[1] BÖHM, Isabelle, LOLAGAR, Samuel.
Open Source Intelligence. Introduction.
legal and ethical considerations.
Agust 2021. Available at:
https://doi.org/10.1365/s43439-021-00042-7
[2] COLQUHOUN, Cameron.
A brief history of open source intelligence.
14 july 2016. Available at:
https://www.bellingcat.com/resources/
[3] KELLY, Heather.
Police embrace social media as crime-fighting tool.
CNN Business, 30 agust 2012.
Available at:
https://edition.cnn.com/2012/
[4] HU, Evanna.
Responsible data concerns with
open source intelligence.
14 nov. 2016.
Available at:
https://responsibledata.io/2016/11/14/
[5] FALCÃO, André, OLIVEIRA, Fabiana Oliveira.
TV Gazeta.
Available at:
https://g1.globo.com/es/espirito-santo/noticia/
[6] WALLOP, Harry.
Burglars using Twitter and
Facebook to 'case the joint'.
The Telegraph, 20 de julio de 2010.
Available at:
https://www.telegraph.co.uk/technology/
Before you get scared off by the "cheap sensationalism" used in the title, I would like to ask you to relax. Although the term OSINT sounds strange to anyone who has never heard of it, like the name of some futuristic robot out of Isaac Asimov's books, and the idea of "cybercriminals" makes us think we are being complicit in aiding and abetting masked villains, this is not the case. The idea behind the title of this article is to be sensationalist enough to draw the reader's attention to the dangers of uncontrolled information sharing.
Let's try to understand some concepts and why your selfie with your new job badge on a social network is more revealing than you might think. However, there is no reason to panic (yet) if you are clear on a few details.
In this article we will define some of these concepts, present use cases and some simple steps so that most individuals and organizations can learn how to protect themselves and make better choices about the type of content that is shared and made available on publicly accessible platforms.
Definition of Open Source Intelligence:

The term Open Source Intelligence (OSINT) originally refers to a type of intelligence source: any source that is publicly accessible. Intelligence sources exist to generate a certain amount of raw information, which will be processed and analyzed during the intelligence cycle [1] until it is disseminated for decision-making. In short, OSINT is intelligence produced by collecting data from public sources such as newspapers, magazines, journals, publications, blogs, websites, radio and television broadcasts, public documents, events, speeches, conferences, articles, libraries and, of course, the Internet and its social networks. The purpose of these collections can range from market research to criminal investigation or malicious cyber (or non-cyber) activities.
Some theorists on the subject have open discussions on the terms, and it is worth mentioning that due to concerns about the massive nature of the amount of data generated in social media, and the sensitivity and value of this data, there are those who advocate separating social media from OSINT sources to consider it as a unique problem of its own. In this sense, the term SOCMINT has emerged, which can be defined as "the analytical exploitation of information available in social media networks"[2].
In the world of cybersecurity, OSINT also refers to the practice of collecting information from open and publicly available sources, using digital tools and means, as this information will be available on systems, websites, corporate and home networks and the like. The focus of this talk is basically to show that this type of activity can be carried out for both legitimate and malicious purposes, and is difficult to detect until a real problem occurs, due to its mostly non-intrusive nature, as the information is in the public domain and can be accessed by anyone at almost any time. Data is a valuable currency in the digital environment, and with enough identifiable information about an individual or organization, it is only a matter of knowing "when" these currencies will be used to cause harm.
Casos de uso de OSINT
As mentioned above, open sources, especially social networks, contain an absurd amount of data on all kinds of topics, as well as data on individuals. Here are some examples of legitimate uses and real-life crimes where bad guys, not necessarily cybercriminals, used open sources not only to choose their victims, but also to map their behavior. The caveat is: actions triggered after collecting data from open sources can have consequences that go beyond the digital world and can cause material damage and even harm human life.
Examples of fair use:
• Military operations: In 2015, "the US military destroyed an Islamic State bomb factory just 23 hours after a jihadist posted a selfie revealing the structure of the building's roof, perhaps the most telling example of the military's use of OSINT for targeted operations". (Colquhoun, 2016)
• Cyber protection: Cybersecurity professionals can use OSINT proactively to collect and understand attacker behavior and act early to identify potential threats to their infrastructure.
• Public safety: "Police check and collect public information and sometimes create fake identities online to get closer to suspects and view more data" (Kelly, 2012).
• Pentesting and ethical hacking activities: Collecting information from open sources is an important part of legitimate penetration testing, ethical hacking and red teaming activities. Through collection, practitioners can enumerate weaknesses so that an organization can understand the level of risk and exposure it is at and correct problems.
Malicious actors, for their part, can use OSINT for a variety of purposes, and will not always be linked to cyber-attacks, as mentioned above. Examples of malicious use of OSINT are:
• Cyberbullying: A quick Google search can reveal reports of victims who are or have been bullied on their social media profiles.
• Social Engineering and Human Intelligence (HUMINT): Criminals collect data and personal information from potential victims in order to set up emails, SMS and even phone calls, making them believe they are a legitimate contact due to the profusion of details in the messages and calls and increasing the chances of success. This results in bank fraud with financial losses, data theft and other problems.
• Preparing for cyber-attacks on organizations: Criminals non-intrusively collect data on known technologies, systems, applications, employees, ways of working, routines, available job offers and anything else that could be useful to carry out an attack. It is becoming increasingly clear why it is not a good idea to post a picture on LinkedIn showing your employee badge, right?
• Common offenses:
• In 2022, Brazilian police identified a group that robbed houses in luxury condominiums in several Brazilian states. This group used to enter the houses when the owners were away and steal valuables such as jewelry and cash. According to the police chief in charge of the case, the group collected information about the victims on the Internet, through social media and data leaks. They knew exactly when residents were absent from their homes and used the stolen data, such as full name, identity documents and social security number (CPF), to trick the condominium staff and gain free entry through the door [5].
• In 2010, a British security company conducted a survey among criminals in the UK, and a proportion of them revealed that they use open sources and social networks such as Twitter and Facebook to search for potential victims. Seventy percent of offenders revealed that they gather information about their victims' routines before committing a crime, regardless of the source of the information. Many stated that the level of exposure on social networks helped them identify the best time to act, as they could tell when homes would be empty. [6]
OSINT tools
It is natural for the careful reader to wonder how attackers have such easy access, where they are, and how it is possible to obtain so much information. Well, in a way it is quite simple. There are an almost infinite number of tools and websites for collecting personal data, in addition to people's own social networks. Below, we have listed some tools that help in the collection process and can help companies and individuals better understand the level of exposure they have. Obviously, tools help a lot in the collection, but some manual work is still necessary - you can't rely 100% on tools or automation.

