- Three Decades of Deception
Techniques in Active Cyber Defense
- Retrospect and Outlook (2021),
Li Zhang and Vrizlynn L. L. L. Thing
In previous posts we have introduced some cyber deception strategies, in this post we will summarize an article entitled "Three decades of deception techniques in active cyber defense: retrospective and perspectives" by Li Zhang and Vrizlynn L. L. L. Thing, which focuses on cyber deception techniques, specifically in the domains of honeypots, honeytokens and moving target defense. These techniques, which have evolved from the late 1980s to the present day, are still considered a game changer in cyber defense. From a systematic retrospective, the integrated use of these techniques for orchestrated deception is examined.
This paper posits an adapted Cyber Kill Chain model and a four-layer deception stack to develop a two-dimensional taxonomy. This classification answers which phases of a cyberattack campaign the techniques can disrupt, and to which layers of the deception stack they belong. Using this taxonomy as a reference can be a starting step to design an organized and comprehensive deception plan or to prioritize deception efforts considering the available budget.
In addition, two important points for achieving an active and resilient cyber defense are discussed: deception in depth and the deception life cycle, illustrating several notable proposals.
Finally, perspectives on future research directions are presented, including the dynamic integration of different deception techniques, the quantified effects of deception, the cost of deception operation, hardware-supported deception techniques, and techniques developed based on a better understanding of the human element.
Honeypots, Honeytokens and Moving Target Defense
From the late 1980s to the present, we have seen a significant evolution in defense strategies. Among these, honeypots, honeytokens and moving target defense are particularly notable for posing a different perspective.
These techniques not only complement each other, but also offer a multi-layered approach to cyber defense, which is essential for dealing with modern threats.
Honeypots
Just to be aligned, honeypots are decoy computer systems designed to be probed, attacked or compromised. They act as traps to detect unauthorized intrusion or scanning attempts. Several interconnected honeypots form a honeypot network, known as a honeynet. Their purpose is to present fake, multi-layered attack surfaces for intruders. However, honeypots, especially those with high interaction that provide a real operating system environment, can be exploited by intruders to gain privileged control and used as a pivot point to compromise other systems.
Honeytokens
Honeytokens are decoy resources that can take various forms, such as accounts, user files, database entries or passwords. They function similarly to honeypots, but are not limited to computer systems. For example, honeyfiles are fake files on a file server; when accessed, an alert is sent to indicate a possible intrusion. Unlike honeypots, which can generally only disrupt specific attack phases in the kill chain from the network and system layer, honeytokens can be applied to counter almost all attack phases across all four layers of the deception stack. One example is the Spacecrab Project, which creates credential honeytokens in the form of Amazon Web Services (AWS) keys, and found some cases where the average time for a hacker to exploit the honeytoken is only thirty minutes after being published on GitHub.
Moving Target Defense (Moving Target Defense)
"Moving target defense" is a defensive deception technique that succeeds in confusing and disorienting attackers by randomizing and reconfiguring networks, assets and defense tools. By dynamically changing both real and fake attack surfaces, the attack surfaces of critical assets can be obfuscated to the maximum extent possible, keeping the attacker in a continuous state of confusion and deception. This technique was identified as a key research and development topic in cybersecurity by the U.S. NITRD Program.
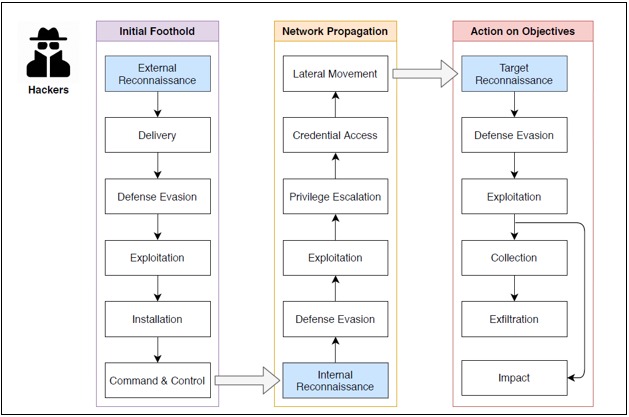
Cyber Kill Chain grouped
The authors propose a Cyber Kill Chain model that significantly expands the Lockheed Martin model. It is divided into three specific "sub-chains", addressing different phases of a cyber-attack:
External Chain: Focuses on establishing an initial foothold in the target system or network. It includes phases such as external reconnaissance, malware delivery, and the creation of a foothold.
Internal Chain: Focuses on propagation within the victim's network. This sub-chain includes lateral movement (the ability of an attacker to move through a network once he has gained access), access to credentials, and defense evasion.
Actions on the target: This chain aims to manipulate the target system to achieve the objectives of the attack. It includes phases such as data collection, installation of malicious elements, defense evasion, exfiltration (extraction of data from the victim's network), command and control, and finally, internal reconnaissance.
