We continue to pay particular attention to all the services that our IT assets provide to our internal network. The reality today is that Microsoft Windows and its Active Directory service is one of the main exponents of the market, although, as you may well know, it is not the only identity and object manager that exists on the market, but it is the most widely used in organizations, the Windows platform provides us with many attributes that offer us a forest of functions that in many cases leave us disoriented in front of so many configurations that we have to take care of. In order to raise awareness, we are going to list below the 10 recommendations that we consider the most useful to apply on our platform, so that we can better understand the security of our architecture day by day.
1- Protect identity and privilege.
In a world that has moved beyond the everyday office workplace to an access-from-anywhere model, identities have become a prime target for attackers, making them more vulnerable.
Today, they are a key focus for attackers seeking access to all types of environments. For this reason, it is a priority that identities have multiple layers of protection and that associated preventive measures are implemented.
Adequate identity protection requires the implementation of account and access management tools that apply the principle of least privilege.
A user should only have access to the specific data, applications and systems required for his or her role, no more and no less. The main tasks to be performed include the following:
Important points to focus on include the adoption of a hierarchical model for privileged access, following Microsoft's Privileged Access Strategy, which proposes the principles of Zero Trust, which means always applying the principle of least privilege when assigning permissions to users. This applies to both Active Directory roles and Azure Active Directory roles when it comes to cloud environments.
Azure RBAC can be used to manage access to resources in Azure. In addition, the cloud platform allows you to improve access security for privileged users by implementing the following solutions:
• Privileged Access Management (PAM)
• Just-in-time access (JIT)
• Privileged Identity Management (PIM)
These solutions provide a complete privileged access management program for both your traditional on-premises environment and your cloud environment. If you don't have privilege management tools, create a secondary account for these purposes and educate your users not to use the same passwords across accounts.
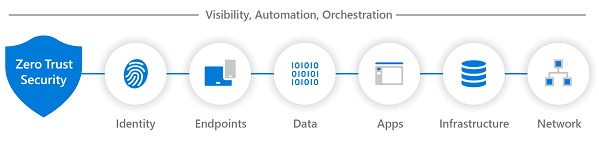
2- Implement a zero trust model
Ensure that we adopt a Zero Trust access architecture for your systems, identities, applications and infrastructure whenever and wherever applicable.
This is a model where we do not trust an identity until we can validate its origin and confirm its authorization. This approach requires a multi-layered access model that can evaluate different aspects of the authentication and authorization chain, from the network and firewall to the physical devices and the user's identity. Implementing cloud-based security technologies will help you significantly if you are looking to adopt a Zero Trust access model, as we have many tools that can seamlessly adapt to the way we currently manage.
Learn more about Microsoft's Zero Trust Access Model: https://docs.microsoft.com/en-us/security/zero-trust/
3- Define a security framework
The adoption of a security framework serves as the basis for your organization's security program. It should consist of recommendations from widely adopted frameworks, such as the following:
• Control Objectives for Information and Related Technology (COBIT): https://www.isaca.org/resources/cobit

• ISO (International Organization for Standardization) 27000:
https://www.iso.org/isoiec-27001-information-security.html
• NIST (National Institute of Standards and Technology) to Improve Critical Infrastructure Cybersecurity:
https://www.nist.gov/cyberframework
We also discuss the importance of well-documented policies, standards, procedures and guidelines as part of your security programme. The framework should consist of one or more security baselines that describe a minimum set of configurations for your devices. The security programme must be supported by senior management and promoted throughout the organization to educate users about the importance of security and the role they play.
4- Keeping up to date
It is important to keep abreast of new technologies in terms of the latest feature releases and security updates for your Windows clients and servers.
For example, applying a compliance assessment to ensure that your devices meet a minimum operating system build version is useful for identifying out-of-date devices that could be at risk. We can even apply additional security controls, such as requiring multifactor authentication through a conditional access policy, based on this compliance assessment.
Among the automated options we can find:
• Configuring Windows Update for Business (WufB) on Windows devices
• Configure Windows Server Update Services (WSUS) or Azure Update Management for Windows servers to keep your devices up to date.
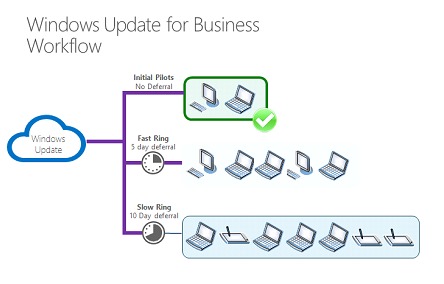
Paying special attention to updates will help ensure that devices are as protected as possible against ongoing threats. In addition to updating the Windows operating system, other enterprise applications such as Google Chrome, Microsoft Office and Adobe products must also be kept up to date as part of a proper patch management system. To plan ahead, third-party applications should be included in a continuous update strategy that can adapt to changes.
5- Use modern management tools
We need to use modern management tools to enforce security configurations and manage devices. Using enterprise-level solutions such as Microsoft Endpoint Configuration Manager and Intune, which can enforce security baselines, also highlights the ability to perform compliance assessments, deploy applications, apply device configurations and manage software updates.
In addition, tools such as Microsoft Deployment Toolkit (MDT) and Configuration Manager allow us to create hardened images and implement task sequences for upgrades or migrations related to application integrity changes.
Another important approach is to focus on reducing the number of tools where possible to avoid complexity in your environment. Simplicity with a reduced footprint helps reduce the number of vulnerabilities.

6- Certify the physical hardware
For physical endpoint devices and any physical servers in your environment, ensure that the hardware specifications comply with a hardware certification program and can support virtualization-based security features in the medium term.
In addition, ensure that there is a process for securely upgrading hardware and device firmware that is incorporated into documented baseline procedures. As a reminder, be sure to check the Windows Server Catalog and the Windows Hardware Compatibility List before purchasing hardware for your Windows operating systems using the links below:
• https://www.windowsservercatalog.com/
• https://partner.microsoft.com/en-us/dashboard/hardware/search/cpl
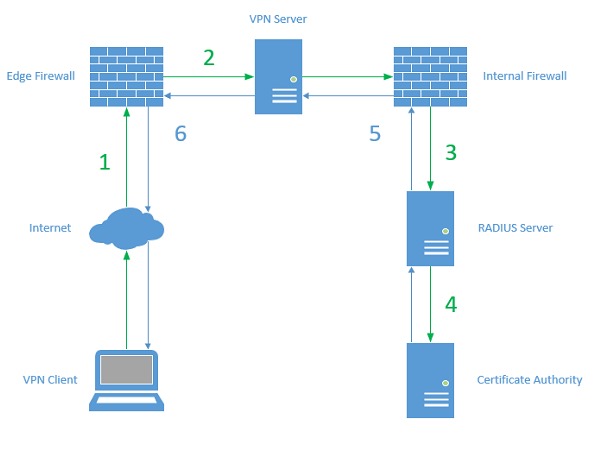
7 - Manage network security
While recent trends have focused on securing user devices and identities, network security continues to play a critical role. The role of network security should focus on network devices, physical offices and data centers, and include network-related configurations for end-user devices and servers. These configurations should be part of your documented security baselines and may include settings for software-based firewalls and VPNs.
For Windows devices, communications can be restricted by configuring the Windows Defender firewall using Group Policy, Intune, or Configuration Manager. Advanced network protection that blocks traffic to risky hosts or inappropriate websites can be added by deploying a proxy server or VPN, or by using advanced features of Microsoft Defender for Endpoint.
For servers running on Azure, a network security group can be applied to the subnet or network interface resource, allowing only necessary communications. As your users become more distributed, we must ensure the implementation of a reliable and secure VPN service, such as Microsoft's Always On VPN.
8- Always encrypt your devices
We should always require encryption for end-user devices and servers. This should include mobile devices that store corporate data or can be used to open corporate documents and email. For Windows clients, you can easily implement BitLocker disk encryption using Intune and Azure Active Directory, Configuration Manager, or Active Directory and Group Policies.
For virtual machines in Azure, use Azure Disk Encryption and Key Vault for key storage. Also, make sure backups are configured for critical systems.
Before making any encryption decisions, it may be useful to take a moment to think about what data is most important to the organization so that you can design your architecture around your organization's most important interests.
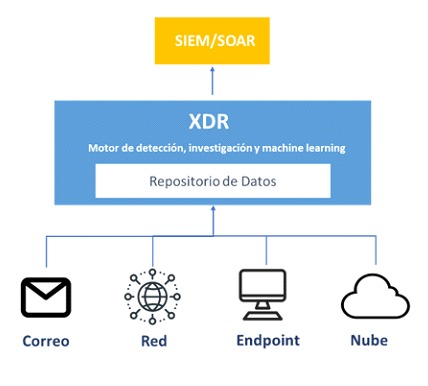
9- Enabling XDR protection beyond EDR
XDR is a highly valuable strategic approach to implement in your cybersecurity program. XDR goes beyond the original EDR capabilities, which focused primarily on a single technology, to bring together multiple technologies. This allows security teams to improve detection by adding context to alerts and seeing a complete picture of a potential attack (hence the term eXtended Detection and Response).
An XDR strategy combines capabilities that span endpoints, email, servers, cloud infrastructure, identity and access management, network and applications, and data. The key benefit of XDR is the consolidation of everything into a centralized view.
For EDR capabilities that have replaced the traditional antivirus model, be sure to integrate your workstations and servers with Microsoft Defender for Endpoint, which provides advanced endpoint protection with behavioral detection, cloud-based analytics, and threat intelligence.
10- Implement security monitoring solutions
Having the right security tools in place is a critical part of your security program, but if you don't have operations and monitoring in place, the value of your security tools is diminished. When you use Microsoft technologies, that means taking advantage of available XDR capabilities that enable immediate response and automated remediation of any incident detected in your environment. Leverage available enterprise-class security monitoring and reporting solutions, including Log Analytics, Microsoft Defender for Endpoint, Defender for Cloud Apps, Microsoft Defender for Cloud, and Microsoft Sentinel. Many of these solutions integrate with third-party SIEM tools for use in-house or in an outsourced security operations center.
Conclusion
Whether you have these technologies or not, it is important to know what vendors offer when designing a security architecture. Some say the tools make the master, but in practice this is not true. It is the abstraction of ideas that makes the difference between a good security architecture and a neglected one. As mentioned before, trying to have simple solutions helps us face all the difficulties that the Internet jungle throws at us on a daily basis. That, and only that, is where awareness makes the difference.