solutions, we can find some such as:
HoneyD: Virtual Honeypot Management Platform
DejaVu: Virtual Honeypot Management Platform
Kippo: Medium Interaction SSH Honeypot
Nodepot: Nodejs Honeypot
HoneyMail: SMTP Honeypot
HoneyThing: IoT (TR-069) Honeypot
Note: We will focus on the implementation of these types of solutions as defensive tools and not as tools for intelligence gathering or reconnaissance of cyberattackers (these are different approaches).
With this type of solution, if we add a new service to our infrastructure that has no other purpose than to be a trap, we can assume that the false positive rate will be low and any activity on it will be of value for threat detection.
Expanding the surface
In this type of technique, we attempt to increase the attack surface within our production services with the goal of creating traps that are fully rooted in our organization's real services. Traps are implemented in our production devices, which can be, for example, additional ports, unused functions, fictitious users, fake tokens, email addresses, or other functional elements that act as traps within the same services that are being used.
We can separate this type of techniques from the typical honeypots, considering that the latter are individual objects within the network, which we can separate more clearly.
Among these strategies we can find projects such as Canary Tokens from which we can manually generate our "Canaries" to distribute in the different spaces where we want to perform the detection.

Some examples include URLs that are specifically designed to wait for an improper connection.
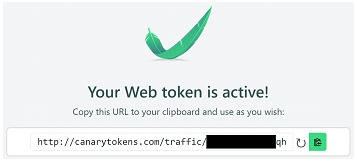
Example Web Token
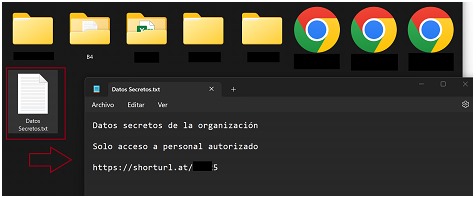
Web Token Implementation (via Short Url)
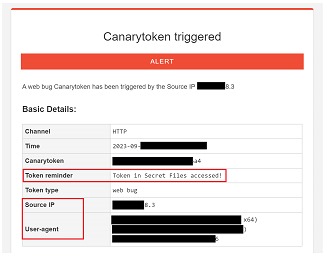
Alert by mail when accessing the web token
We can also find more complex projects such as PhantomFS which describes the design of a file system specifically developed to present different files to an attacker who does not use the correct interface.
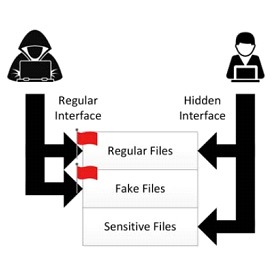
This allows the actual data of the productive services to remain "hidden" from the eyes of a cyber-attacker accessing the system through "common interfaces".
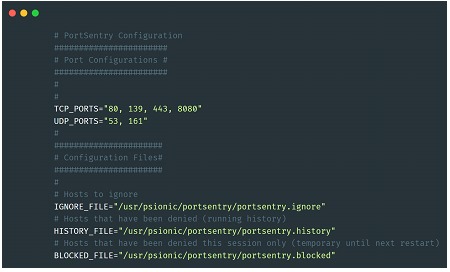
Finally, we present a tool that can be used both for deployment inside a production server and for creating a honeypot.Portsentry allows you to quickly and easily deploy a configuration of dummy ports and automate blocking responses or alerts.
Crumbs to return home
In a solid cyber deception strategy, "breadcrumbs" are considered a useful element. These will be pieces of information, traces that will provide information to the attacker to lead him to our various services that will be used as "traps".
For this purpose, we can use documentation specifically created for this purpose, which could contain, for example, the description of the use of servers, services or usernames that will eventually be our trap services. We can also think of other types of traces, such as simple credential hashes intentionally injected into memory, or simply logs that support our deployed traps as valid elements and resolve some kind of doubt that a cyberattacker can detect.br>
Some considerations and conclusions
Understanding the tools available for the implementation of a cyber deception strategy is quickly accessible, even among the options that we could explore for the deployment of a honeypot, we could even use the mere copy of our productive services with some tweaks. Whichever option is chosen, we will have a trap available on our network, and for it to be truly effective, we must first consider two aspects that we will refer to as "Look" and "Do".
Look
The art of deception, as well as social engineering or magic and any other practice where one of the parties is presented with a situation that is somewhat removed from reality, requires a real understanding of the interpretation of the "deceived" party. Underestimating a cyberattacker by using a tool without a real understanding of what we are doing can result not only in a lack of effectiveness of our activities, but also in a real increase in risks to our infrastructure, for example, by taking real control of a honeypot service from which new attacks on productive services are launched. Cyber deception activities need to LOOK real.

Make
Whichever option is deployed in our cyber-breach strategy, it will be necessary to articulate the alerts and logs (that one of our traps might generate) with specifically designed response procedures. The goals of cyber deception are not only to detect a potential cyber-attacker in our infrastructure, but also to understand their behavior and degrade or disrupt their operations.
We'll share some past posts where we introduced you to MITRE ENGAGE as a model for conducting cyber threat operations, or where you can get started on deploying aHoneypotand doing a little analysis of the data collected.