Shodan(https://www.shodan.io/): Often referred to as the "Google of connected devices", it allows users to discover specific devices (such as cameras, routers and servers) connected to the Internet.
theHarvester: Information gathering tool that searches a variety of public sources to collect emails, names, subdomains, IPs and URLs. Available in Linux distributions focused on information security, such as Kali Linux and Parrot Security.
Maltego: a graphical application that provides a visualization of the relationships between data. It is widely used to analyze links and build relational maps, and is capable of displaying various data about a person and their relationships. It is also available in Linux distributions focused on information security.
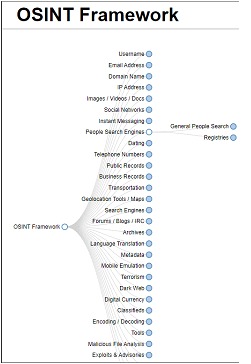
Marco OSINT (https://osintframework.com/): A browser-based visual tool to guide researchers through the OSINT resources available online, organized by category. The OSINT framework presents numerous searchable sources for usernames, email addresses, personal data search engines, phone numbers, geolocation and so on.
Google Dorks: This is not a tool, but a technique, extremely powerful by the way, that uses Google's advanced search operators to find specific information or vulnerabilities in websites.
Strategies to reduce risks
Now that we are familiar with the power and scope of OSINT, it is crucial to understand and reflect on how we can complicate the actions of a malicious actor rather than make it easier for them to do their job. The answer to this comes from the principle of minimum exposure, i.e. the less public data available, the lower the risk of malicious open source intelligence activities against an individual or organization.
Even job descriptions on professional social networks such as LinkedIn can give too much information to attackers. When advertising a vacancy, recruiters should avoid exposing names of technologies, devices and equipment, describing everything as generically as possible to prevent the attacker from mapping the infrastructure.
Of course, it is impossible to step back and completely eliminate the risk of data collection through OSINT, but with the right strategies it is possible to significantly reduce it. When employees share work-related information, they can inadvertently expose sensitive data, future plans, internal infrastructure and much more. Attackers can use this information for OSINT purposes, helping them plan more sophisticated and targeted attacks.
While the release of data is often unavoidable, there are approaches to limit exposure and strengthen defenses against those who might use this information against individuals and organizations, some of which are listed below.