Each of these sub-chains provides a detailed framework for understanding how cyberattacks unfold and offers cyber defender's guidance for developing defense strategies against these threats
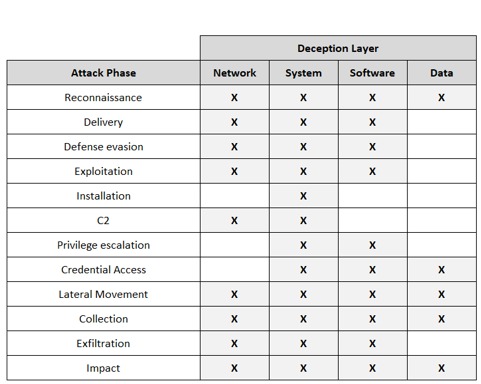
To facilitate the coordinated selection and deployment of deception techniques, honeypot, honeytoken and MTD techniques can be assigned to a particular attack phase and based on the characteristics of each unique attack phase, what are the possible layers of deception, in which the specific attack phase can be disrupted.
"Layers of deception" refers to a framework of typically used deception techniques.
Network layer: Includes techniques such as the use of "decoy traffic" to induce attackers to take observable actions, such as using captured credentials to access a decoy account. Methods such as "record, modify and replay" are employed to automatically generate a large amount of decoy traffic and keep it up to date.
System layer: Focuses, for example, on IP and operating system (OS) obfuscation. In the IP obfuscation technique, attackers are prevented from tracking hosts in the target network based on IP addresses, using methods such as dynamic network address translation (DyNAT) and OpenFlow host random mutation (OF-RHM). OS obfuscation is performed to defend against OS fingerprinting attacks, randomized TCP number sequences and patterns in various protocols.
Software Layer: Includes tactics such as layout randomization (ASLR), which makes it difficult to exploit memory corruption vulnerabilities by randomizing the memory addresses of loaded software, and instruction set randomization (ISR) to address code injection attacks. Software diversity approaches are also used, such as "Marlin", which breaks a software binary into function blocks and randomly shuffles the order.
Data Layer: Employs techniques such as multipath routing strategy to frequently modify communication paths between devices, and self-protected dynamic network architecture (SDNA), which rewrites traffic to hide the identities of the sender and receiver. Dynamic data approaches, such as partitioning cryptographic keys into random shares to prevent side-channel attacks between virtual machines (VMs), are also used.
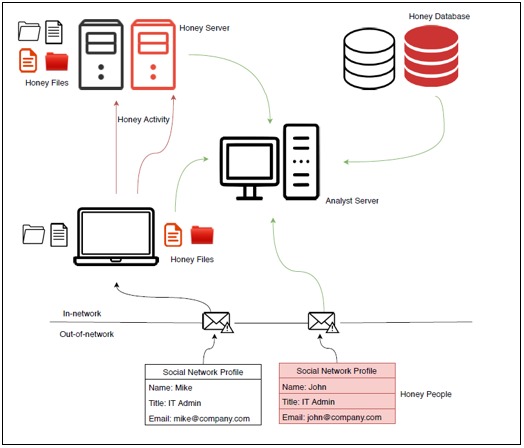
In addition, strategies are defined according to the objectives of each element in the cyberdeception operation:
- Lamb: An isolated system that has no point of entry to production systems.
- Zoo: A complete subnetwork of honeypots with various platforms, services, vulnerabilities and configurations, which are isolated from production systems.
- Minefield: Several honeypots placed in the front line to serve as first strike targets.
- Proximity Lures: Honeypots deployed in proximity to production systems.
- Redirect Shield: External honeypots that appear on production systems through port forwarding.
- Spoofing Ports: Simulated services (e.g., SMTP, DNS, FTP) on production systems.
In addition to these main layers and strategies, the article addresses the need to integrate and coordinate these techniques to create a holistic deception fabric that covers the protected network and forms a complete illusion for the adversary.
Conclusions
Beyond the techniques individually used for each stage of the attack, emphasis is placed on the importance of a well-managed deception lifecycle to ensure the effectiveness of these tactics over time, adapting to changes in the environment and the attacker's behavior.
It is also discussed how the application of game theory and machine learning can enhance the interaction of deception techniques with the adversary.
In summary, the "Deception Layers" represent a multidimensional and stratified approach to cyber defense, encompassing varied tactics across different layers of the IT infrastructure, from the network to the data, to deceive, disorient, and defend against attackers.
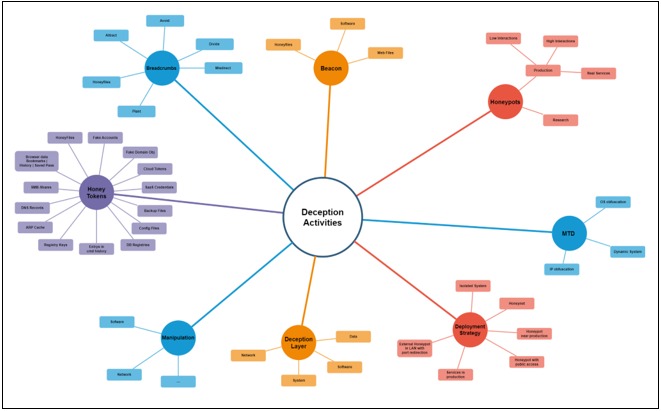
To conclude, we share a brief map of the various strategies and elements that can be part of a cyber deception operation: