Social engineering continues to be a major concern in the cybersecurity world, as its tactics become increasingly complex and sophisticated. In this article, we will look at Social Engineering techniques that pose a challenge to Computer Security, while examining in detail the fundamental prevention strategies for dealing with them.
Introduction to Advanced Social Engineering Techniques
In recent years, Threat Actors have improved their social engineering tactics, making them highly effective tools for infiltrating corporate systems and networks. To date, it continues to be an extremely effective attack vector when trying to take control of accounts belonging to corporate environments, with the aim of moving later laterally within these networks, as well as to escalate privileges to achieve greater control over the victim environment.
Some of the techniques that have been observed include:
1. Targeted Phishing (Spear Phishing)
Targeted phishing is much more than just sending mass emails. Attackers research their targets in detail and personalize phishing messages to make them appear legitimate. On the other hand, they use victim-specific information, such as names of colleagues, current projects and language that could well be considered internal jargon, to build trust and increase the likelihood that sensitive company information will be disclosed.
2. Social Engineering through Social Networks
Attackers sometimes use social networks to gather information about potential targets. This allows them to build detailed profiles of individuals and their activities, which helps them create convincing and credible messages. Fake or compromised profiles are used to establish connections and gain the trust of victims, making it easier to extract sensitive information.
The remarkable thing about this point is that, since these are Social Networks, there is no economic cost that could be a problem for attackers when trying to apply this Social Engineering technique.
On the other hand, if this attempt is unsuccessful, the risk of having lost resources is practically nil.
3. Hardware and Device Social Engineering
In this case, adversaries move directly to Devices and Hardware, with the goal of gaining access to sensitive information. This may include the manipulation of physical devices, such as USBs or external storage devices. To effectively accomplish this task, attackers use Malware designed to steal data or compromise systems once connected.
To accomplish this task, social engineering is applied in this case, directly in a way that allows the attacker, who is inside the company, to abuse the victim computer, generating some kind of deception that allows him to carry out his objective.
Strategies to counteract these techniques
To mitigate the risks associated with these advanced social engineering techniques, proactive and preventative strategies must be implemented. Some best practices include:
1. User Education and Awareness
Users and staff should be trained to identify potential social engineering attacks. Training should include real examples and mock attacks to improve understanding of the threats and encourage caution when interacting with unfamiliar information and messages.
2. Implementation of Multifactor Authentication (MFA)
Multifactor authentication makes unauthorized access to systems and data considerably more difficult. By requiring multiple forms of authentication, even if an attacker succeeds in obtaining credentials, they will encounter an additional barrier that complicates their advance.
3. Ongoing Monitoring and Behavior Analysis
Generate detection and monitoring rules that monitor user and device behavior. This activity may well help identify unusual patterns or suspicious activity within the enterprise. On the other hand, behavioral analysis can alert about possible intrusion or manipulation attempts. For this reason, it is necessary to have elements that allow, from a monitoring approach, to generate the corresponding correlations of events to determine possible suspicious behaviors, both occurring and potentially probable.
4. Information Access and Disclosure Policies
It is important to establish clear and comprehensive policies on access to confidential data and protocols for disclosing internal and sensitive information. These policies should be enforced at all levels of the organization and reinforced regularly through training and periodic reviews.
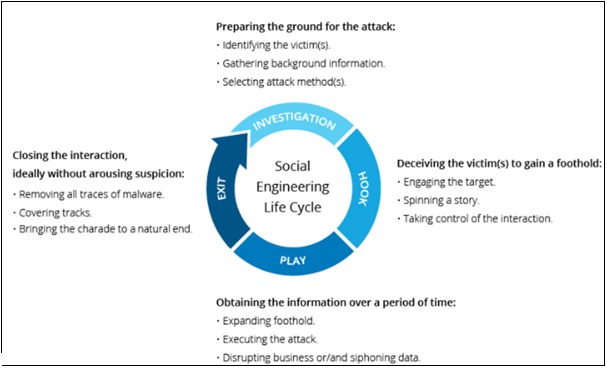
Conclusions
Social engineering continues to be a significant threat to enterprise security. With the continued development of social engineering and its advanced techniques, awareness and implementation of effective prevention strategies have become critical to protect against these attacks.
Organizations and cybersecurity professionals must constantly be vigilant and adapt to the changing tactics of adversaries to ensure the security of information and systems alike.
It is only through the implementation of the best practices mentioned above that organizations can strengthen their defenses and significantly reduce the risk of falling victim to social engineering techniques.