• Online presence/attack surface analysis: Conduct regular audits to understand what is exposed online, find out how many and which assets are available for public access, versions of software, technologies, operating systems and the like that may be improperly available, and in addition to this, regular vulnerability scans and penetration testing.
• Access control, encryption and other technological measures.
• User training and responsible use of social networks: Social networks are an integral part of the lives of a large part of the population. For this reason, the line between what is personal and what is professional can often blur. Comments, check-ins and posts related to work or personal life, while seemingly harmless, can inadvertently reveal valuable information about an organization. Below is a sub-list of attitudes to avoid:
• The classic credential photos, as we already mentioned: they can contain personal information such as full name, employee registration, photo, position/function, and as if all that were not enough, it is still possible for the attacker to map the visual identity of the company and better formulate their social engineering strategies for a future attack, as well as enabling the "cloning" of the credential, which can be used for a physical intrusion into the organization's premises. In 2018, at a conference in the capital of Brazil, I heard from Kevin Mitnick himself that he had a box with countless cloned company badges, most of them obtained from photos on social media;
• Photos and videos revealing part of the company's routine, location/address, start and finish times and shift changes;
• Real-time location information;
• Pictures of computer screens or objects on the desktop that may reveal future plans, IP addresses, employee registration numbers, personal and financial data, application and system security settings, e-mail addresses, usernames, etc.
• Obviously, all the recommendations listed above also apply perfectly well to the personal lives of employees, and should be observed to prevent not only cyber-attacks and crimes, but also fraud and possible real and common crimes, as shown earlier in this publication.
• Information security policy: It is important that the organization takes some responsibility in this area and establishes rules on what employees can share online, as well as conducting regular training on the appropriate use of media.
• Detailed review of social media activity and personal online presence: Ideally, participation or use of social media should be avoided altogether, but as this may be impossible or even unacceptable, reviewing what is available, adjusting privacy settings and considering everything there as public information is crucial to reduce the risks of this information being used against one's assets [1].
Training focused on social media

The best way to avoid unnecessary exposure is through education and training. After all the above recommendations, many of them addressed to individuals, it is important to once again stress the role of organizations in raising awareness. Among other things, employees need to be trained:
• Recognize sensitive information and the importance of protecting it and avoiding excessive or unnecessary sharing.
• How to correctly configure the privacy settings of your accounts.
• Minimally understand the tactics that attackers can use to extract information, such as social engineering via email, SMS and phone calls.
• The importance of recognizing such activities and reporting them to the responsible department of the organization, or blocking/reporting them if the action is directed at the individual.
• ⦁ Spreading the acquired knowledge to people close to them in some way, as in the absence of information about an individual, the malicious actor can search social networks and information from family, friends and other types of relationships.
Well-trained employees, as well as being less susceptible to mistakes, can also act as the first line of protection, helping to detect, identify and report potential threats. Cybersecurity is not just about technology, but also about people and their practices, and this concept can easily be transposed to a personal life context, since, as explored through the examples above, the problems caused by unnecessary exposure transcend the online 'wall'.
Regulatory milestones

Obviously, individuals are not solely responsible for making the OSINT collection scenario so "dangerous" for themselves and for organizations. The way in which data has historically been collected, processed and stored has contributed greatly to bringing it to the level it is at today.
With this scenario in mind, where OSINT is becoming an increasingly powerful tool in the hands of malicious actors, laws such as the GDPR (General Data Protection Regulation of the European Union) emerge as a kind of regulatory response to these threats. These regulations set strict guidelines on how personal data should be collected, processed and stored in order to protect the privacy of individuals and limit the availability of sensitive information in public sources. Thus, by imposing liability and sanctions on organizations that fail to comply with these rules, such laws discourage careless dissemination of data and restrict the arsenal of information accessible to malicious OSINT activities.
Conclusion

OSINT is a dynamic and constantly evolving field. It is notoriously useful for a variety of well-intentioned and malicious applications that can cause harm to people, technologies and organizations. Protecting against the risks associated with OSINT requires a combination of awareness, education, strict policies and technological tools. Prevention is always the best medicine, and understanding the threats, knowing the risks and raising awareness is the first step towards effective defense.s
Once this conversation has taken place, it is possible to realize that it is relatively easy for a malicious actor to obtain information from public sources via OSINT. Open sources provide a treasure trove of information that can be exploited. So we should not make it too easy for them. By being aware and taking precautions with regard to our online behavior, we can make it more difficult for these actors to do their job and better protect our personal and organizational data.